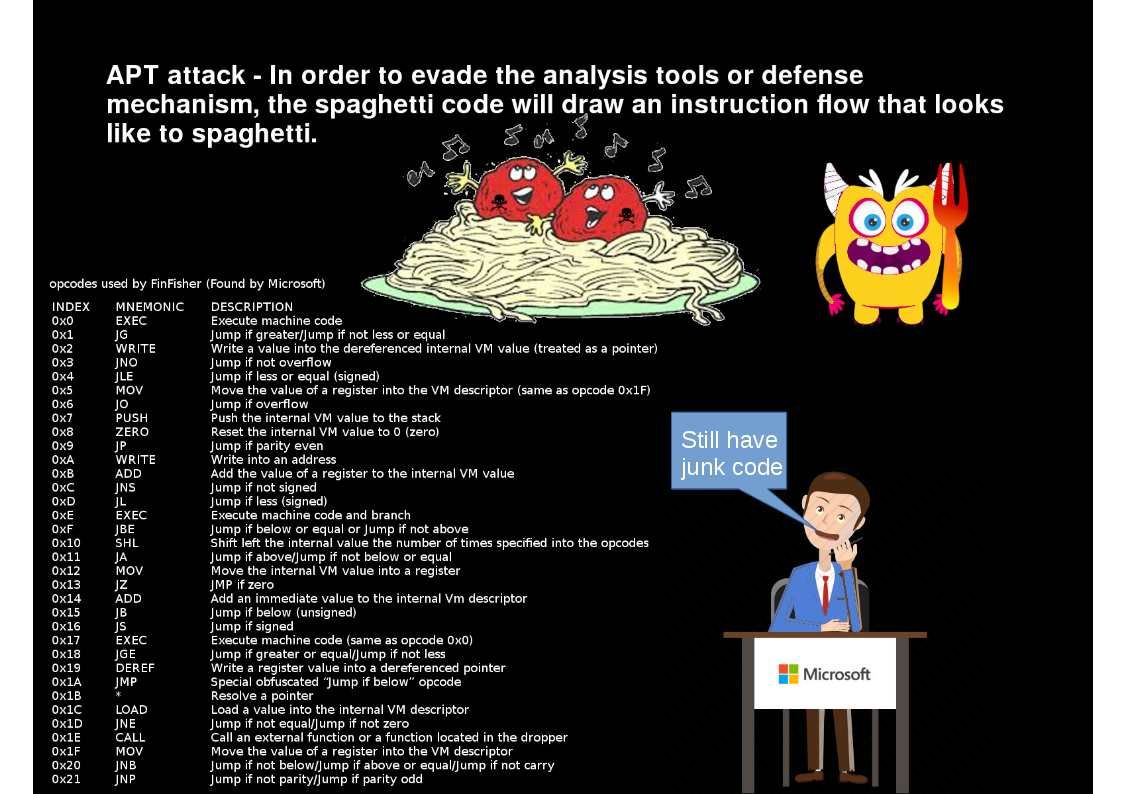
Preface: The objective of an APT attack is usually to monitor network activity and steal data. But the APT historical records shown that there are APT attacks intend to damage the network or organization.
APT might not easy to detect:
VM handler able to relocate and move code because of ASLR (address space layout randomization) applied. Example shown below for refernce.
For example the instruction AND has opcode 0x17 when you print.
The 32-bit code to run is stored entirely into the variable section with the value at offset 5 specifying the number of bytes to be copied and executed.
However the ability of conditional opcodes, the variable part can contain the next JIT packet ID or the next relative virtual address (RVA) where code execution should continue. So it such a way increase the difficult to detect the malware behaviour.
Prevention:
In order to fight against APT activities. Try to understand their goal of action. For example, we can learn from security report. For more details, please find below URL for reference.
Kaspersky Threat predictions for 2019 – https://www.brighttalk.com/webcast/15591/340766?utm_source=kdaily&utm_medium=blog&utm_campaign=gl_Vicente-Podz_organic&utm_content=link&utm_term=gl_kdaily_organic_link_blog_Vicente-Podz