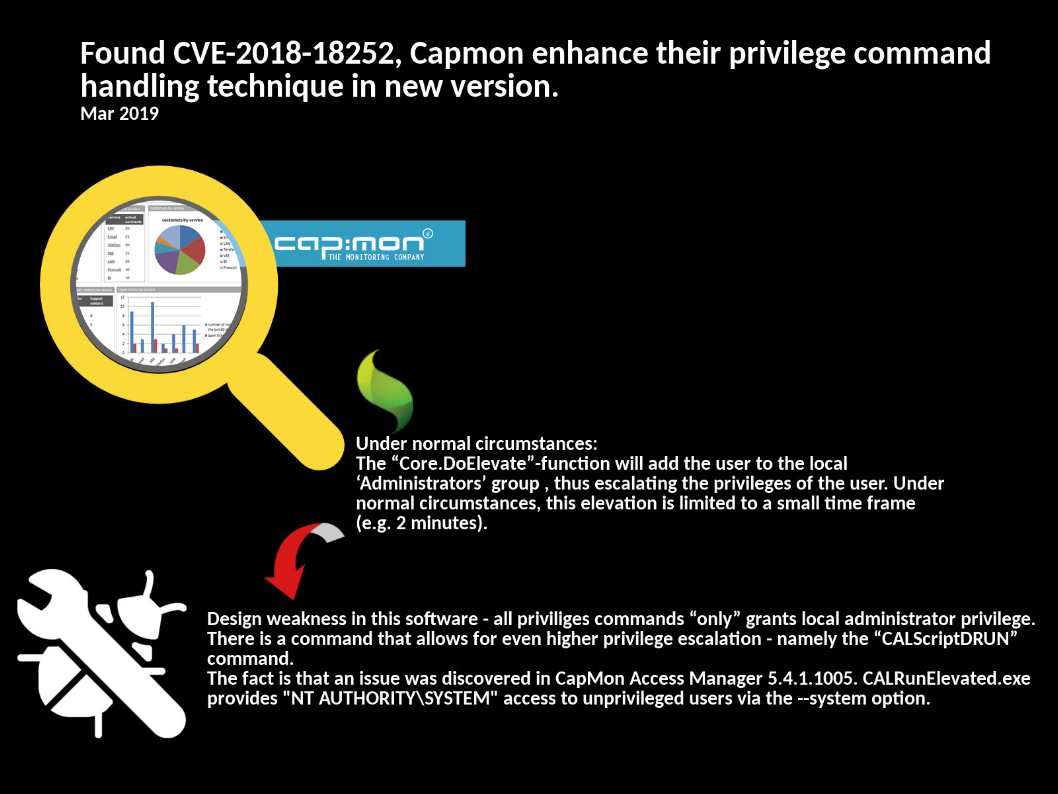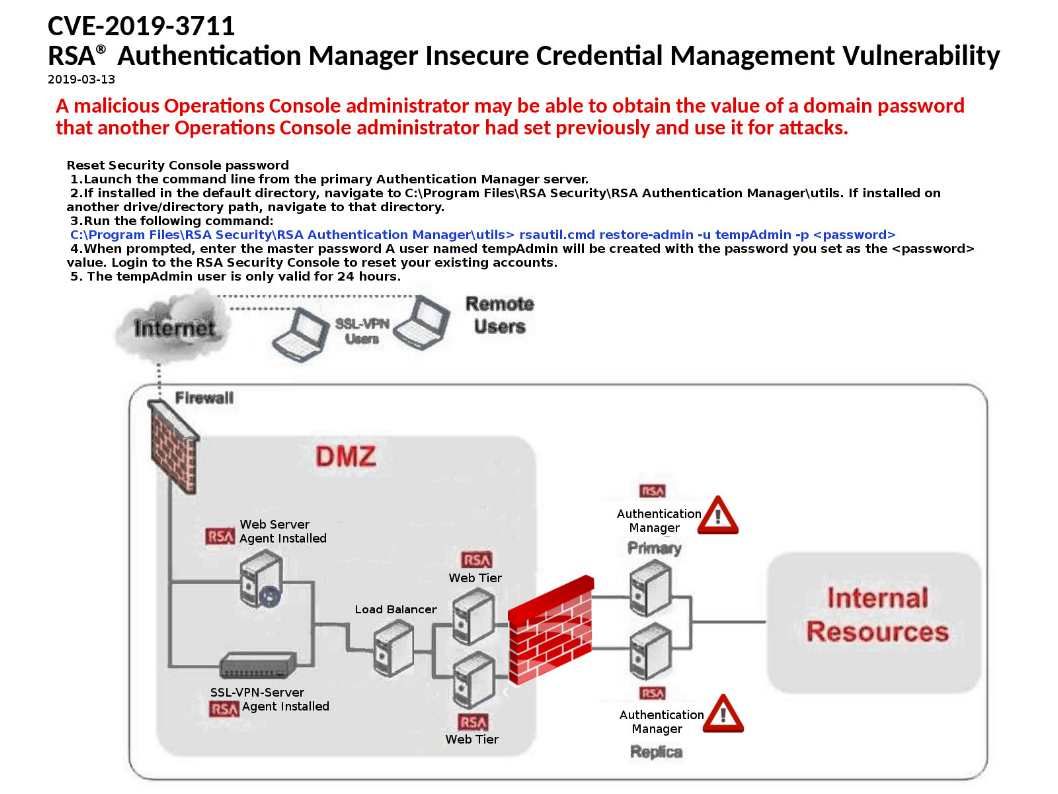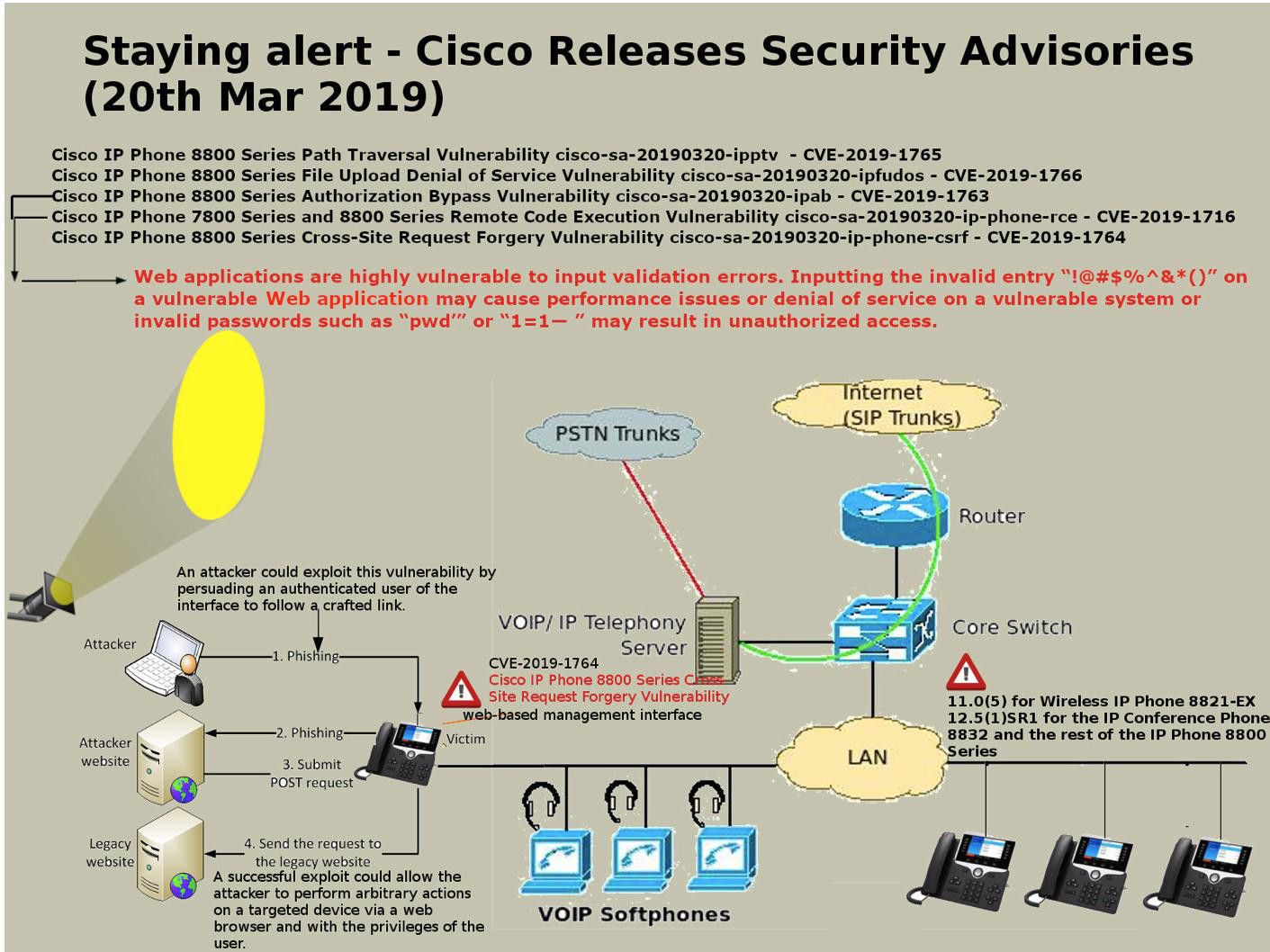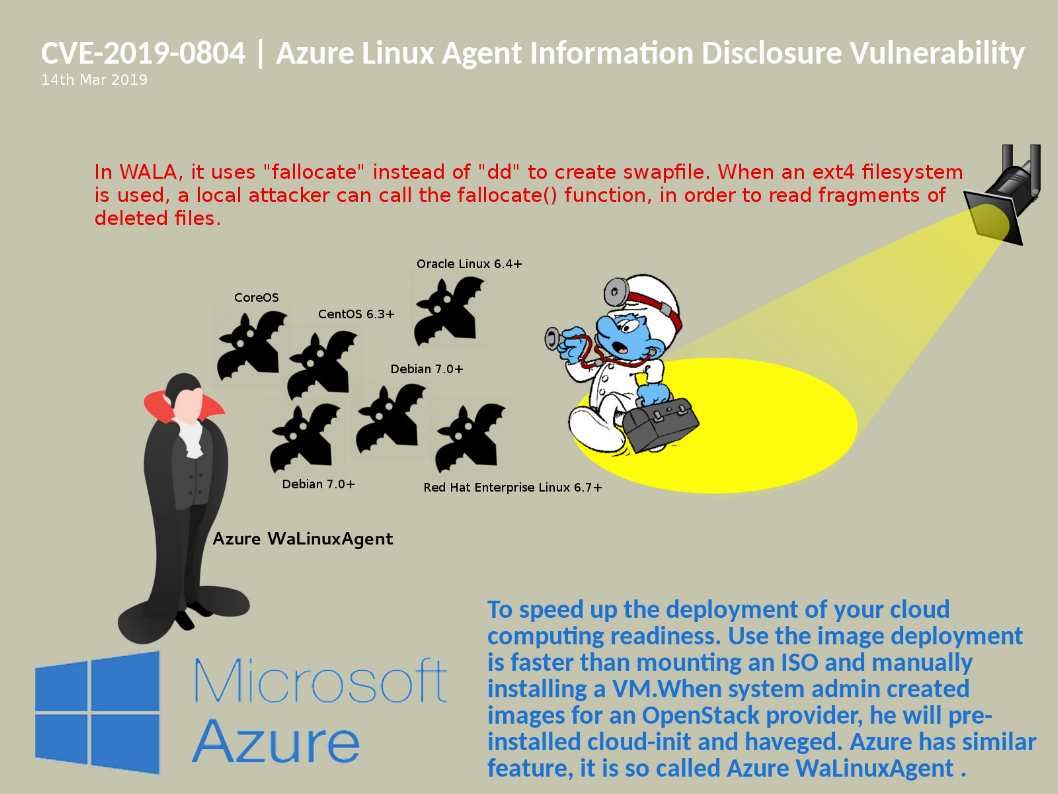