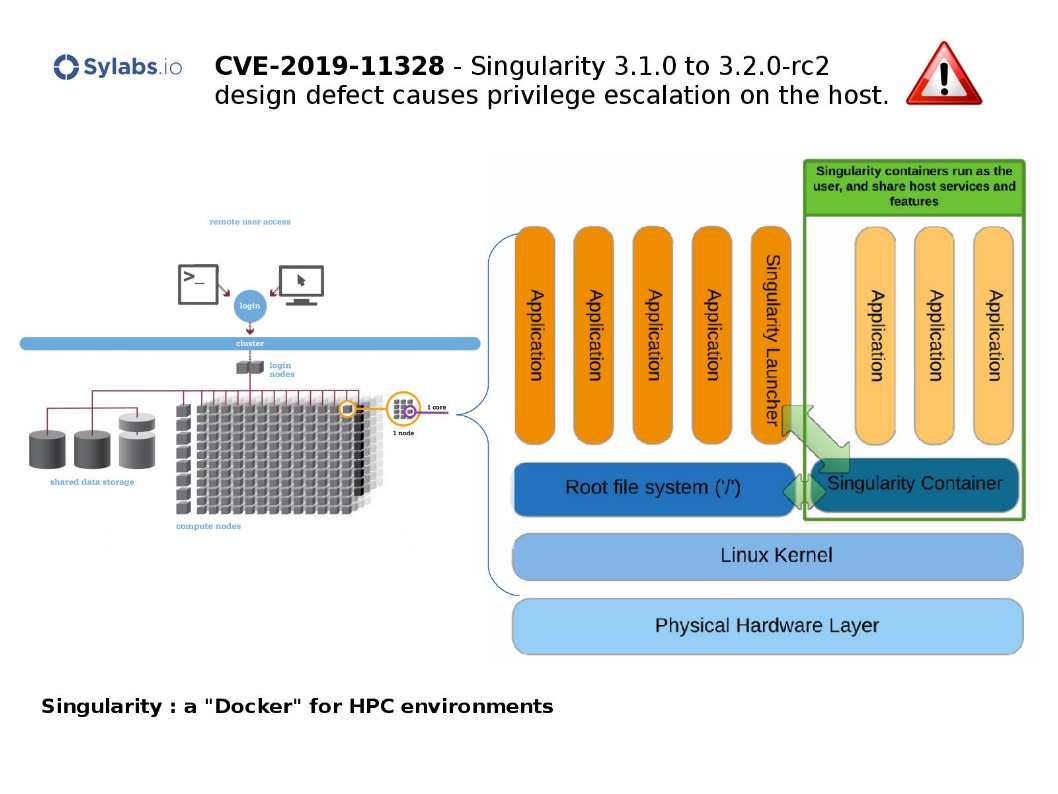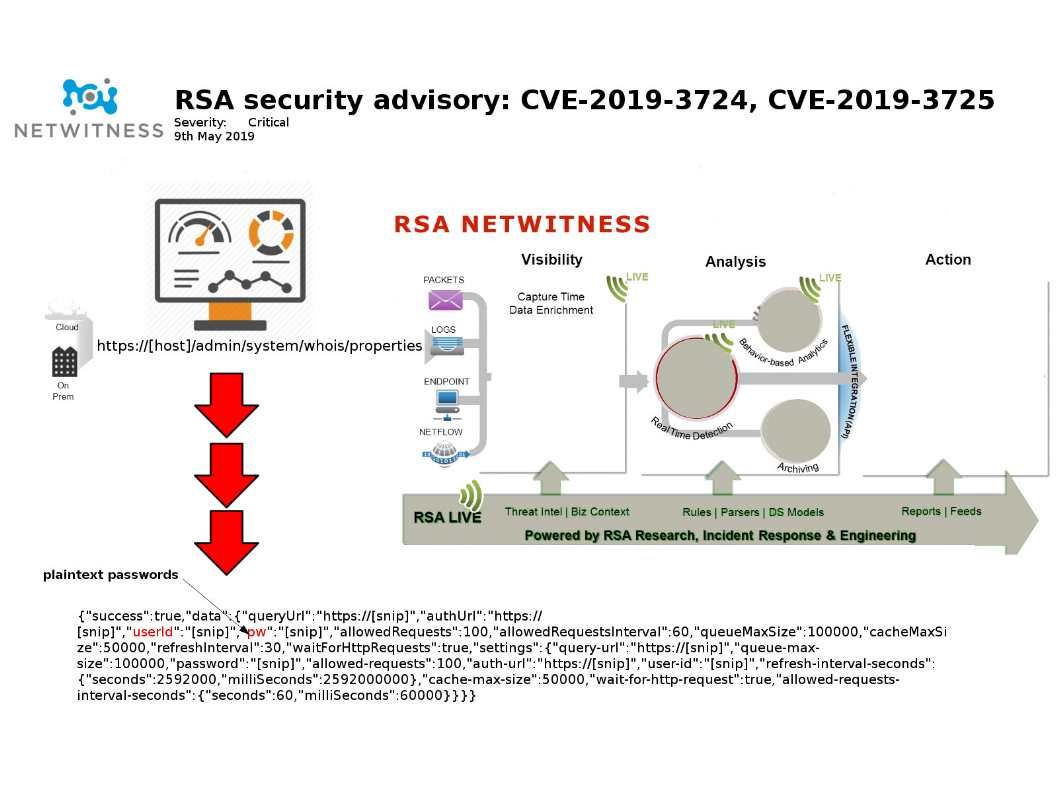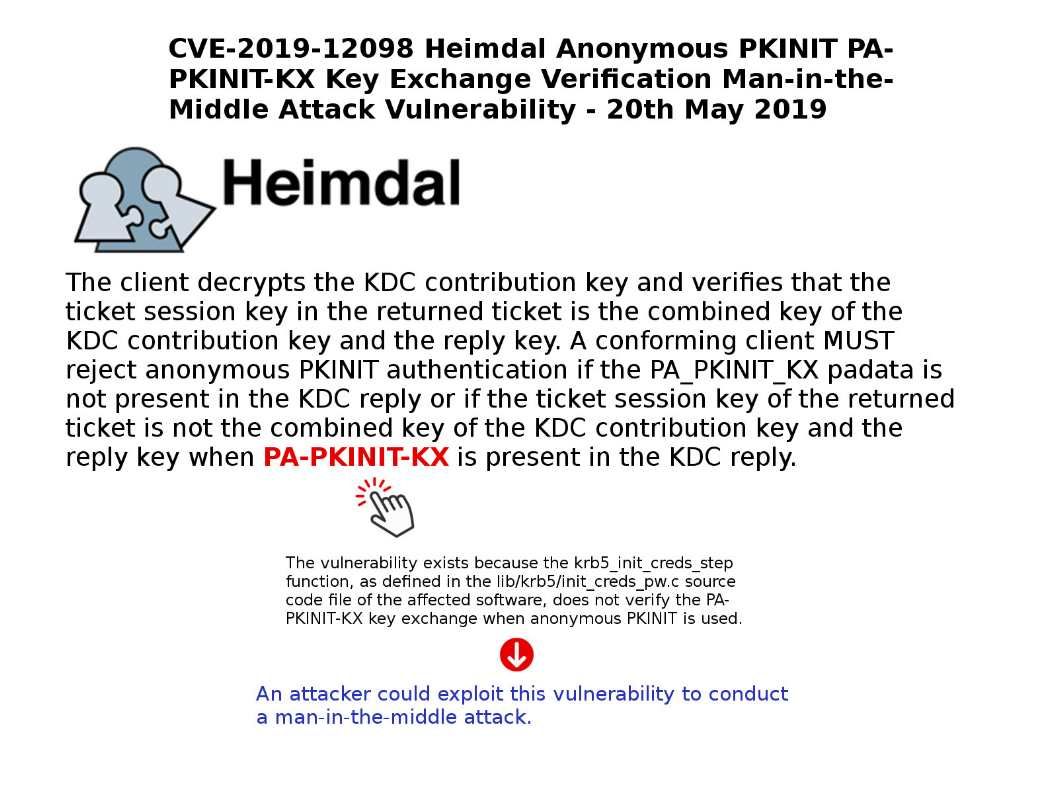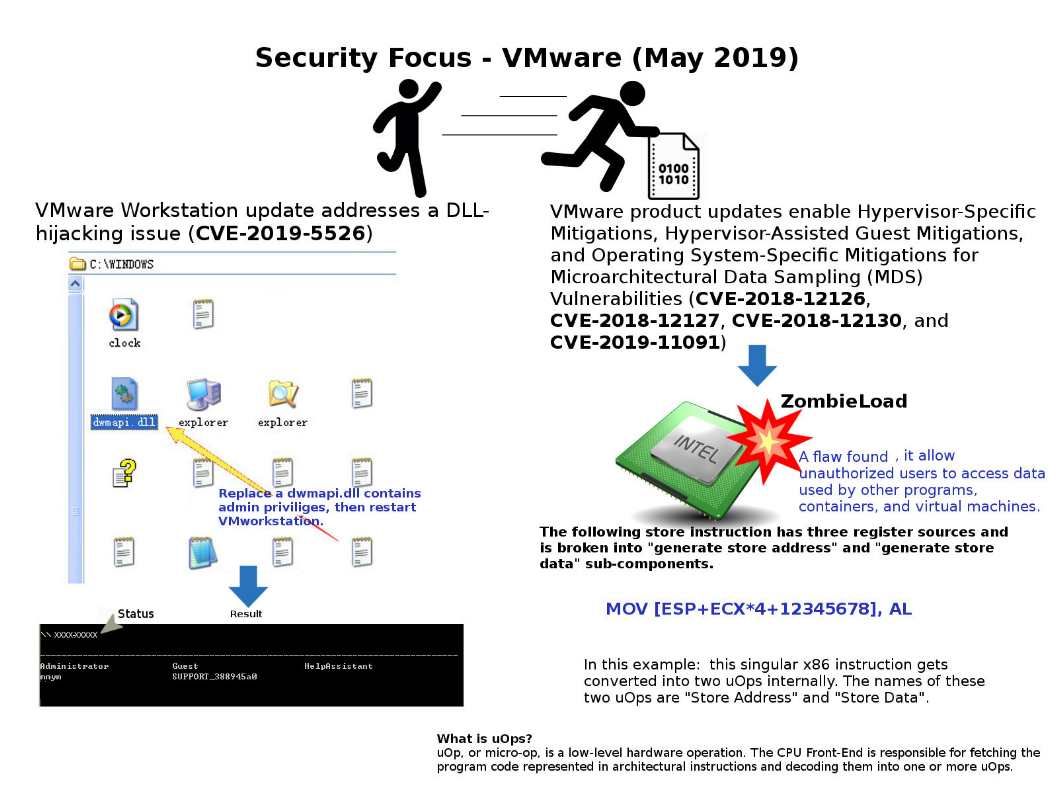
Preface: If the victim of cybersecurity is a defensive device? What you can do?
Background: Leading players in the Global It Asset Management (Itam) Software