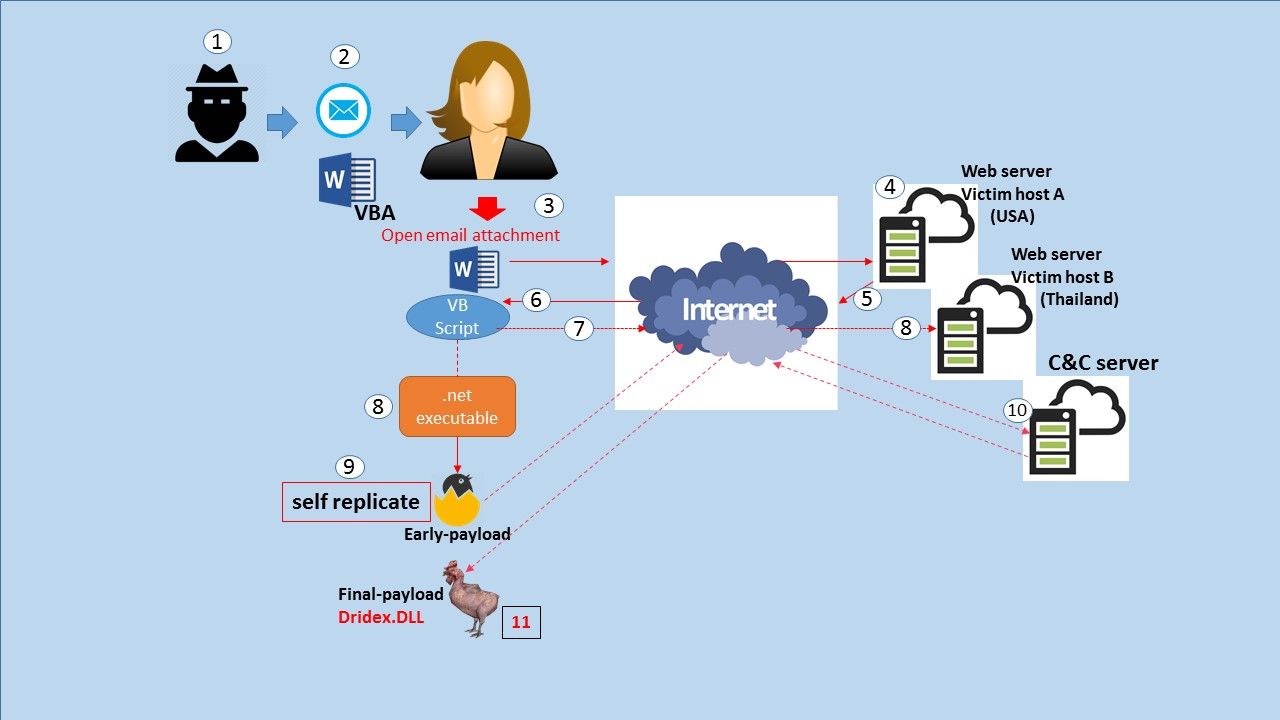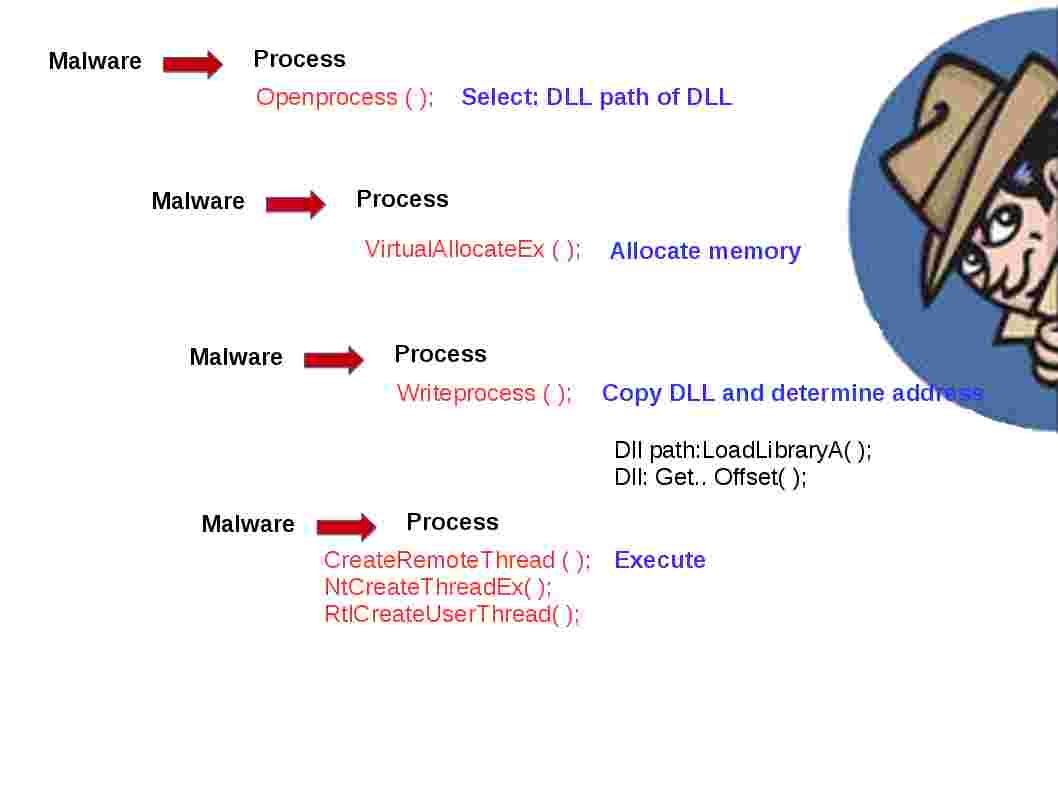
Whenever Windows OS or applications execute syntax action, check the registry, read or write a file, launch or close a process, etc. It result in Windows calling a service in the System Service Descriptor Table (SSDT).
Hooking SSDT technique exploits found on 2010. The problem was that attacker might fool the security check especially antivirus program. Attacker benefits on behavior of an electronic, software or other system output design limitation. A specific kind of bug given by race condition. This is so called time-of-check-to-time-of-use (TOCTTOU or TOCTOU), a vulnerability in security-conscious code. Microsoft suggest antivirus vendor use microsoft offical API, whereas the official API does not support all the required functions. Therefore antivirus vendor was still forced to use SSDT hooks to implement behavior detection.
CWE-367 – The software checks the state of a resource before using that resource, but the resource’s state can change between the check and the use in a way that invalidates the results of the check. This can cause the software to perform invalid actions when the resource is in an unexpected state.
How the code (TOCTTOU) does?
The program uses the access() system call to check if the person running the program has permission to access the specified file before it opens the file and performs the necessary operations. The program uses the access() system call to check if the person running the program has permission to access the specified file. If an attacker replaces file after the call to access() with a symbolic link to a different file, the program will use its root privileges to operate on the file even if it is a file that the attacker would otherwise be unable to modify. By tricking the program into performing an operation that would otherwise be impermissible, the attacker has gained elevated privileges.
