Preface: For security reasons, SAP will not disclose the details of the vulnerability. Security bulletin issued yesterday. However, the end user only needs to tinker. But we don’t know what happened? So my purpose of this topic is to try to dig out details an interest that appeals to you. If , my findings didn’t precise find the reason of this vulnerability. No worries. Since, the weaknesses in client-side JavaScript security in SAPUI5 applications may be ubiquitous. It is easily find the details somewhere.
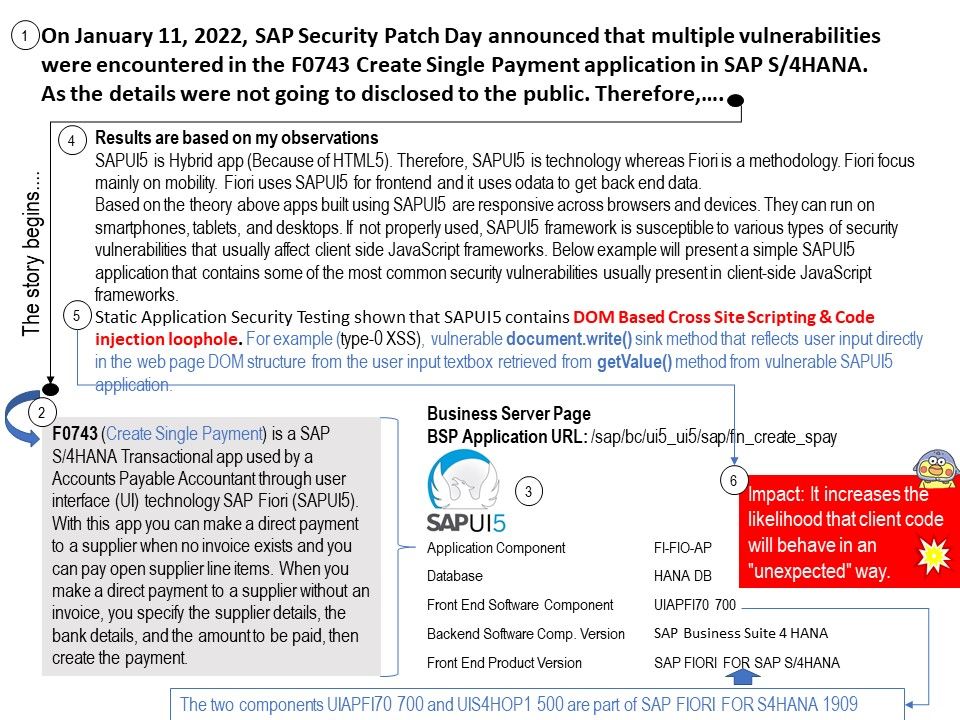
Background: F0743 (Create Single Payment) is a SAP S/4HANA Transactional app used by a Accounts Payable Accountant through user interface (UI) technology SAP Fiori (SAPUI5). With this app you can make a direct payment to a supplier when no invoice exists and you can pay open supplier line items. When you make a direct payment to a supplier without an invoice, you specify the supplier details, the bank details, and the amount to be paid, then create the payment.
Vulnerability details: Official announcement stated that Multiple vulnerabilities in F0743 Create Single Payment application of SAP S/4HANA.
Results are based on my observations: SAPUI5 is Hybrid app (Because of HTML5). Therefore, SAPUI5 is technology whereas Fiori is a methodology. Fiori focus mainly on mobility. Fiori uses SAPUI5 for frontend and it uses odata to get back end data. Based on the theory above apps built using SAPUI5 are responsive across browsers and devices. They can run on smartphones, tablets, and desktops.If not properly used, SAPUI5 framework is susceptible to various types of security vulnerabilities that usually affect client side JavaScript frameworks.
Static Application Security Testing shown that SAPUI5 contains DOM Based Cross Site Scripting & Code injection loophole. For example (type-0 XSS), vulnerable document.write() sink method that reflects user input directly in the web page DOM structure from the user input textbox retrieved from getValue() method from vulnerable SAPUI5 application.
Impact: It increases the likelihood that client code will behave in an “unexpected” way.
Official announcement: Please refer to the link – https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=596902035