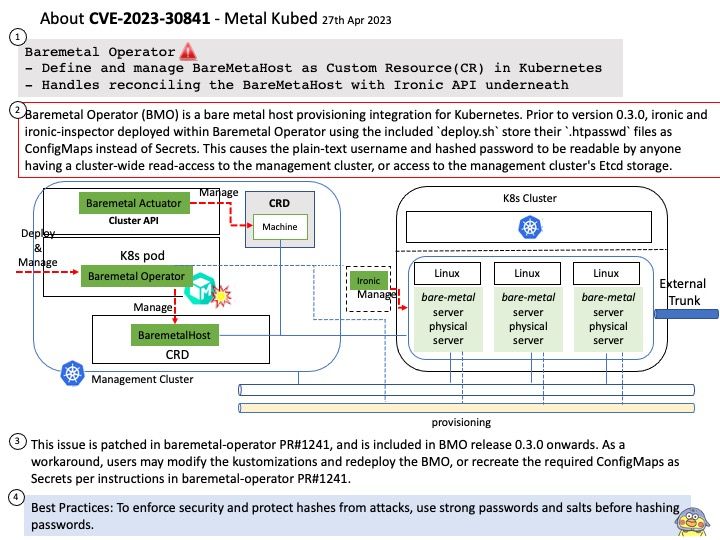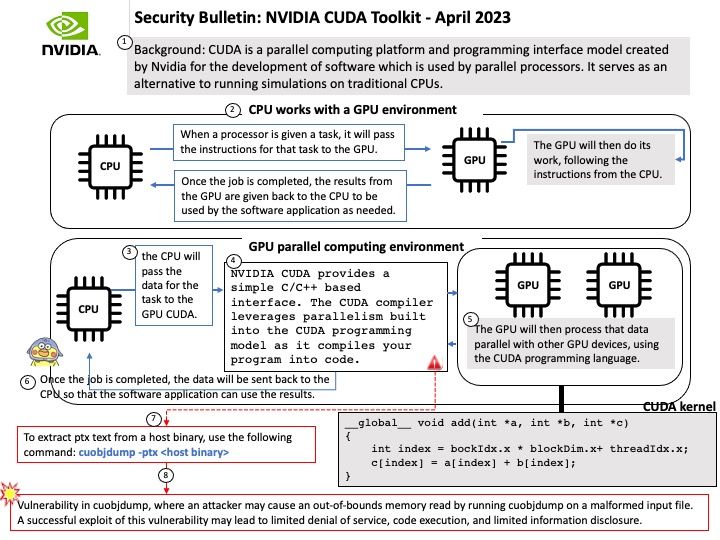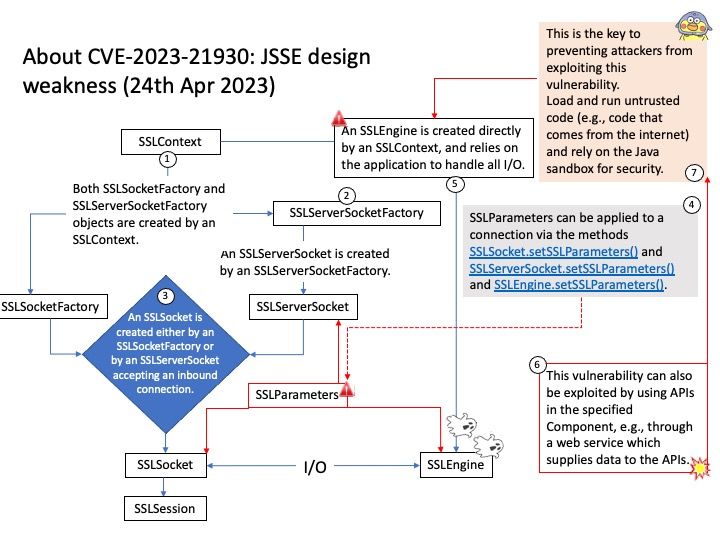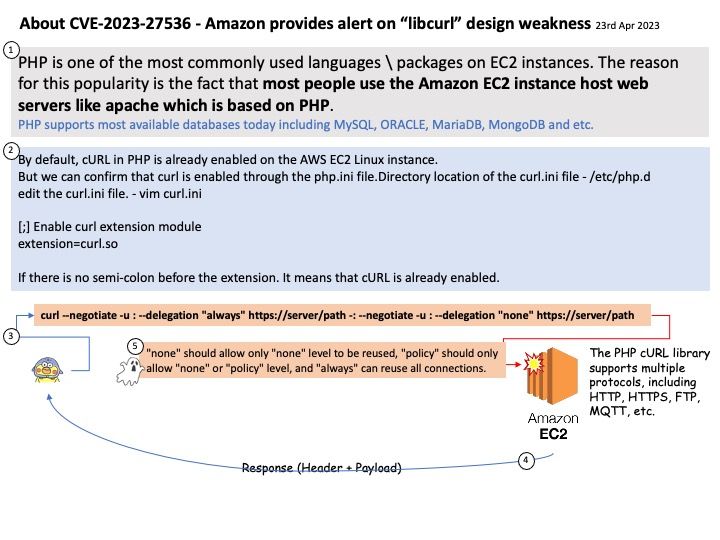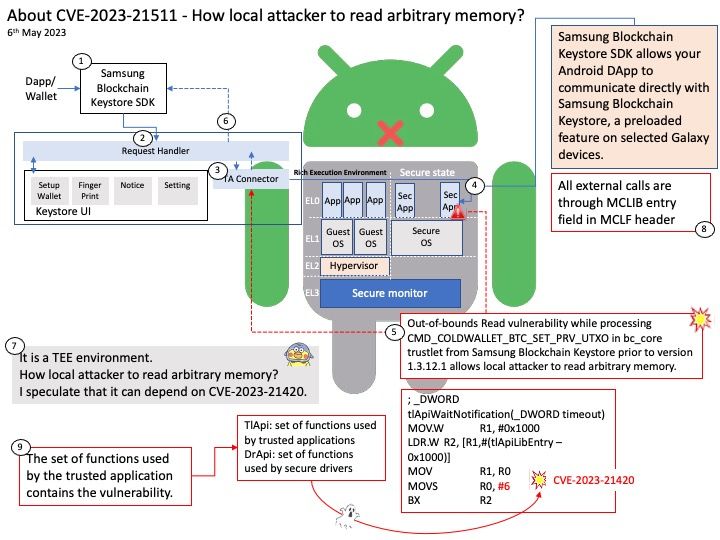
Preface: TEE is an area on the chipset that works like a TPM, but is not physically isolated from the rest of the chip.
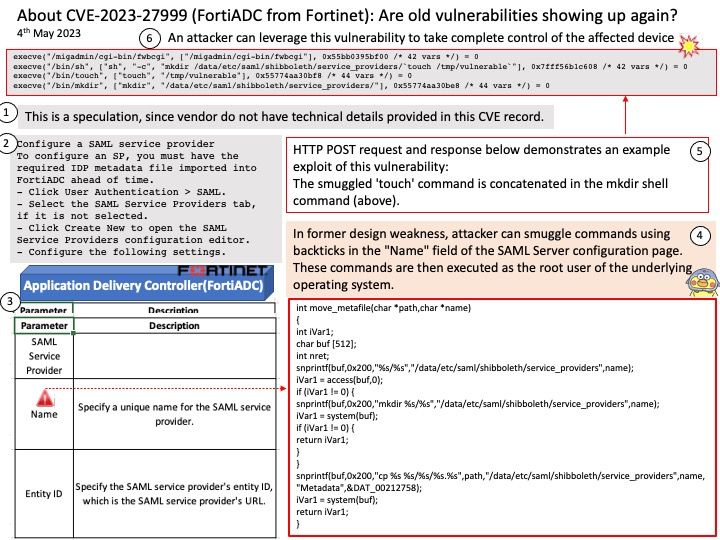
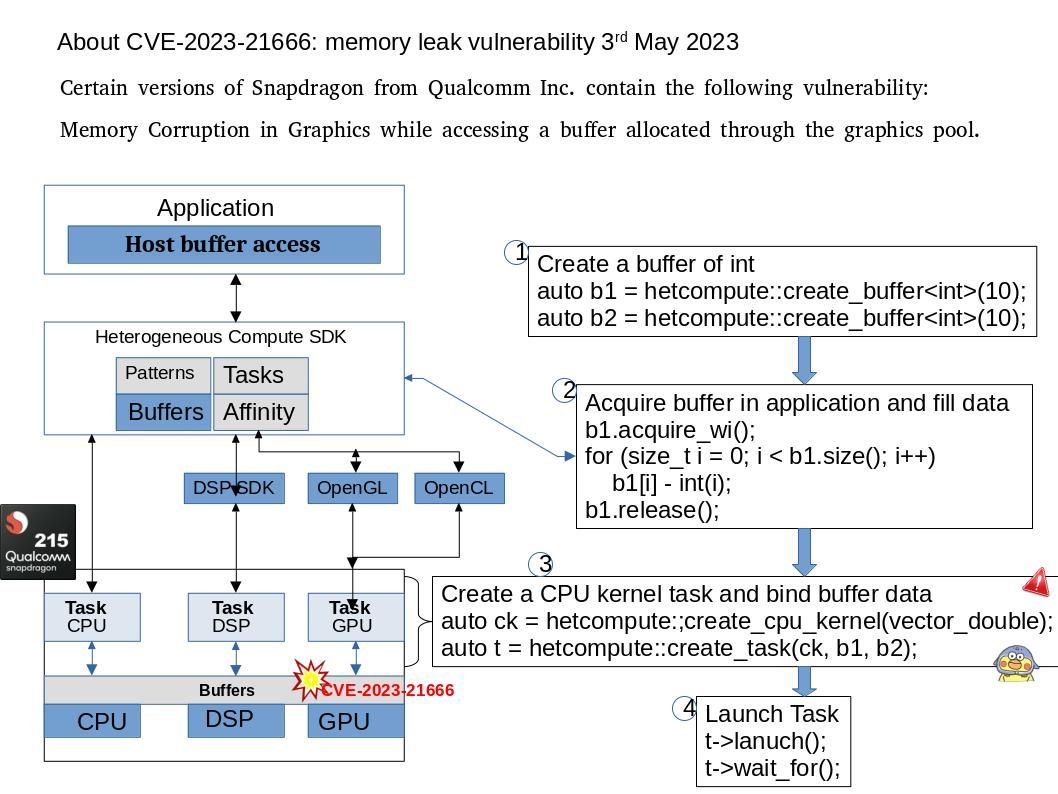
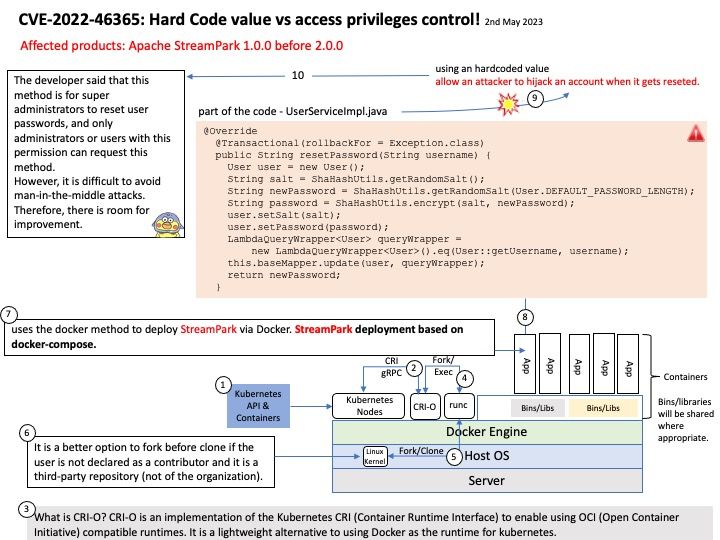
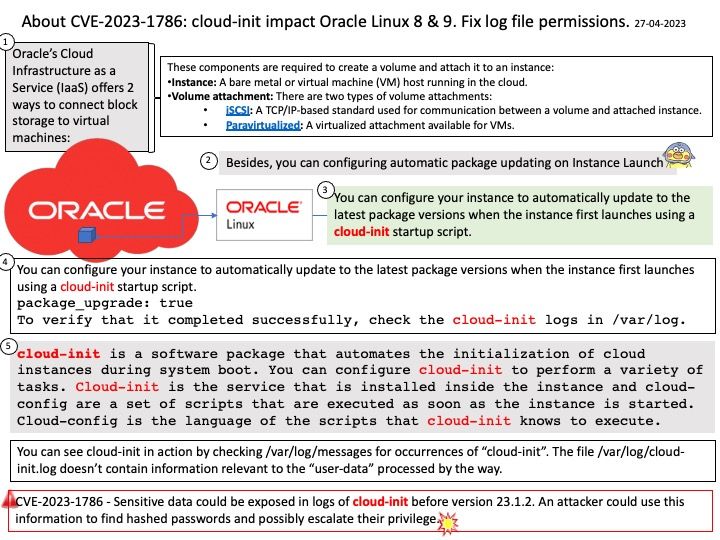
Background: The Trusted Execution Environment (TEE) is a secure area within the main processor. As an isolation environment, it ensures that the code and data loaded in the TEE are protected from software attacks and vulnerabilities in the Rich Execution Environment (REE).
How Samsung Blockchain Keystore leverages TEE? Samsung Blockchain Keystore SDK allows your Android DApp to communicate directly with Samsung Blockchain Keystore, a preloaded feature on selected Galaxy devices.
Developers can use an API provided by the Samsung Blockchain Keystore to check if a user is ready to use Samsung Blockchain Keystore. If the user has not created a wallet yet, developers can direct the user to create a new wallet to leverage Samsung Blockchain Keystore features.
Vulnerability details: Out-of-bounds Read vulnerability while processing CMD_COLDWALLET_BTC_SET_PRV_UTXO in bc_core trustlet from Samsung Blockchain Keystore prior to version 1.3.12.1 allows local attacker to read arbitrary memory.
Official announcement: For details, please refer to the link – https://security.samsungmobile.com/serviceWeb.smsb?year=2023&month=05