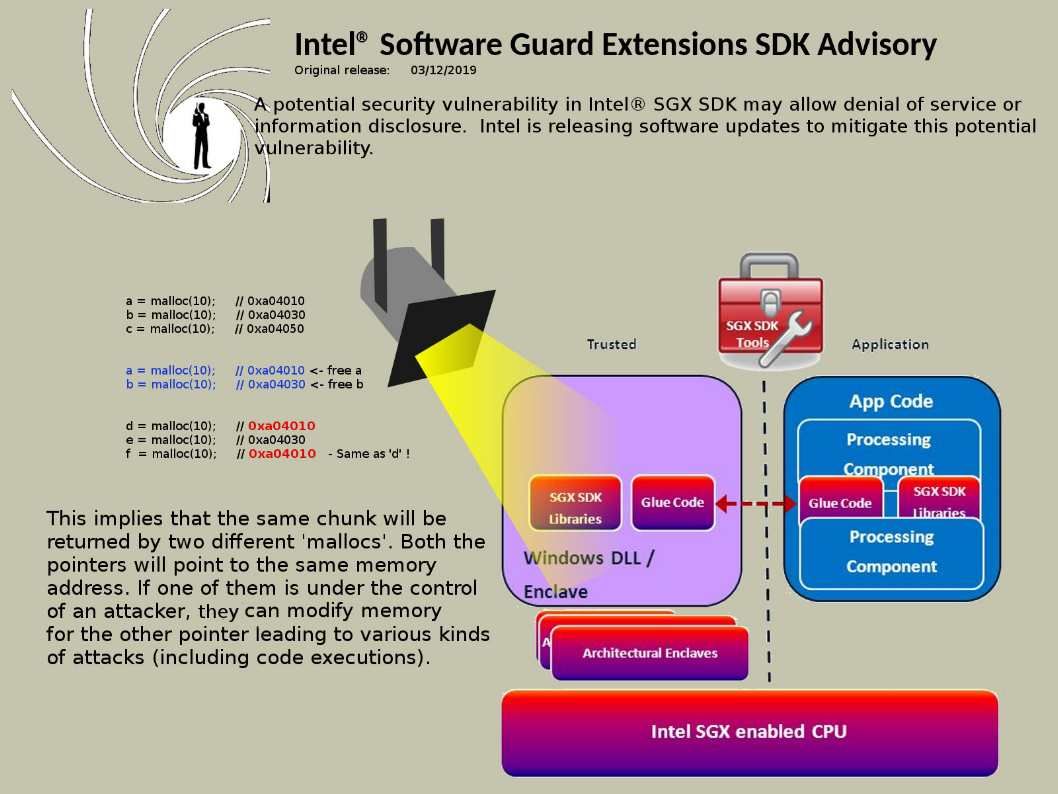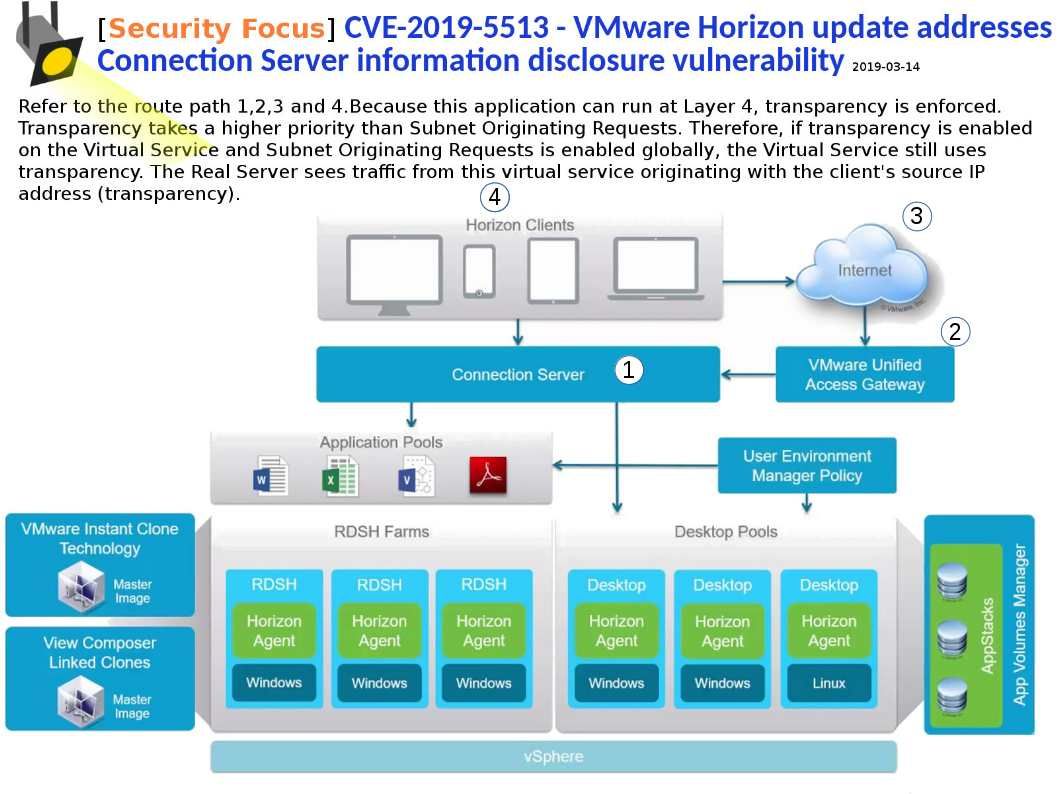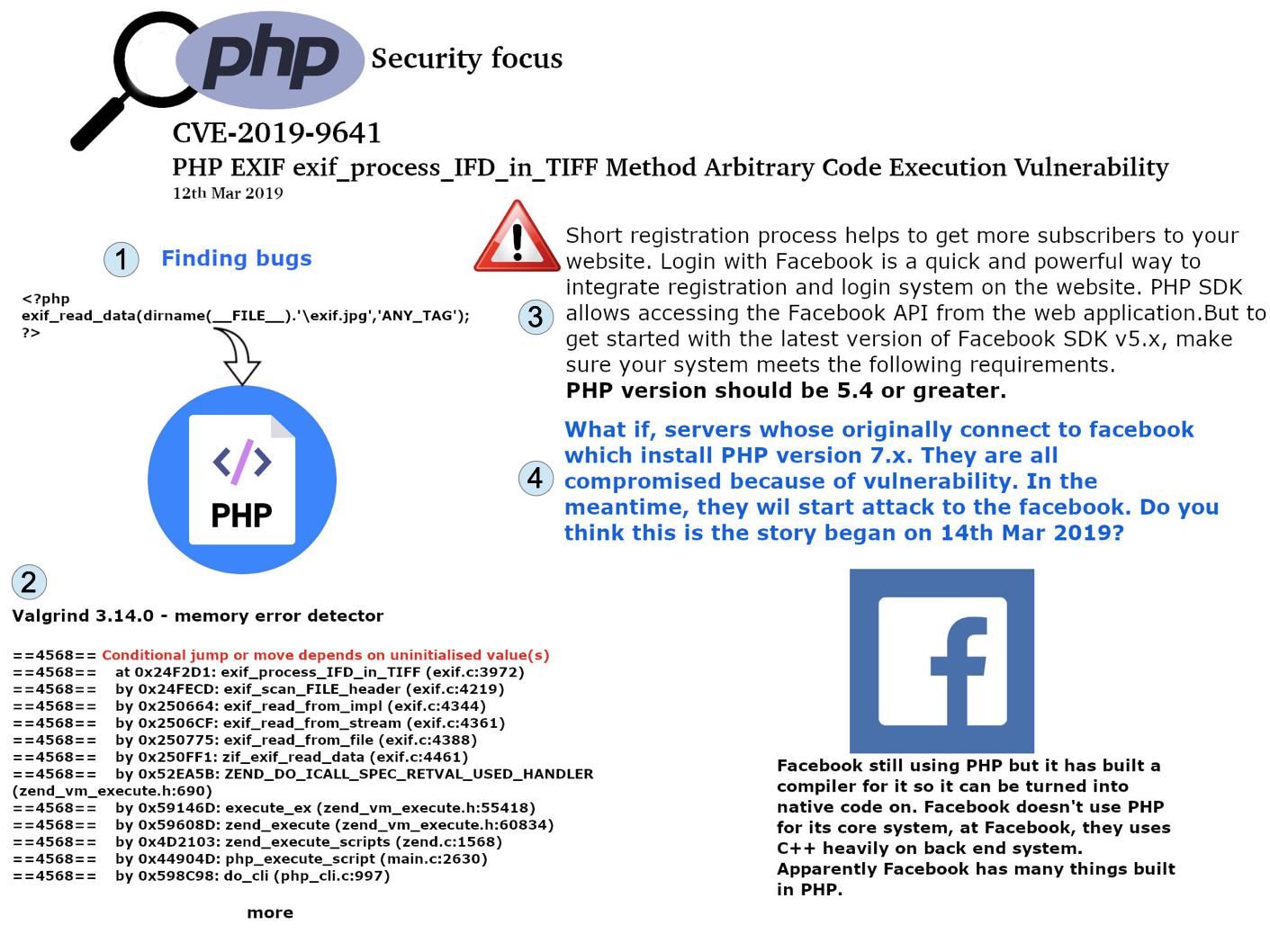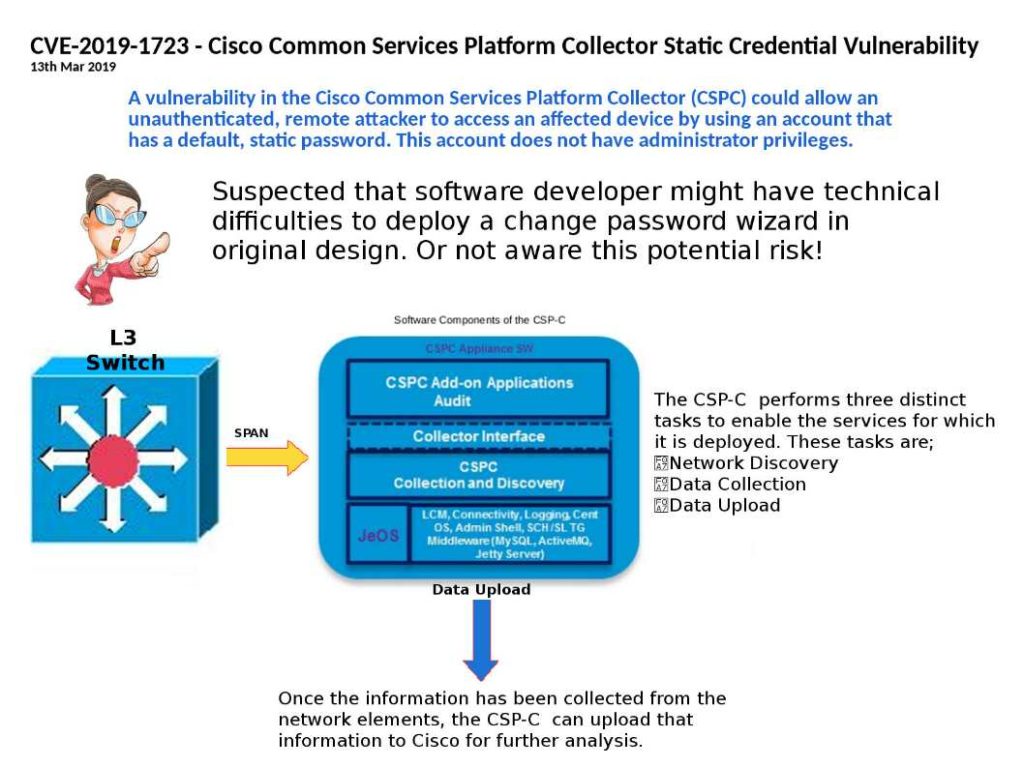
