Preface: If you recall, programming in Java was involved in the field of network security ten years ago, because many serious incidents were caused by Java applications. Over time, the Java sandbox and secure programming techniques temporarily calmed the field. However, there was no long-term peace.
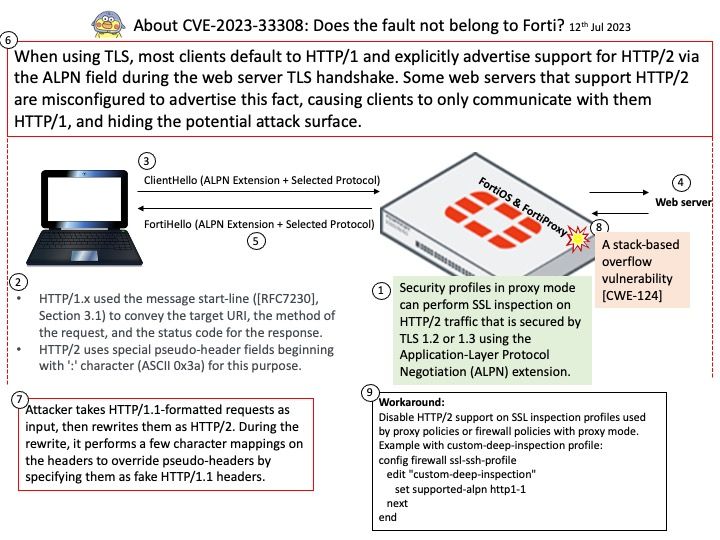
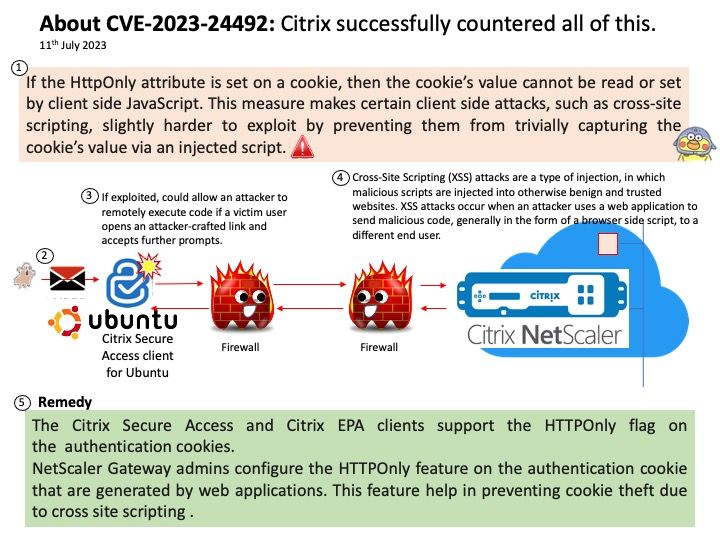
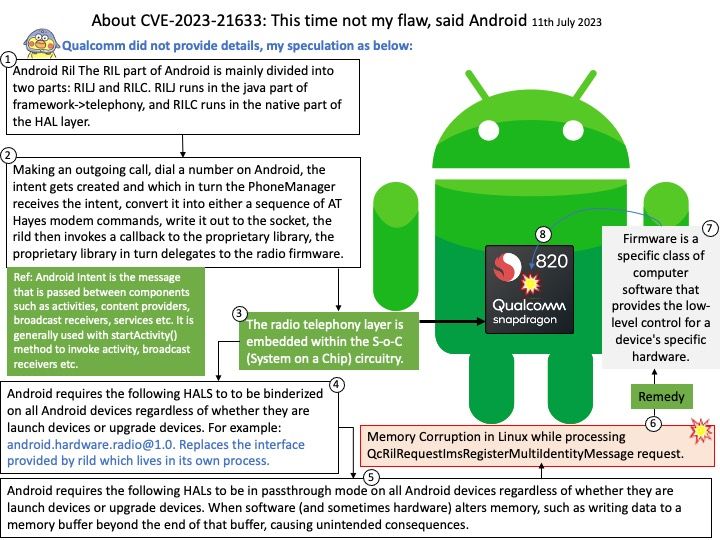
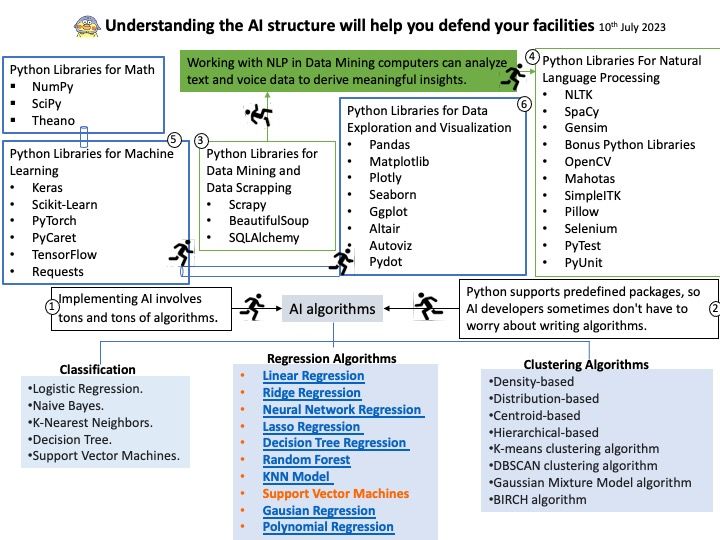
Background: vm2 is a sandbox that can run untrusted code with whitelisted Node’s built-in modules. It specialized JavaScript sandbox used by a broad range of software tools for running and testing untrusted code in an isolated environment, preventing the code from accessing the host’s system resources or external data.
Vulnerability details: The library contains critical security issues and should not be used for production. The maintenance of the project has been discontinued. In vm2 for versions up to 3.9.19, Promise handler sanitization can be bypassed with @@species accessor property allowing attackers to escape the sandbox and run arbitrary code. Remote Code Execution, assuming the attacker has arbitrary code execution primitive inside the context of vm2 sandbox.
Ref: A Node[.]js Promise is a placeholder for a value that will be available in the future, allowing us to handle the result of an asynchronous task once it has completed or encountered an error. Promises make writing asynchronous code easier. They’re an improvement on the callback pattern and very popular in Node[.]js.
Ref: The Proxy object allows you to create an object that can be used in place of the original object, but which may redefine fundamental Object operations like getting, setting, and defining properties. Proxy objects are commonly used to log property accesses, validate, format, or sanitize inputs, and so on.
Official announcement: For details, please refer to the link – https://www.tenable.com/cve/CVE-2023-37466