Preface: Space Layout Randomization (ASLR) to defend against memory corruption attacks. However, Intel Software Guard Extension (SGX), it is capability protects selected code and data from disclosure or modification. From security point of view, it provides an advance protection than before.
Vulnerability detail: Double free in Intel(R) SGX SDK for Linux before version 2.2 and Intel(R) SGX SDK for Windows before version 2.1 may allow an authenticated user to potentially enable information disclosure or denial of service via local access.
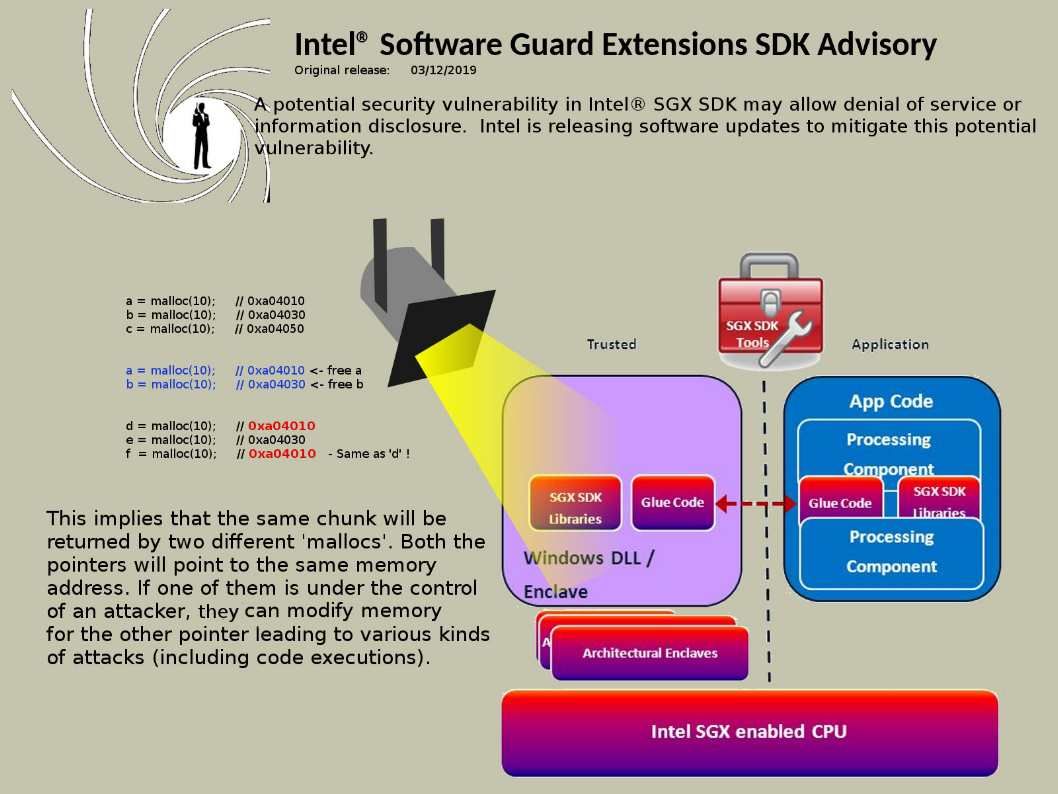
Synopsis: About double free vulnerability
Refer to the scenario of attach diagram, it shown that the same chunk will be returned by two different ‘mallocs’. Both the pointers will point to the same memory address. If one of them is under the control of an attacker, he/she can modify memory for the other pointer leading to various kinds of attacks (including code executions).
Official announcement: https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00217.html