Preface: On 4th Jan 2019 CERT/CC Reports Critical Vulnerabilities in Microsoft Windows, Server…
Report details:
The report recall vulnerabilities found on 13th Dec 2018 (see below):
CVE-2018-8626 Windows DNS Server Heap Overflow
Vulnerability – https://www.kb.cert.org/vuls/id/531281/
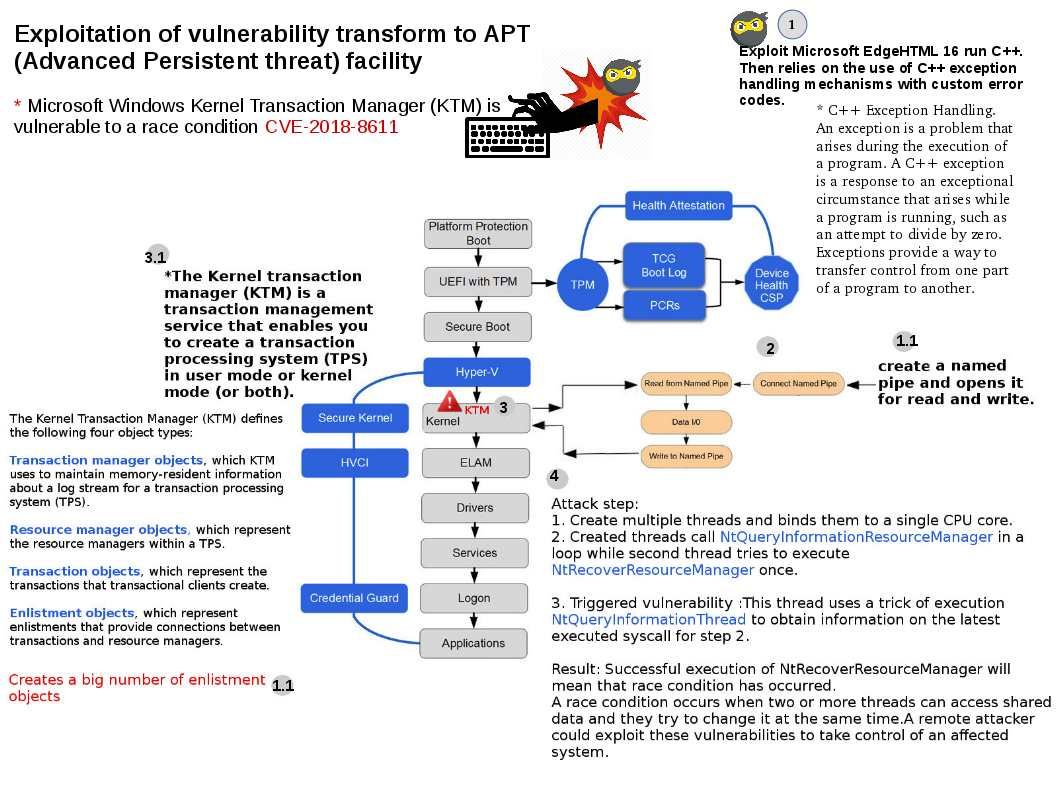
CVE-2018-8611 Windows Kernel Elevation of Privilege Vulnerability – https://www.kb.cert.org/vuls/id/289907/
But vulnerability (CVE-2018-8611) successfully bypasses modern process mitigation policies, such as Win32k System call Filtering that is used, among others, in the Microsoft Edge Sandbox and the Win32k Lockdown Policy employed in the Google Chrome Sandbox.
My observations:
Perhaps you applied the MS patch but it is hard to avoid similar evasion of technique in the moment because of the following reason.
C++ Exception Handling. An exception is a problem that arises during the execution of a program. A C++ exception is a response to an exceptional circumstance that arises while a program is running, such as an attempt to divide by zero. Exceptions provide a way to transfer control from one part of a program to another.
Suggestion: Enforce the control by SIEM or deploy MSS services.