Preface: Who cares about spending all your money, maybe just yourself! Who cares about running out of your system resources, perhaps it is the system owner.
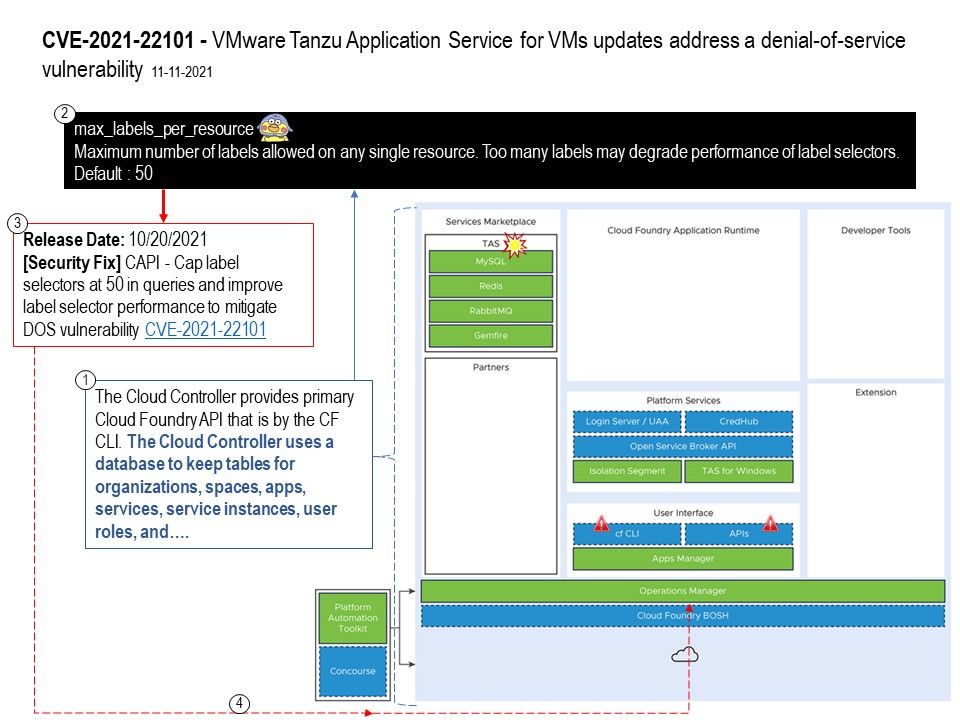
Background: VMware Tanzu Application Service is a modern application platform for enterprises that want to continuously deliver and run microservices across clouds. Release new features and updates to production daily. across clouds. Apply security patches and platform updates with near zero downtime.
A REST call requires the creation of a resource handler.
The resource handler represents the entry point for resource requests and is annotated with the @Path, context, and other information that is required to handle a request. Handlers are responsible for coordinating the client request. Handlers intercept calls, run required actions, and convert responses to a form consumable by the client by using standard
HTTP protocol elements.
Vulnerability Details: A denial-of-service vulnerability was found in one of the components of VMware (Tanzu Application Service for VM). Cloud Controller versions prior to 1.118.0 are vulnerable to unauthenticated denial of Service(DoS) vulnerability. The remote attacker can leverage this vulnerability to cause denial of service by using REST HTTP requests and generating an enormous SQL query leading to database (ccdb) unavailability.
Note: The design weakness notified by the supplier on manual before CVE record happens: (max_labels_per_resource) – Maximum number of labels allowed on any single resource. Too many labels may degrade performance of label selectors.
Default : 50
Remediation: upgrade to 2.12.1 (Release Date: 10/20/2021)
[Security Fix] CAPI – Cap label selectors at 50 in queries and improve label selector performance to mitigate DOS vulnerability (CVE-2021-22101) – https://www.vmware.com/security/advisories/VMSA-2021-0026.html