Preface: The Ryzen 7000 desktop and laptop chips were introduced in 2023. Alongside the main x86 CPU, Ryzen 7000 has a new type of coprocessor, a Neural Processing Unit (NPU), based on the XDNA™ AI Engine architecture. This new NPU is called Ryzen AI.
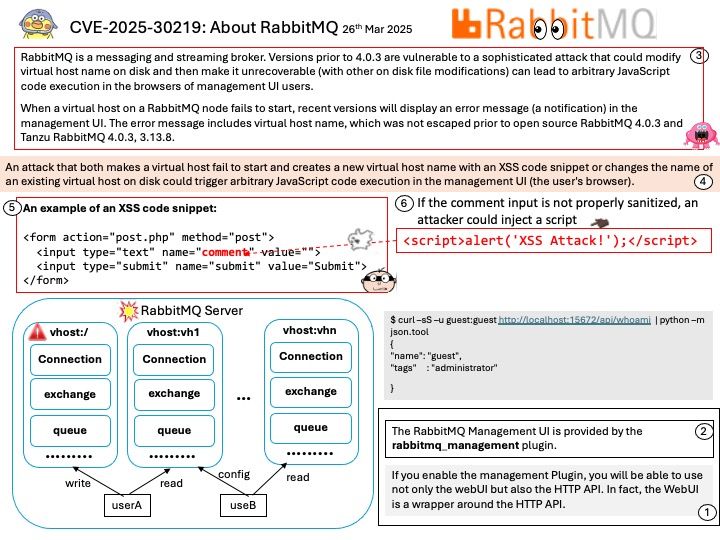
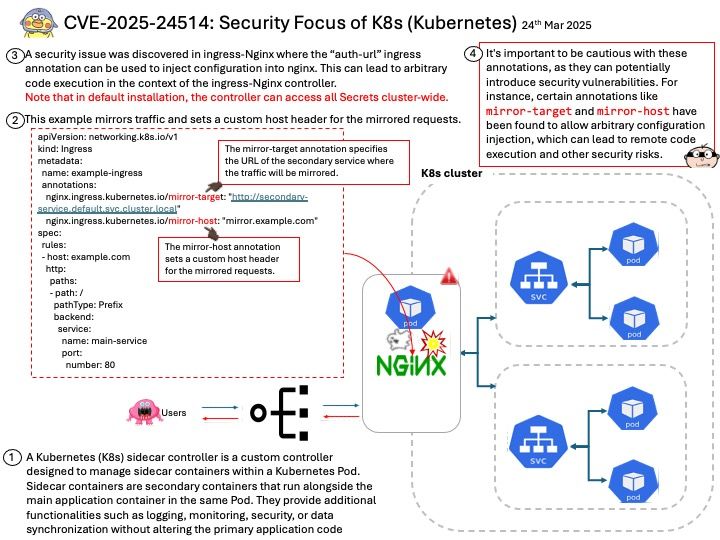
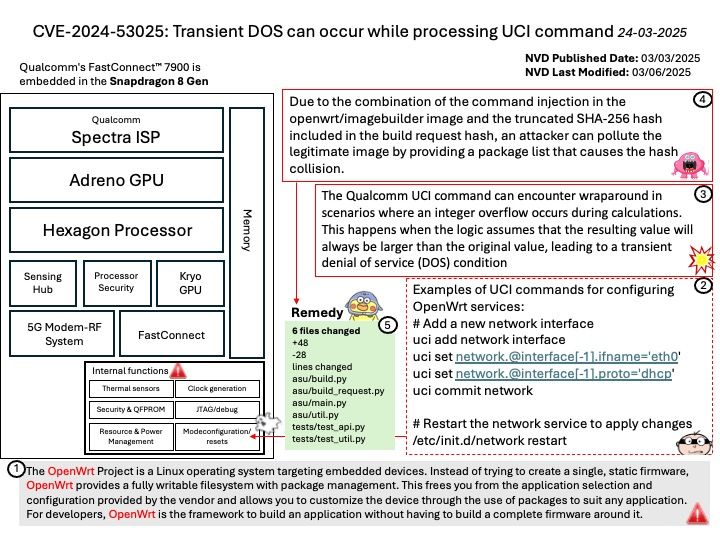
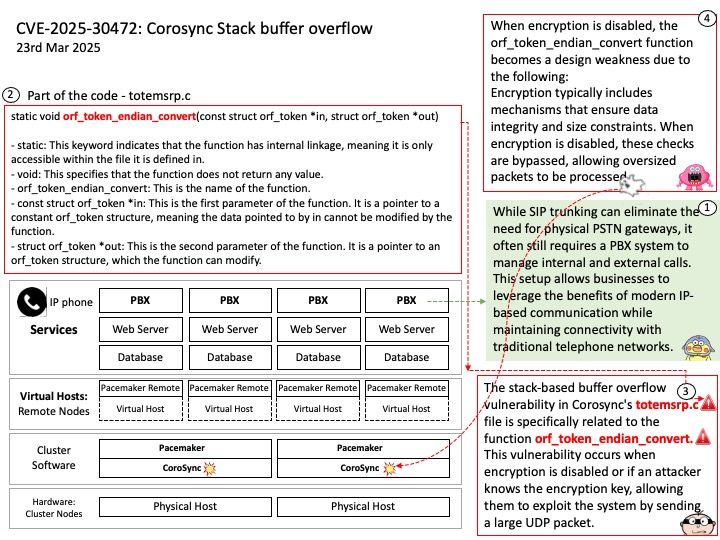
Background:
1.Install NPU Drivers
2.Download the NPU driver installation package NPU Driver
3.Install the NPU drivers by following these steps:
4.Extract the downloaded “NPU_RAI1.2.zip” zip file.
5.Open a terminal in administrator mode and execute the [[.]\npu_sw_installer[.]exe] exe file.
6.Ensure that NPU MCDM driver (Version:32.0.201.204, Date:7/26/2024) is correctly installed by opening Device Manager -> Neural processors -> NPU Compute Accelerator Device.
Vulnerability details:
