Preface: Every Windows system is vulnerable to a particular NTLM relay attack that could allow attackers to escalate privileges from User to Domain Admin.
Background: If your administration portal is a web application which protected by IWA (Integrated Windows Authentication). When client send a request to web server doing handshaking, the web server will be rejected the request and sends a response saying the user needs to be authenticated using NTLM. NTLM relaying is a well known technique that has long been abused by attackers.
Normally, NTLM relays need user intervention, so you have to trick the victim to authenticate to a resource under your control.
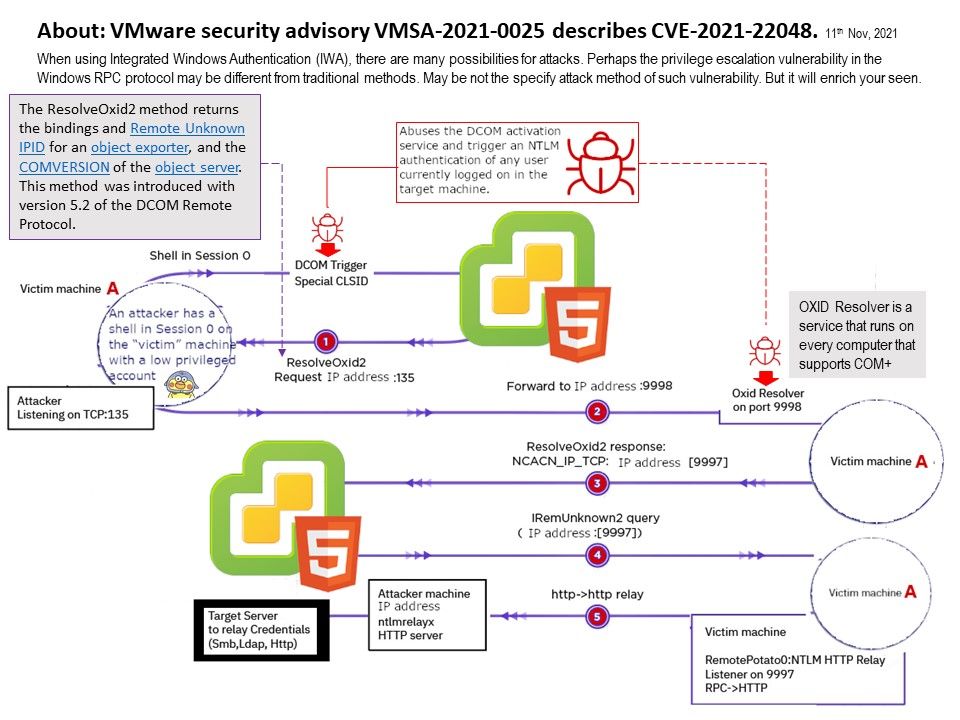
Vulnerability details: When using Integrated Windows Authentication (IWA), there are many possibilities for attacks. Perhaps the privilege escalation vulnerability in the Windows RPC protocol may be different from traditional methods. May be not the specify attack method of such vulnerability. But it will enrich your seen.
VMware vCenter Server IWA privilege escalation vulnerability (CVE-2021-22048): The vCenter Server contains a privilege escalation vulnerability in the IWA (Integrated Windows Authentication) authentication mechanism. The attacker with non-administrative access to vCenter Server may exploit this issue to elevate privileges to a higher privileged group. US Homeland secuirty (CISA) encourages users and administrators to review VMware Security Advisory – https://www.vmware.com/security/advisories/VMSA-2021-0025.html
Workaround Instructions for CVE-2021-22048 – https://kb.vmware.com/s/article/86292