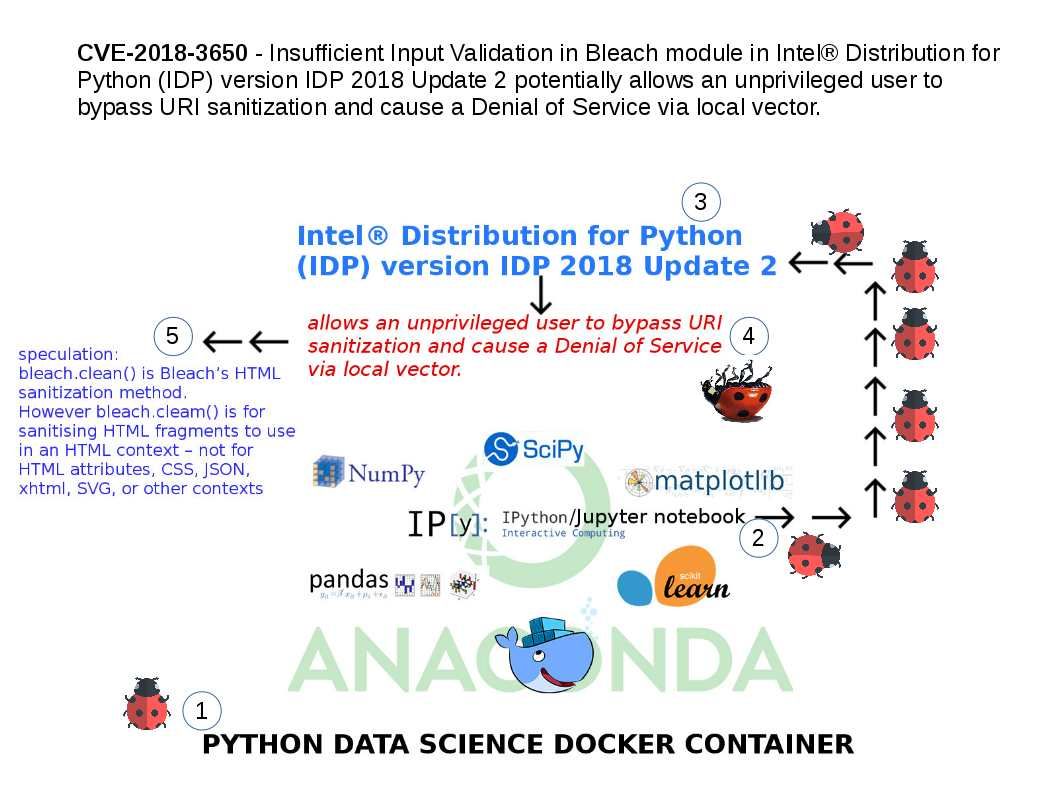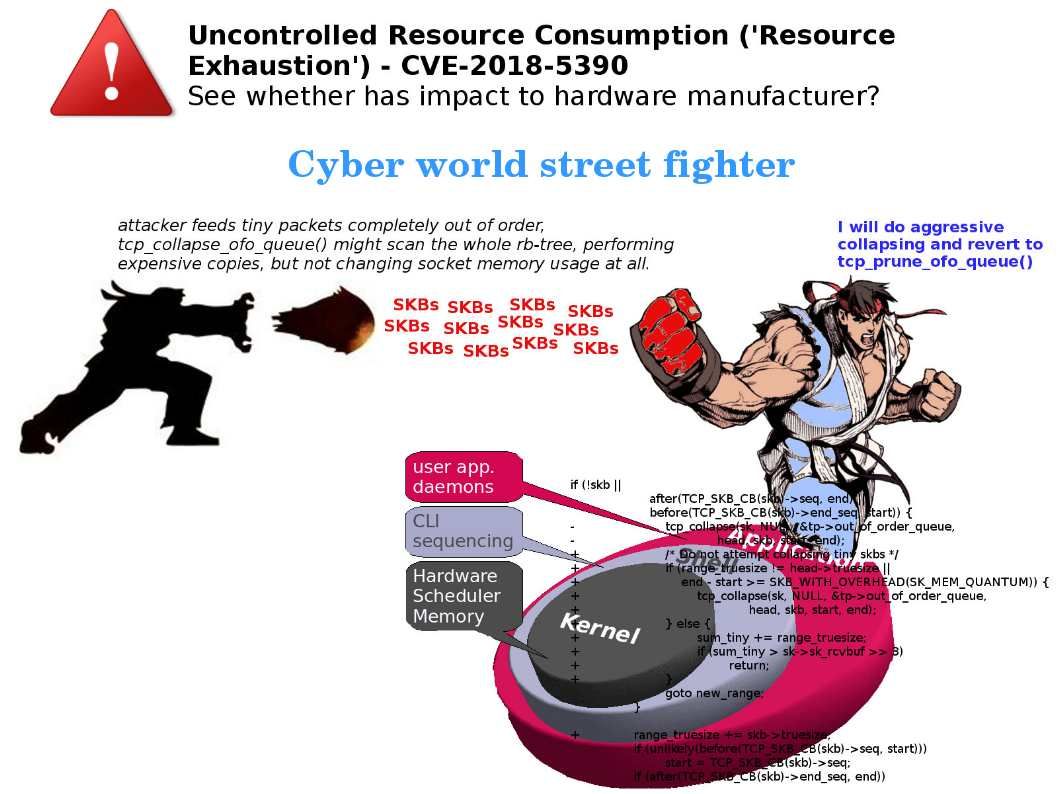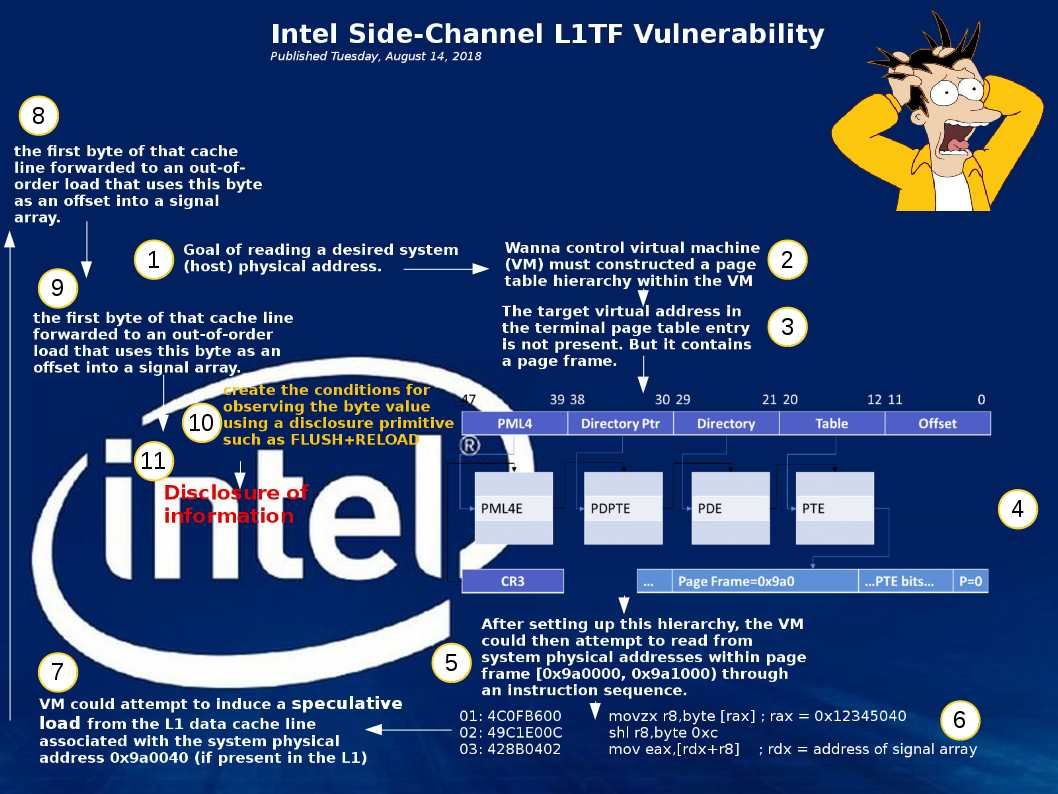
An official announcement state that there are three more data-leakage security holes found in Intel chips:
- CVE-2018-3615 – L1 Terminal Fault: SGX
- CVE-2018-3620 – L1 Terminal Fault: OS/SMM
- CVE-2018-3646 – L1 Terminal Fault: VMM
Across the board, Intel’s desktop, workstation, and server CPUs are vulnerable.
Official announcement shown as below:
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00161.html
Reminder: I am using window 7 instead of windows 10. In retrospect, I did patch management which focus for spectre on Jan 2018. It behind my seen that CPU vulnerability still valid on my PC. The cache-misses as compared to missed-branches data collected from Spectre is possible on my PC (see attached screen-shot for reference). So I believe that this flaw (L1TF) substained. Furthermore the vendor known earlier. May be the vendor believe that this is the appropriate timeframe to announce.
Below historical record for reference:
CPU vulnerability remediation status update – especially Spectre