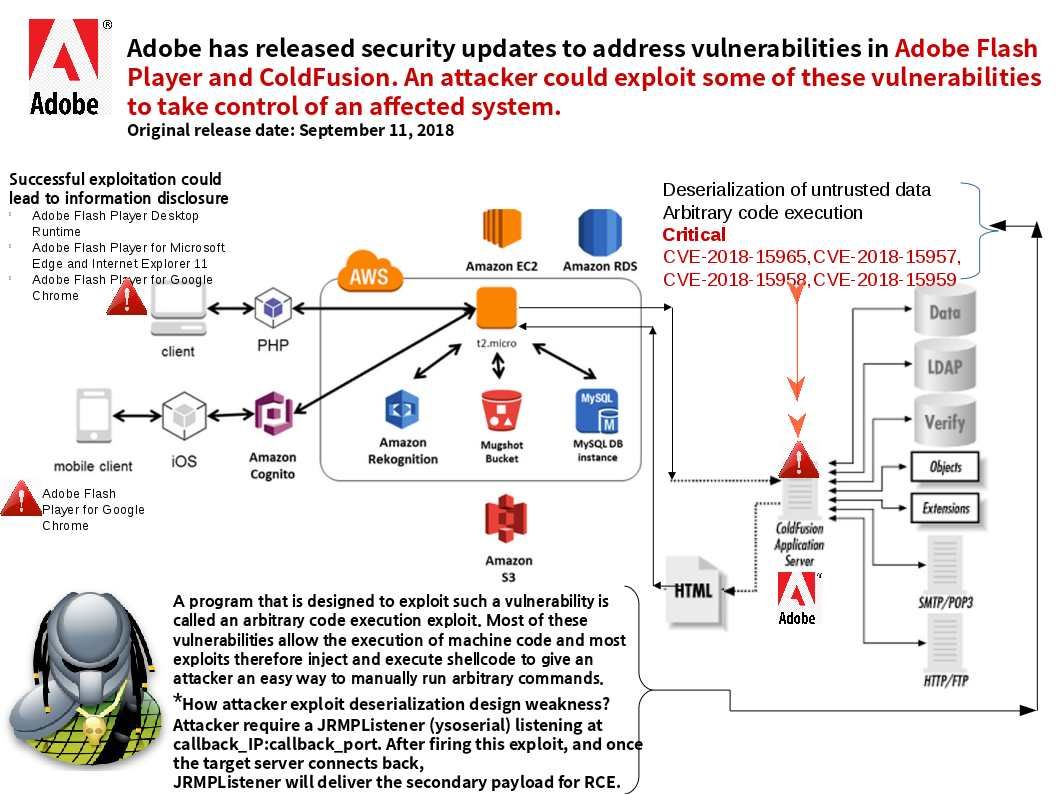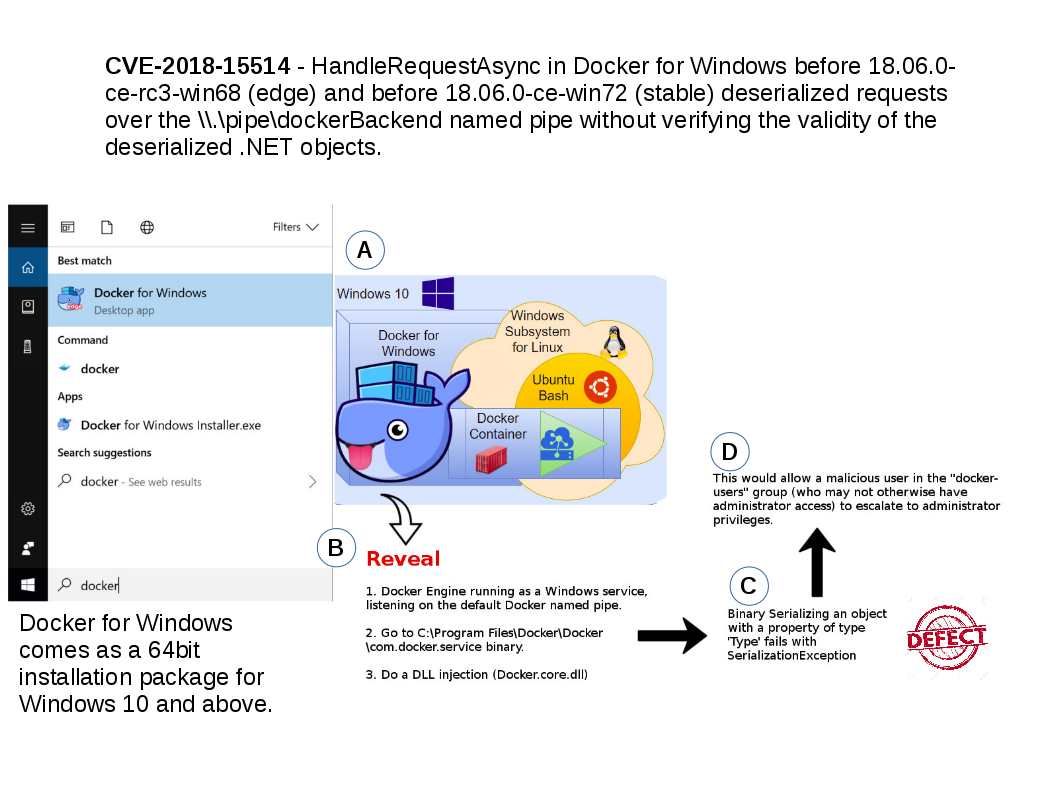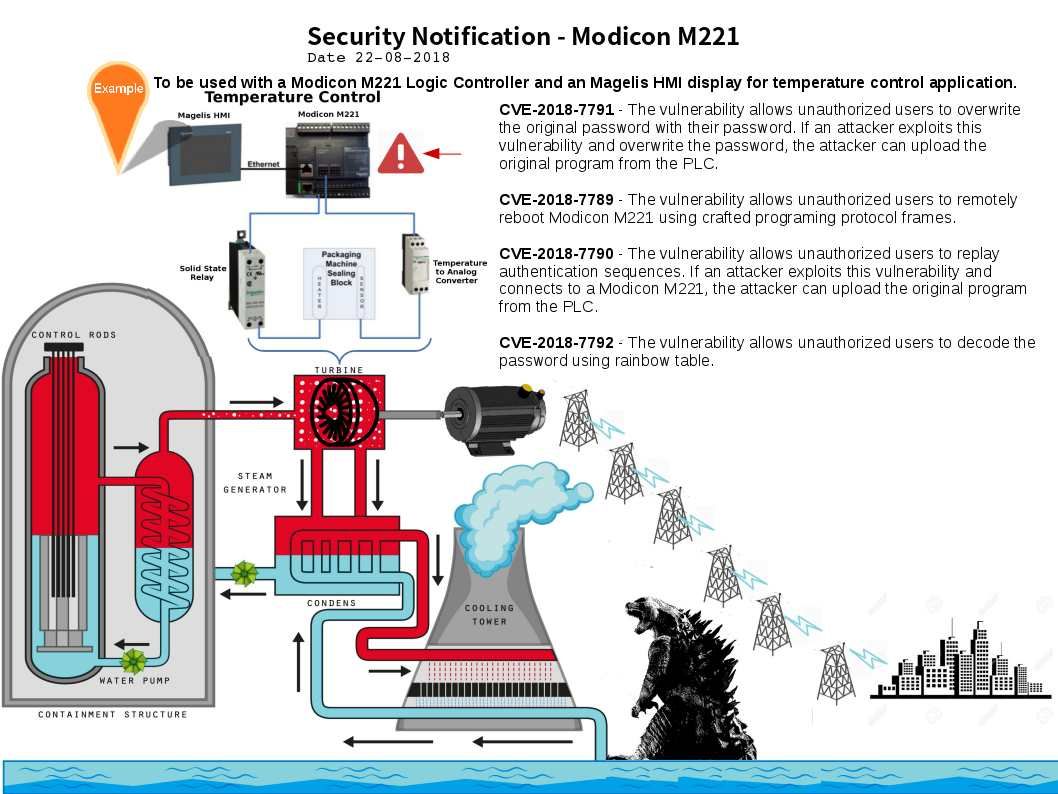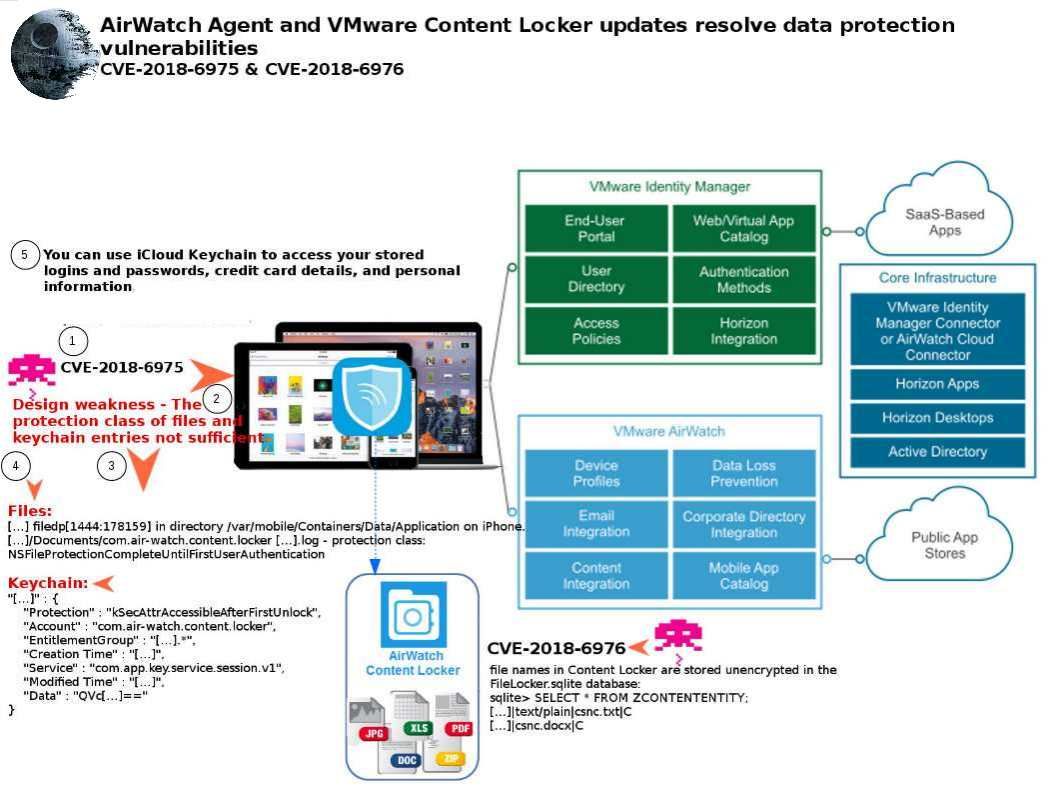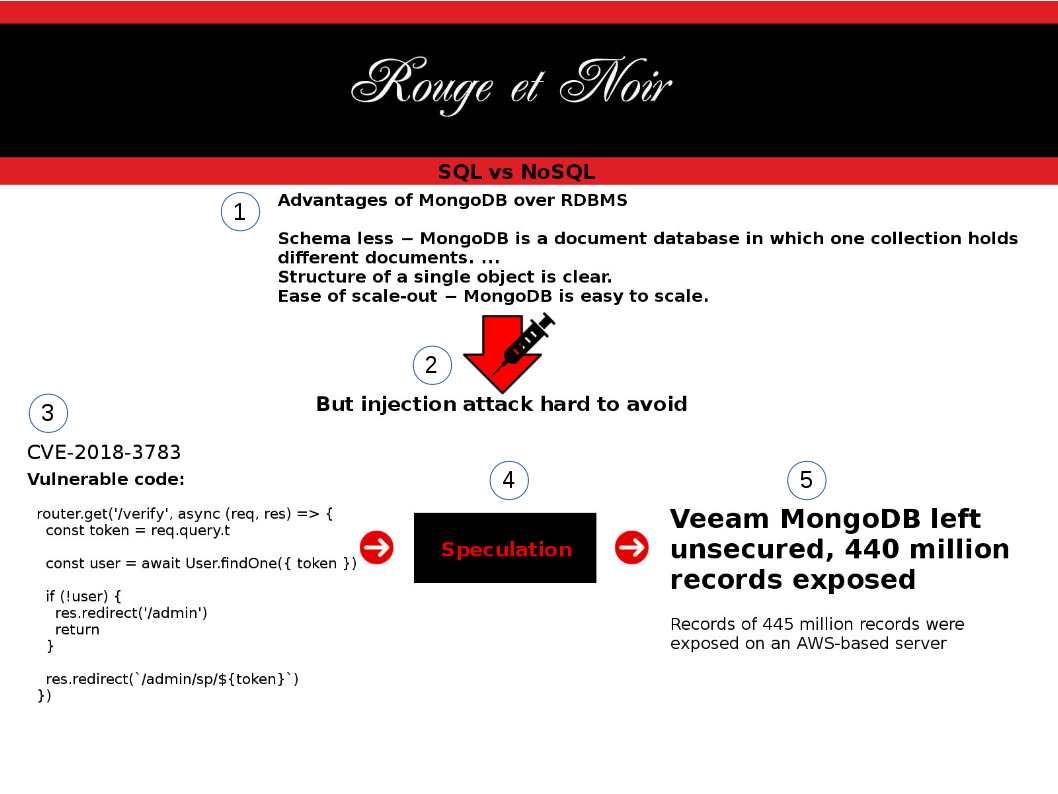
Sanitization process is important in IT world. If without correct validation, it may allow malicious code pass to trust boundary. As a result it may causes remote code execution, SQL injection, trigger Zero day attack, ….etc. So…… Headline News this week. Should you have interest, my picture can tell my speculation.
https://www.scmagazine.com/home/news/veeam-mongodb-left-unsecured-440-million-records-exposed/
Vulnerability looks scary! However, as the variety and volume of data has increased in recent years, non-relational databases like MongoDB have arisen to meet the new needs of our fluid data.