Preface: Privilege escalation attacks can be separated into two way. It is horizontal privilege escalation and vertical privilege escalation. Privilege escalation happens when a malicious user exploits a bug, design flaw, or configuration error in an application or operating system to gain elevated access to resources that should normally be unavailable to them.
Background: Starting with 2109 version, Citrix Workspace app introduces an option to append the User-Agent strings in the network request and identify the source of a network request. Based on this User-Agent strings request, you can decide how to manage your network request.
For version 2108, the app protection feature is now fully functional. The app protection feature supports apps and desktop sessions and is enabled by default. However, you must configure the app protection feature in the AuthManConfig.xml file to enable it for the authentication manager and the Self-Service plug-in interfaces.
Vulnerability details: A vulnerability has been identified in Citrix Workspace app for Linux that could result in a local user elevating their privilege level to root on the computer running Citrix Workspace app for Linux.
This vulnerability only affects Citrix Workspace app for Linux 2012 – 2111 and only exists if App Protection was installed as part of Citrix Workspace app for Linux. This vulnerability does not exist if App Protection is not installed.
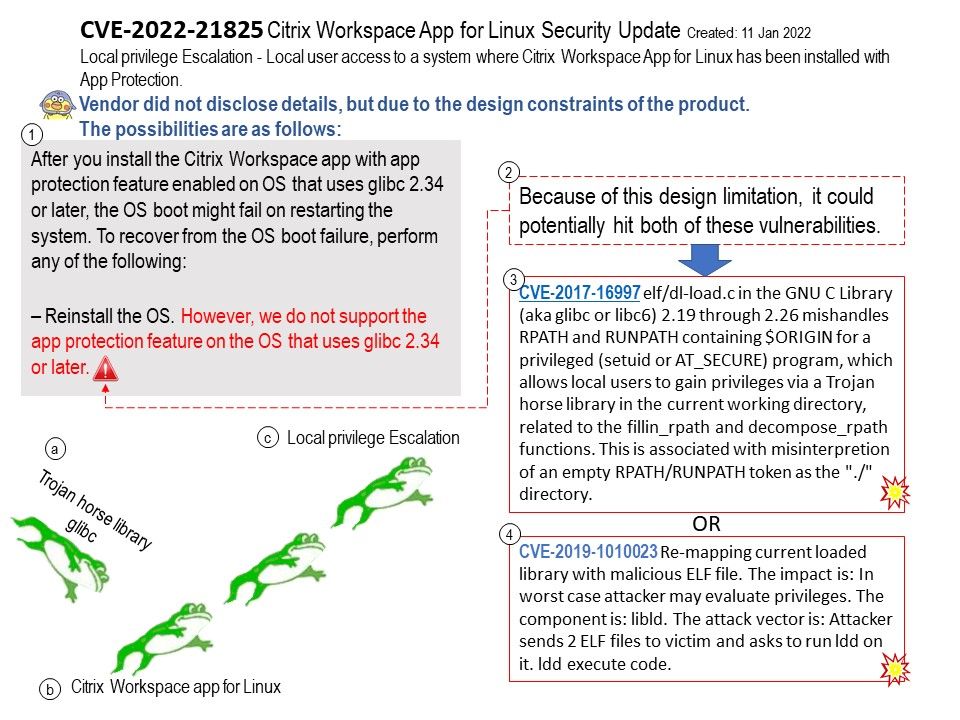
My observation: Vendor did not disclose details, but due to the design constraints of the product. The vulnerable version of glibc might have possibilities to trigger the design weakness. Because workspace app for Linux (has been installed with App Protection) do not support the app protection feature on the OS that uses glibc 2.34 or later. For more details, please refer to attached diagram.
Official announcement: Please refer to the link –