Preface: Don’t underestimate the vulnerabilities discovered in the past, it will cause trouble for your cloud or system.
Background: VMware vCloud Director is a management tool for private and hybrid cloud architectures. Top Industries that use VMware vCloud Director are Financial Services, Insurance Program Managers Group, & business technology services provider.
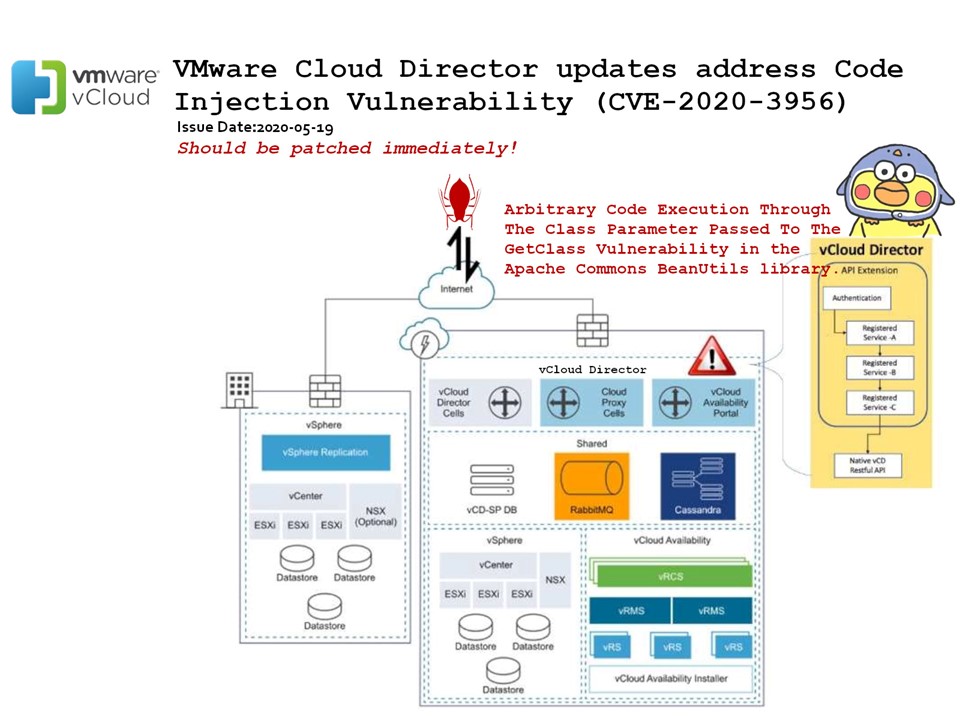
Vulnerability details: VMware officially announced on May 19, 2020. Suppliers urge customers to immediately repair or apply workarounds. The details of the vulnerability pointed out by the vendor is a code injection vulnerability in VMware Cloud Director. The product failed to properly handle the input that led to the code injection vulnerability. For more details, please refer to following url: https://www.vmware.com/security/advisories/VMSA-2020-0010.html
Our observation: With reference to the workaround provided by vendor. The hints of JAR file (org.apache.bval.bundle) and ELF Class can tell us that hacker is able to conduct the arbitrary code execution through the Class Parameter passed To the GetClass vulnerability in the Apache Commons BeanUtils library. And therefore we suggest to do the patching immediately. For more details, please refer to following url: https://kb.vmware.com/s/article/79091