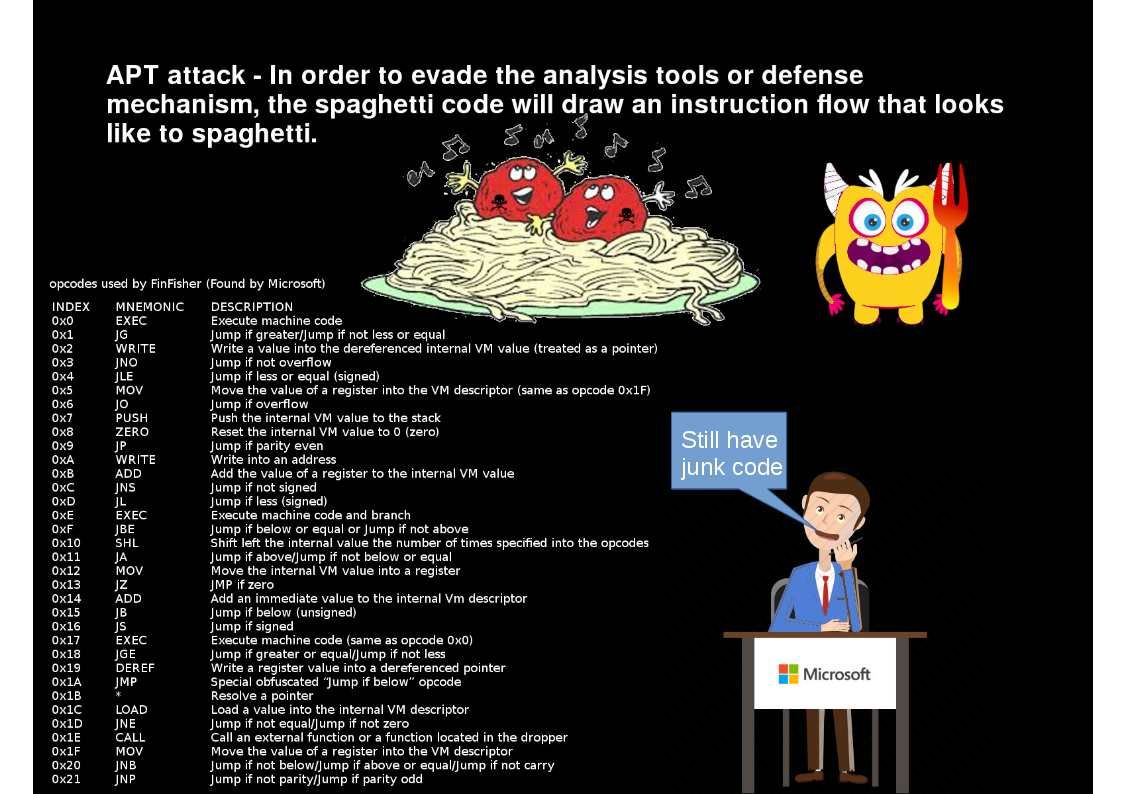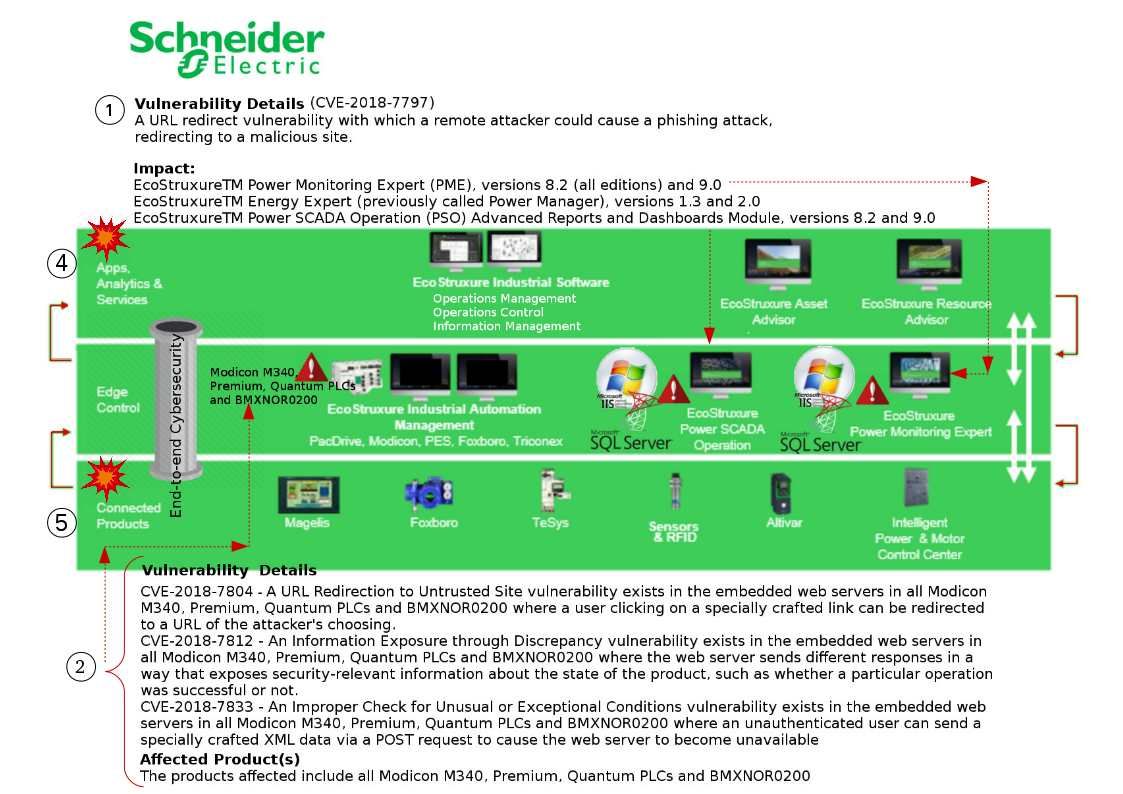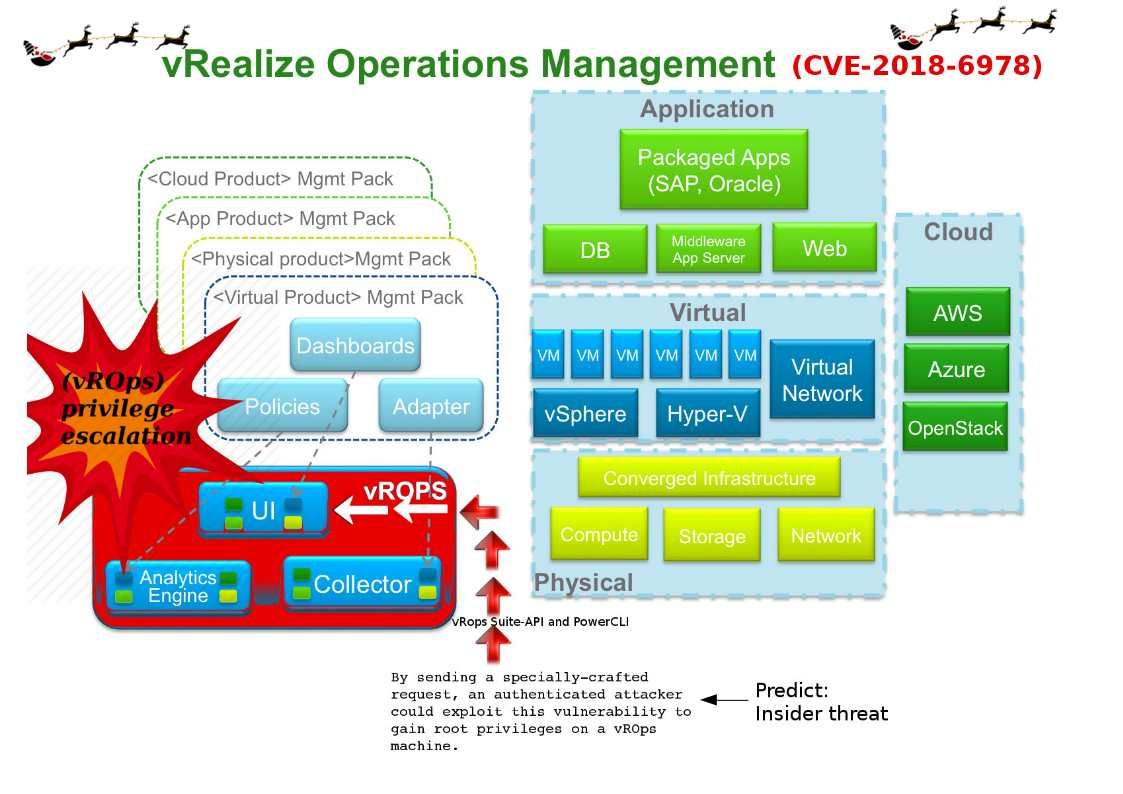