functionreadFile($filename){
$user = getCurrentUser();
//resolve file if its a symbolic linkif(is_link($filename)){
$filename = readlink($filename);
}
if)fileowner($filename)==$usr){
echo file_get_contents($realFile);
return;
}
else{
echo'Access denied';
returnfalse;
}
}
In real world attacker change above file from a real file to a symbolic link between the calls to is_link() and file_get_contents(), allowing the reading of arbitrary files.
Hooked with inline, IAT or EAT hooks
Reference: System Service Descriptor Table (SSDT) is an internal dispatch table within Microsoft Windows. Hooking SSDT calls is often used as a technique in both Windows rootkits and antivirus software.
Why Anti-viruses not check the library modules of exe to detect hook?
Avoid false positive mainly! Antivirus detect the (SetWindowsHookEx) API call is not sufficient since it is also used by many authorized applications. For instance the fundamental design of hooking calls such as SetWindowsHookEx is for debugging.
Security expert know the weakness of anti virus program and therefore develop additional scan tool. Yes, it is a Ring 3 hook scanner. The scanner can do the following functions.
(Ring3) Scan every running process:
(Ring3) Scan only the running process with PID
To be honest, IT guy might feel that malware running on Ring 3 is easy to figure out compare with Ring 1 and Ring 0. But properly not.
Conclusion:
As of today, it is hard to judge behavior base malware detection method is outdated. We known that malware detector especially FireEye can arrest over 99% of malware. The reason is that the detective control of Fire-eye looks great. The device stand parallel with layer 3 core switch. The gateway type infrastructure which enhance the detection level of malware activities. It is because malware require communicate with C&C server.
Next topic we discuss Ring 1 and Ring 0 concept. Stay tuned.