Preface: HTTP[.]sys is mature technology that protects against many types of attacks and provides the robustness, security, and scalability of a full-featured web server. IIS itself runs as an HTTP listener on top of HTTP[.]sys.
Background: HTTP/1.1 specifies that a response sent as Transfer-Encoding: chunked can include optional trailers (ie. what would normally be sent as headers, but for whatever reason can’t be calculated before the content, so they can be appended to the end).
The http 1.1 specification, which lays out how chunking works. Specifically section 3.6.1.
The chunked encoding modifies the body of a message in order to transfer it as a series of chunks, each with its own size indicator, followed by an OPTIONAL trailer containing entity-header fields. This allows dynamically produced content to be transferred along with the information necessary for the recipient to verify that it has received the full message.
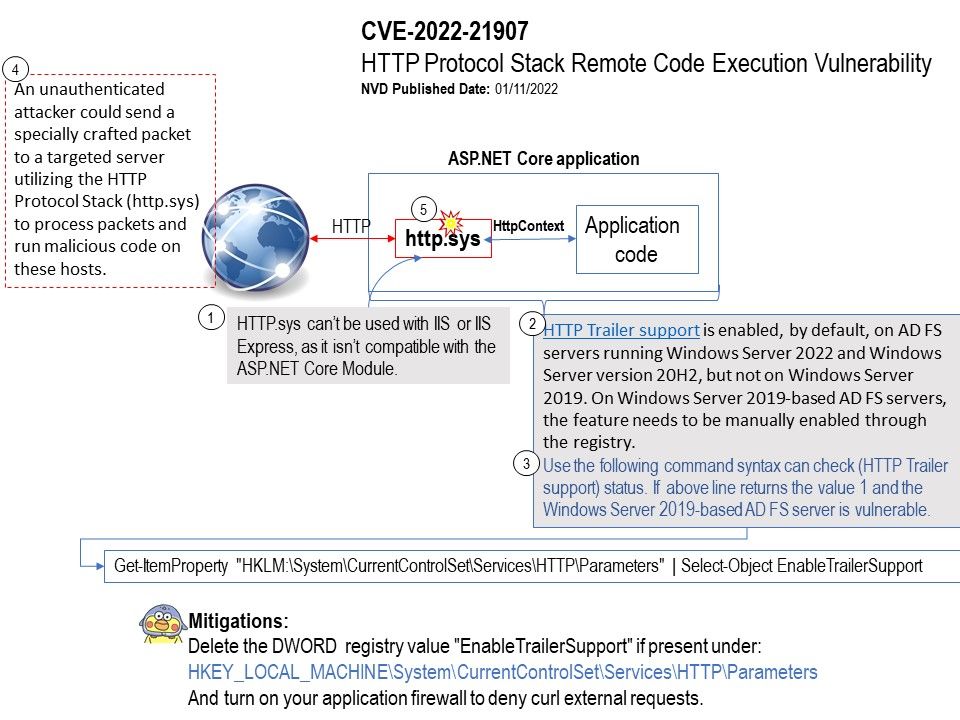
Vulnerability details: This vulnerability can be exploited by sending specially crafted packets to exploit the HTTP protocol stack to launch an attack. In view of the high harm of this vulnerability.
Ref (1): The HTTP Trailer response header allows the sender to include additional fields at the end of chunked messages in order to supply metadata that might be dynamically generated while the message body is sent. No package install is needed if you use the (xref:)Microsoft[.]AspNetCore[.]All metapackage.
The Microsoft[.]AspNetCore[.]Server[.]HttpSys package is included in the metapackage.
Ref (2): Call the UseHttpSys extension method on WebHostBuilder in your Main method, specifying any HTTP[.]sys options that you need.
Mitigations: Please refer to the link – https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-21907