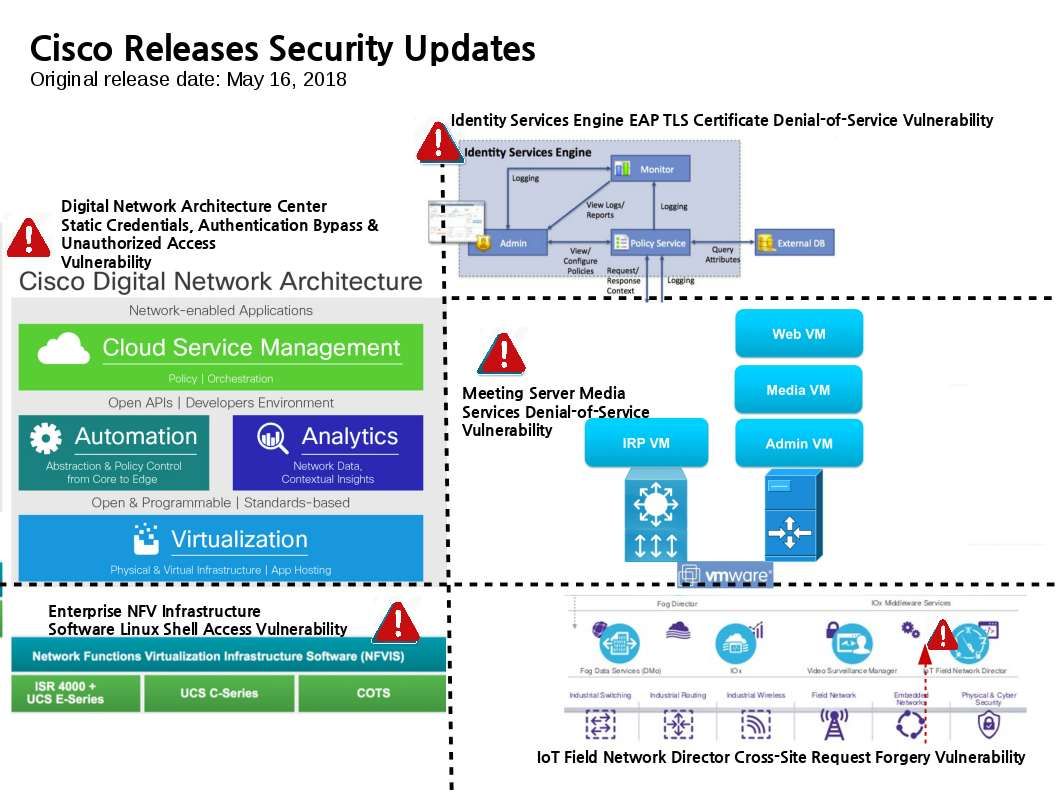
Cisco Releases Security Updates
Original release date: May 16, 2018
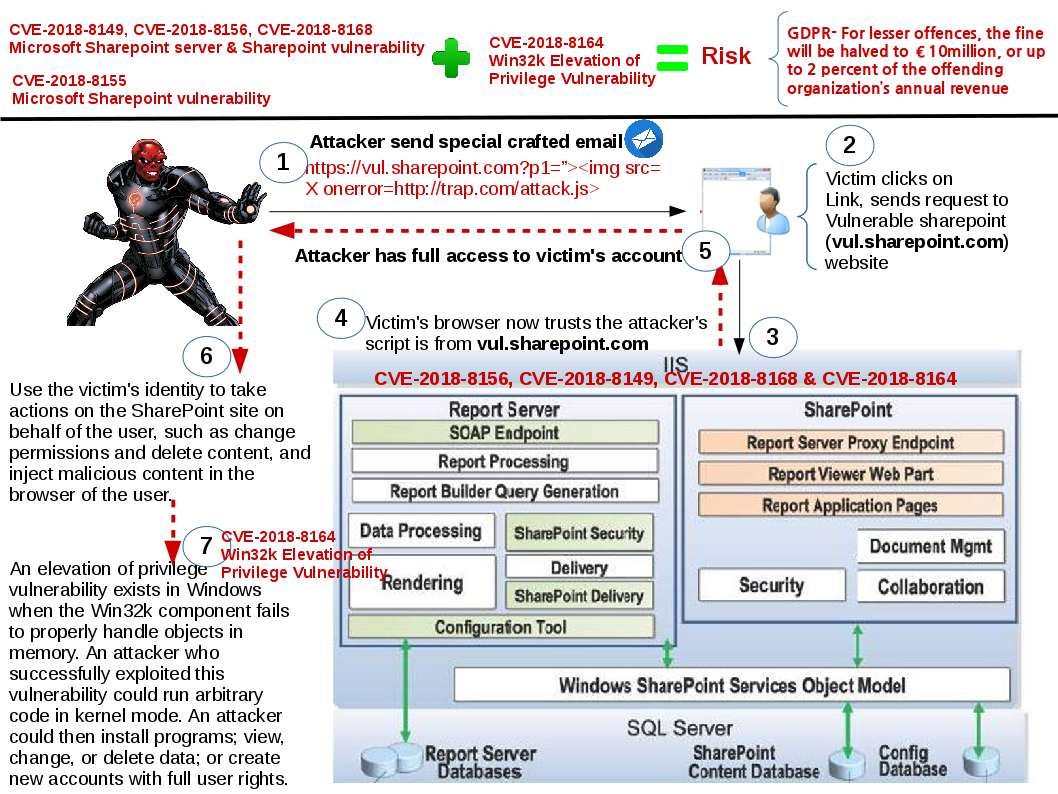
- Digital Network Architecture Center Static Credentials Vulnerability
- Digital Network Architecture Center Authentication Bypass Vulnerability
- Digital Network Architecture Center Unauthorized Access Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180516-dna
Enterprise NFV Infrastructure Software Linux Shell Access Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180516-nfvis
Meeting Server Media Services Denial-of-Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180516-msms
Identity Services Engine EAP TLS Certificate Denial-of-Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180516-iseeap
IoT Field Network Director Cross-Site Request Forgery Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180516-fnd