Preface: Long time ago, digital world try to avoid malware infection. Malware has few different types. Memory-resident malware, also known as fileless malware, is a type of malicious software that writes itself directly onto a computer’s system memory. This behavior leaves very few signs of infection, making it difficult for traditional tools and non-experts to identify. Therefore software engineer invented ASLR to fight against them. Apart from that the public announcement said, 64 bit software OS contained anti-malware function. So people are imagine that our digital is secure forever.
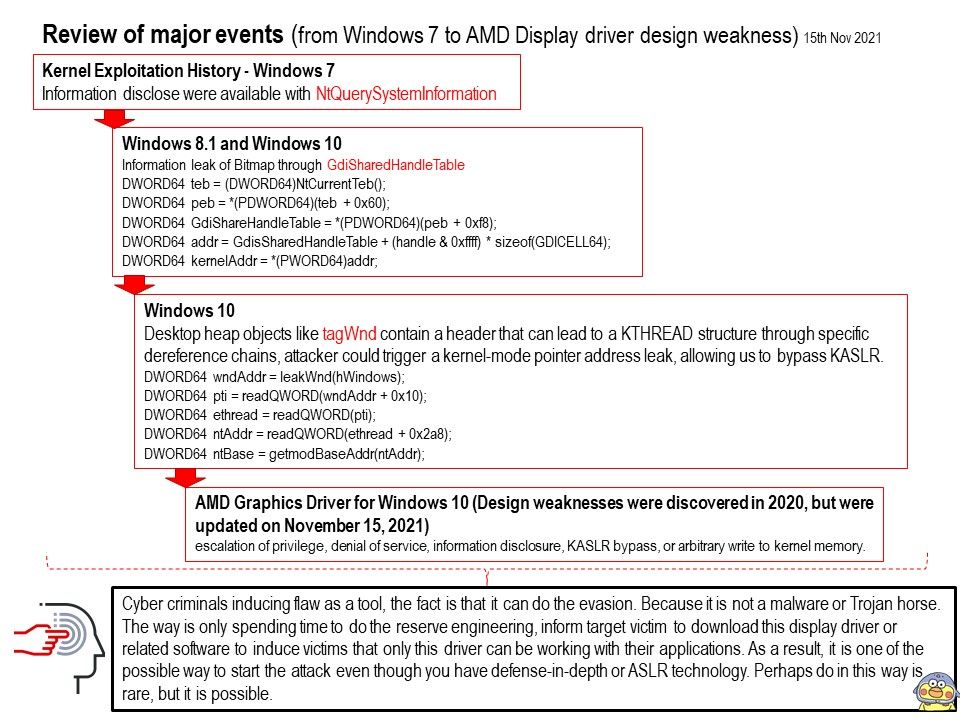
Situation in the past ten years: The NTQuerySystemInformation function is implemented on NTDLL. And as a kernel API, it is always updated in the Windows version without any notice. The software developers revealed the reality afterwards. KASLR can be trivially bypassed by an exploit executed at medium-integrity through the use of the well-known EnumDeviceDrivers and NtQuerySystemInformation APIs. As such, NtQuerySystemInformation may be altered or unavailable in future versions of Windows. Perhaps it should use the other functions for replacement. But how about the EnumDeviceDrivers ?
Remark (1): EnumDeviceDrivers – Retrieves the load address for each device driver in the system. i.e. It enums already loaded device drivers.
A story can tell: In Windows 10 Redstone 2 (2017), the UserHandleTable containing the kernel-mode address of all objects allocated on the Desktop heap was removed, however the Desktop heap itself was still mapped in user-mode, allowing us to search through it and locate a specific object. Attacker can creating a window through the CreateWindowEx API, grabbing the address of the user-mode mapped Desktop heap from offset in the TEB, and performing a brute-force search for the Window handle on the user-mode mapped Desktop heap to obtain the offset. It sound likes bypass Kernel ASLR.
Remark (2): Every desktop object requires memory to store UI objects, such as windows and menus. This memory is called desktop heap.
When applications require a UI object, functions within user32. dll are called, and desktop heap memory is allocated.
Remark (3): Remark: TEB(winternl.h) – Win32 apps – The Threat Environment Block (TEB structure) describes the state of a thread.
Summary: In analysis of the AMD Escape calls, a potential set of weaknesses in several APIs was discovered, which could result in escalation of privilege, denial of service, information disclosure, KASLR bypass, or arbitrary write to kernel memory. Please refer to the link – https://web.archive.org/web/20211113054717/https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1000