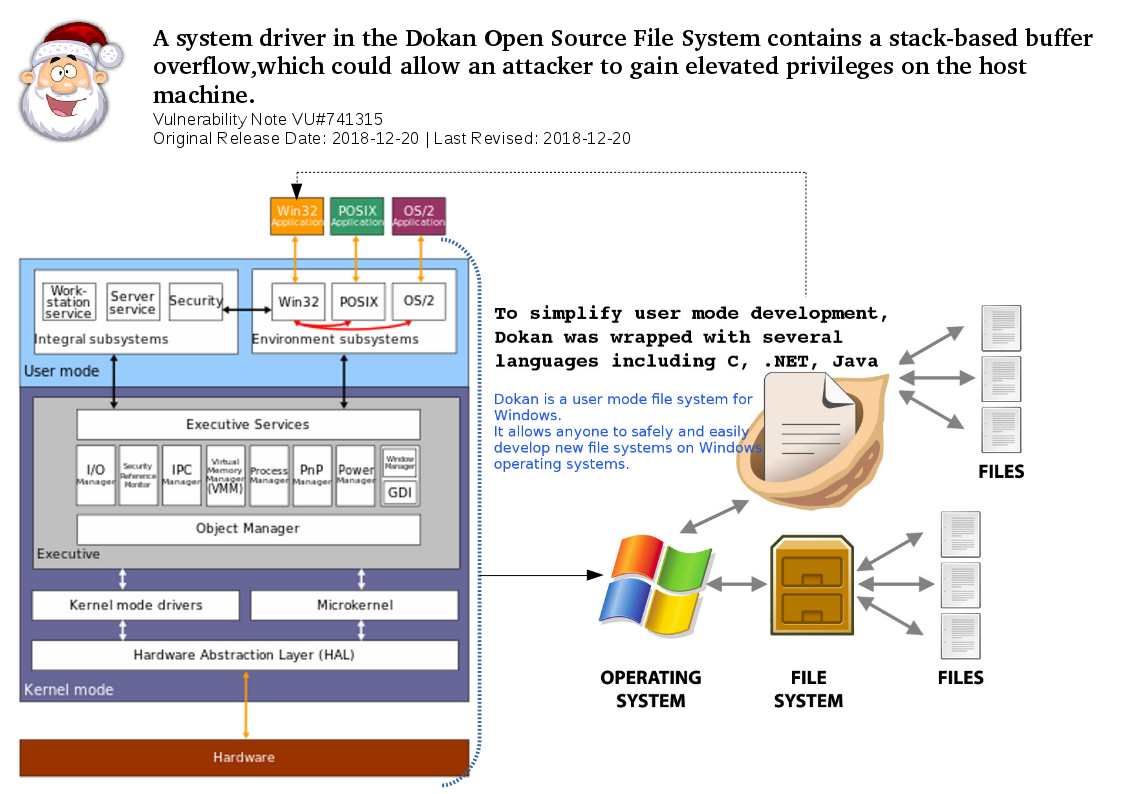
Preface: Electric vehicles (EVs) have no tailpipe emissions. Replacing conventional vehicles with EVs can help improve roadside air quality and reduce greenhouse gas emissions.