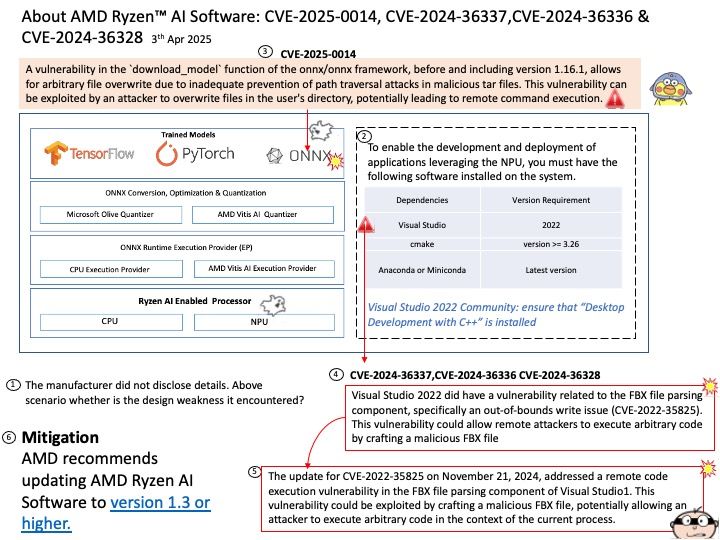
CVE-2025-0014: Incorrect default permissions on the AMD Ryzen™ AI installation folder could allow an attacker to achieve privilege escalation, potentially resulting in arbitrary code execution.
CVE-2024-36337: nteger overflow within AMD NPU Driver could allow a local attacker to write out of bounds, potentially leading to loss of confidentiality, integrity or availability.
CVE-2024-36328: nteger overflow within AMD NPU Driver could allow a local attacker to write out of bounds, potentially leading to loss of integrity or availability.
CVE-2024-36336: nteger overflow within the AMD NPU Driver could allow a local attacker to write out of bounds, potentially leading to a loss of confidentiality, integrity, or availability.
Official announcement: Please refer to the official announcement for details – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-7037.html