Preface: The statistic by Netcraft in January 2019, Apache server coverage market reach 30.88%.
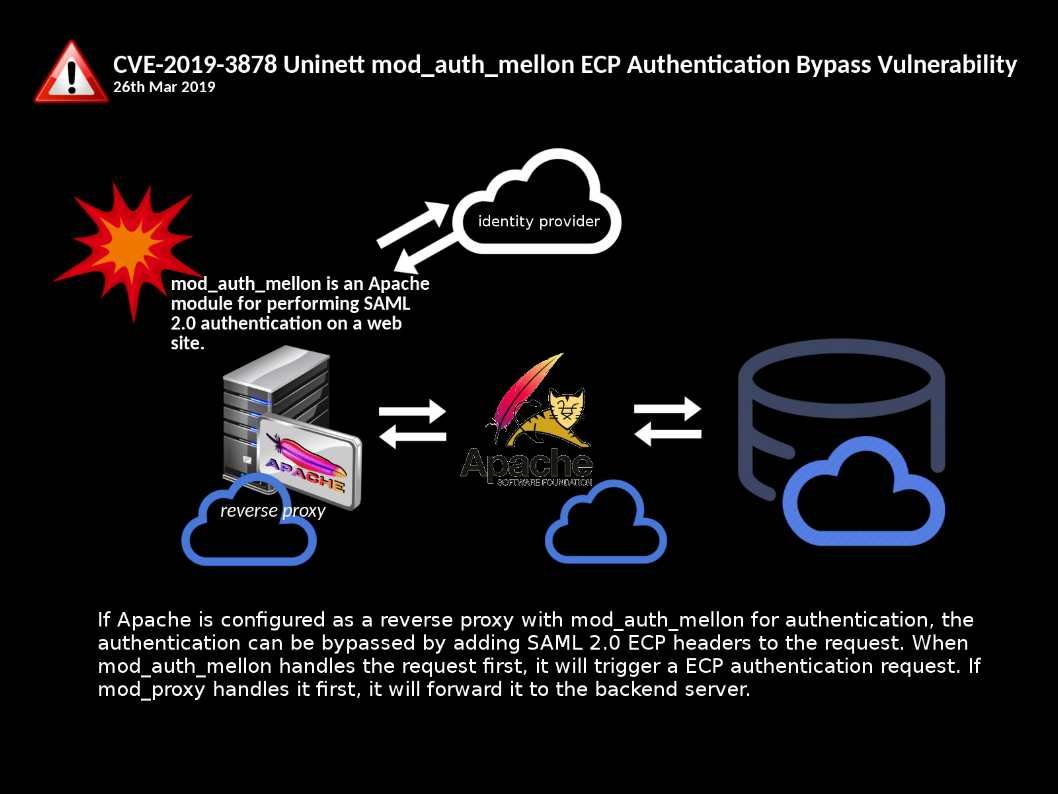
Technical background: Apache server not only contain web server service, it can config as a reserve proxy server to enhance the web infrastructure isolation level. Single sign-on authentication method growth significant in past few years. A popular web architecture model, setup Apache become reserve proxy service and thus integrate to single sign on (SAML) function.
Vulnerability detail: If Apache is configured as a reverse proxy with mod_auth_mellon for authentication, the authentication can be bypassed by adding SAML 2.0 ECP headers to the request.
Official announcement and security fixes: https://github.com/Uninett/mod_auth_mellon/releases