Technical background: Level 2 electric car chargers deliver 10 to 60 miles of range per hour of charging. They can fully charge an electric car battery in as little as two hours, making them an ideal option for both homeowners who need fast charging and businesses who want to offer charging stations to customers.
Subject matter expert:
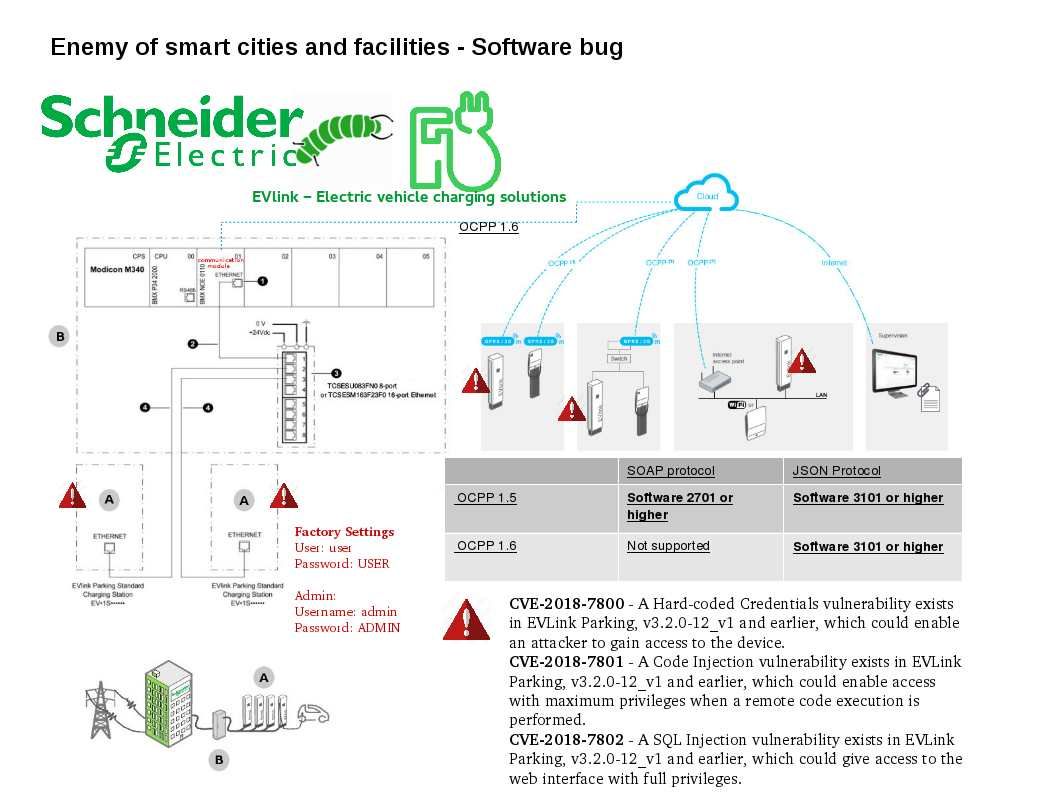
EVlink Parking a charging stations for shared usage or on-street developed by Schneider Electric.
Vulnerabilities found:
Schneider Electric has become aware of multiple vulnerabilities in the EVLink Parking product (see below):
- A SQL Injection vulnerability exists in EVLink Parking, v3.2.0-12_v1 and earlier, which could give access to the web interface with full privileges.
- A Code Injection vulnerability exists in EVLink Parking, v3.2.0-12_v1 and earlier
- A Hard-coded Credentials vulnerability exists in EVLink Parking, v3.2.0-12_v1 and earlier
Official announcement shown below url: https://download.schneider-electric.com/files?p_enDocType=Technical+leaflet&p_File_Name=SEVD-2018-354-01-EVLink.pdf&p_Doc_Ref=SEVD-2018-354-01