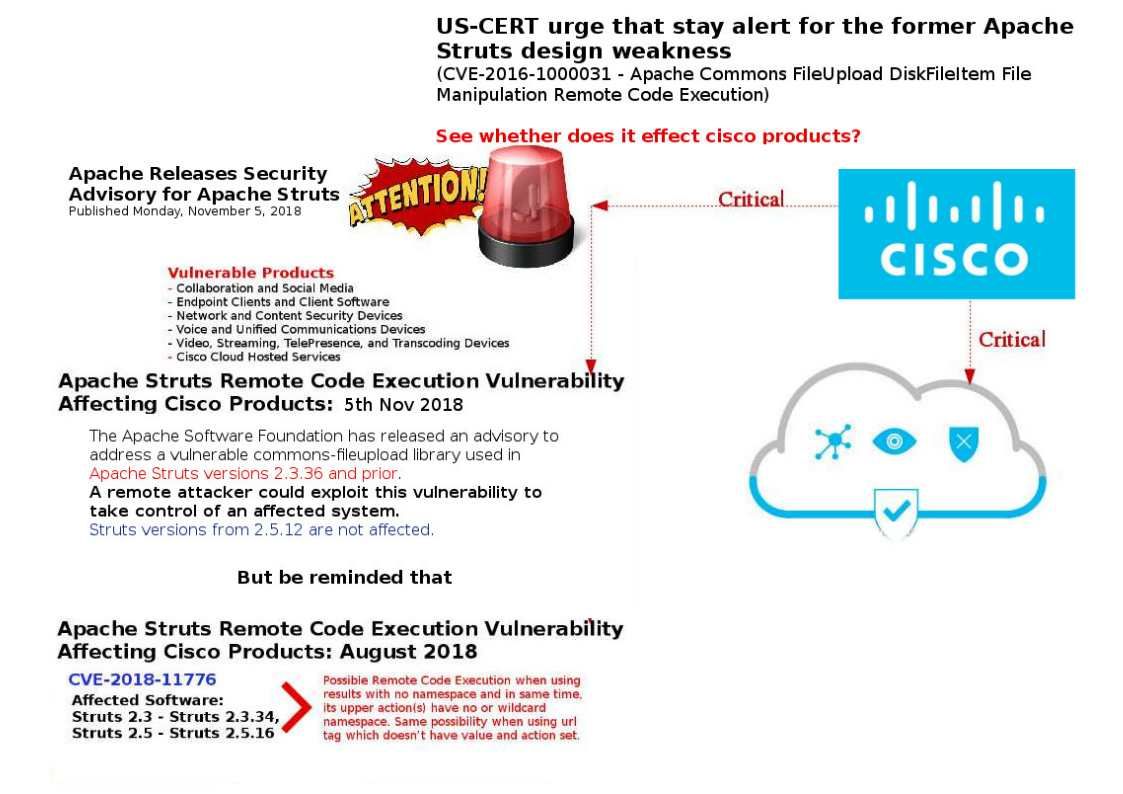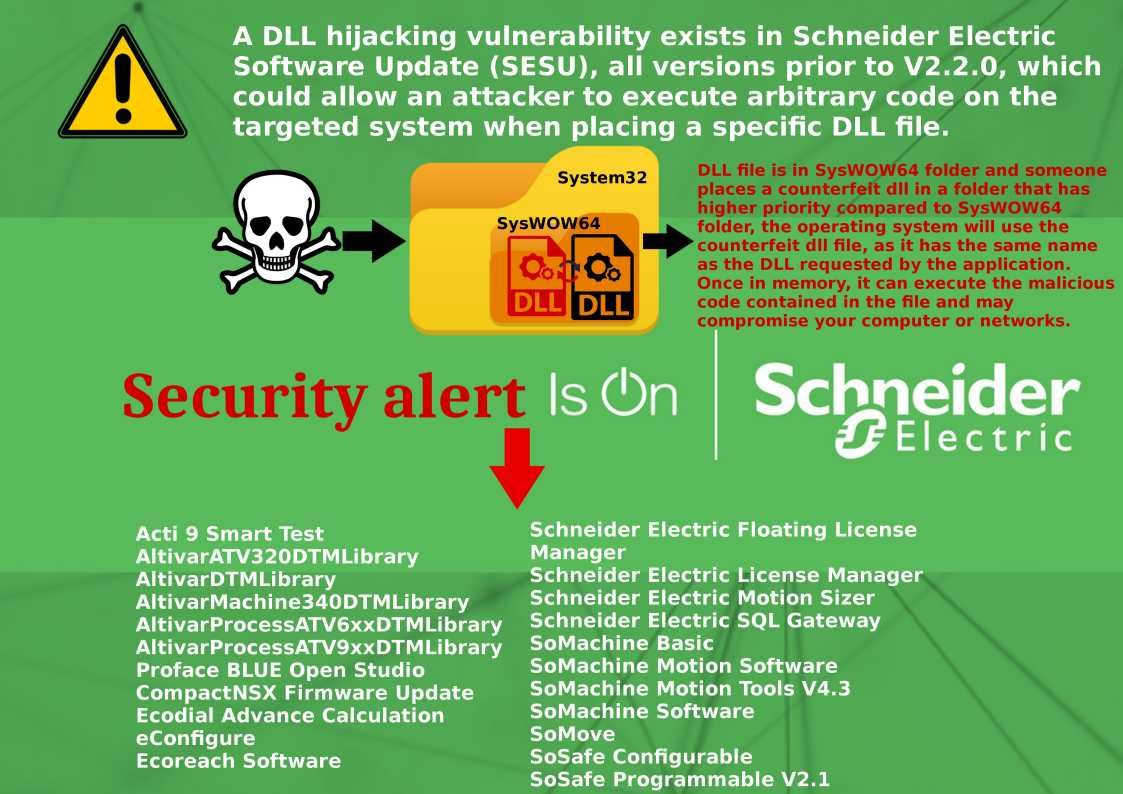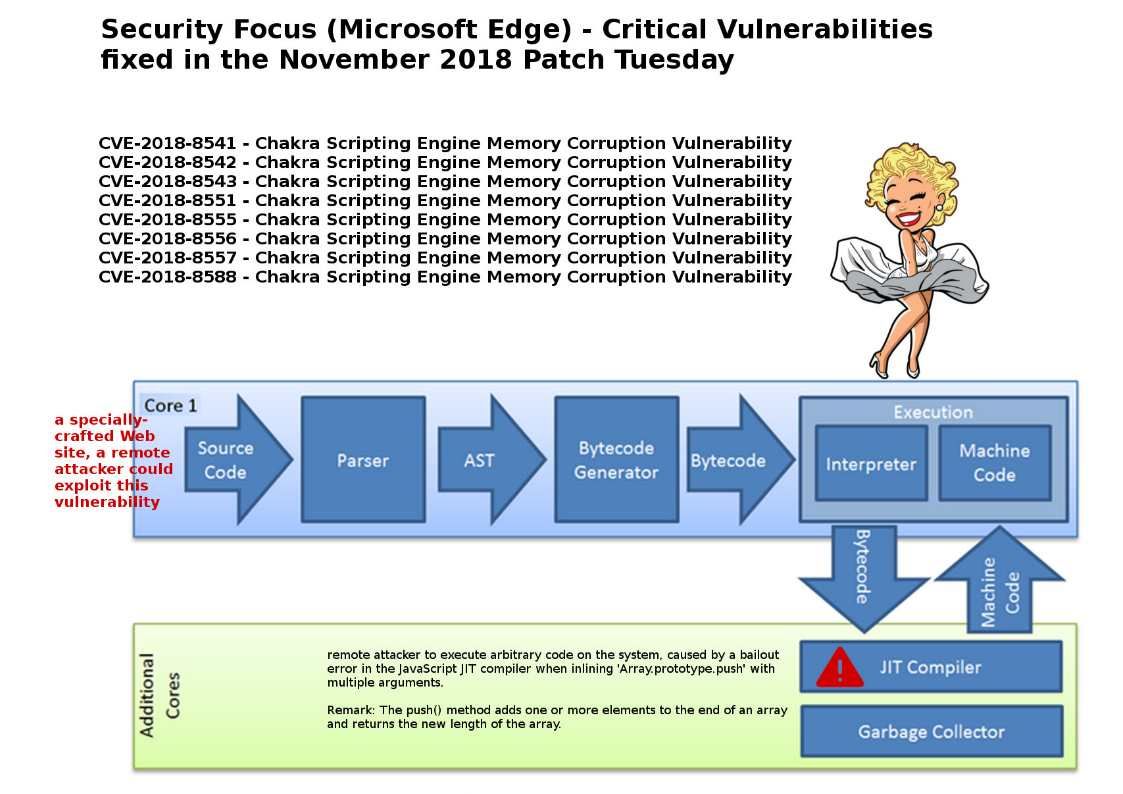
Preface:
Chakra is a JavaScript engine developed by Microsoft for its Microsoft Edge web browser. It is a fork of the JScript engine used in Internet Explorer.
Description:
The technical details issued by patch Tuesday not describe explicitly (see below).
A remote code execution vulnerability exists in the way that the Chakra scripting engine handles objects in memory in Microsoft Edge.This vulnerability could also be exploited through Microsoft Edge via specially crafted web sites or advertisements..
Speculation:
Remote attacker to execute arbitrary code on the system caused by a ballout error in the JavaScript JIT compiler when inling ‘Array.prototype.push’ with multiple arguments.
Remark: The push() method adds oneor more elements to the end of an array and returns the new length of the array.
Remedy:
CVE-2018-8541
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8541
CVE-2018-8542
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8542
CVE-2018-8543
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8543
CVE-2018-8551
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8551
CVE-2018-8555
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8555
CVE-2018-8556
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8556
CVE-2018-8557
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8557
CVE-2018-8588
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8588