Preface: SAP has released its August 2022 Patch Day updates. However, you will still see items you are familiar with. What’s that? As follows!
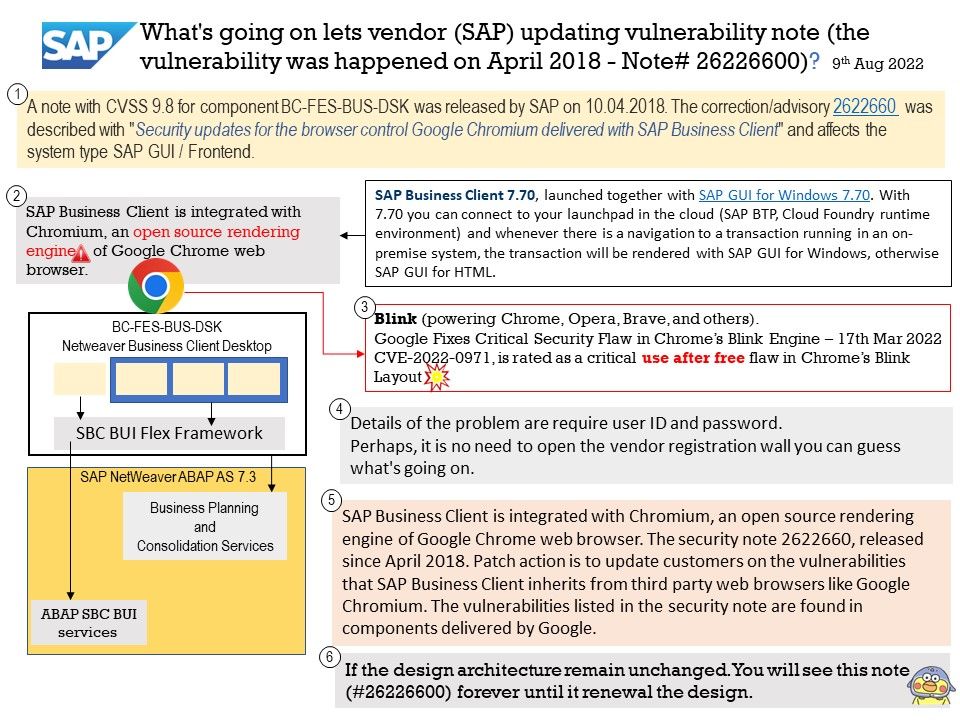
Update to Security Note released on April 2018 Patch Day:
Security updates for the browser control Google Chromium delivered with SAP Business ClientProduct-SAP Business Client, Versions -6.5, 7.0, 7.70 (Hot News – CVSS 10)
Background: SAP Business Client 7.70, launched together with SAP GUI for Windows 7.70. With 7.70 you can connect to your launchpad in the cloud (SAP BTP, Cloud Foundry runtime environment) and whenever there is a navigation to a transaction running in an on-premise system, the transaction will be rendered with SAP GUI for Windows, otherwise SAP GUI for HTML. Furthermore, SAP Business Client is integrated with Chromium, an open source rendering engine of Google Chrome web browser.
What rendering engine does Chrome use? Most of Chrome’s source code comes from Google’s free and open-source software project Chromium, but Chrome is licensed as proprietary freeware. WebKit was the original rendering engine, but Google eventually forked it to create the Blink engine; all Chrome variants except iOS now use Blink.
Vulnerability details: No CVE record number provided. A note with CVSS 9.8 for component BC-FES-BUS-DSK was released by SAP on 10.04.2018. The correction/advisory 2622660 was described with “Security updates for the browser control Google Chromium delivered with SAP Business Client” and affects the system type SAP GUI / Frontend.
Details of the problem are require user ID and password – https://accounts.sap.com/saml2/idp/sso .Perhaps, it is no need to open the vendor registration wall you can guess what’s going on.
SAP Business Client is integrated with Chromium, an open source rendering engine of Google Chrome web browser. The security note 2622660, released since April 2018. Patch action is to update customers on the vulnerabilities that SAP Business Client inherits from third party web browsers like Google Chromium. The vulnerabilities listed in the security note are found in components delivered by Google.
On 9th of August 2022, SAP Security Patch Day saw the release of 5new Security Notes. Further, there were 2 updates to previously released Patch Day Security Notes.Please refer to the link for details – https://dam.sap.com/mac/app/e/pdf/preview/embed/ucQrx6G?ltr=a&rc=10
.jpg)
.jpg)