Market Research Report are: HP, Cherwell Software, Oracle & Dell KACE .
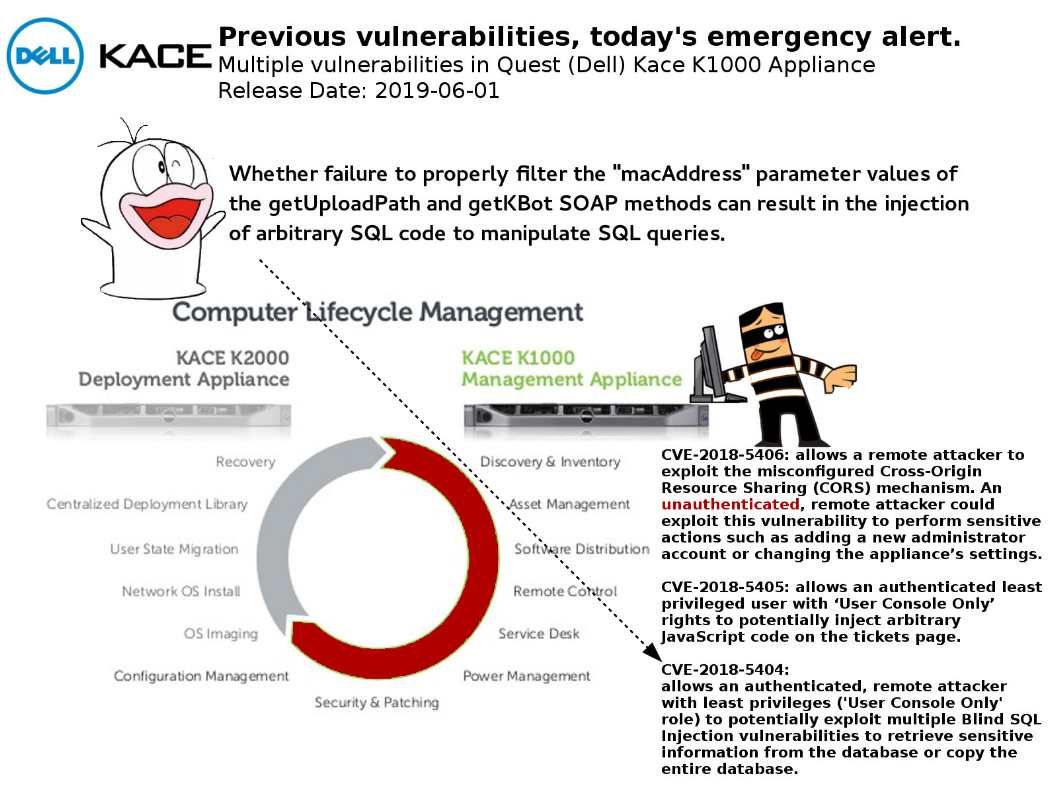
Vulnerability details: The Dell Kace K1000 Appliance contains multiple vulnerabilities, including a blind SQL injection vulnerability and a stored cross site scripting vulnerability.
Comment: As usual, vendor did not provide the vulnerability details. For SQL injection vulnerability. Seems has similarity of the previous vulnerability, see below:
Failure to properly filter the “macAddress” parameter values of the getUploadPath and getKBot SOAP methods can result in the injection of arbitrary SQL code to manipulate SQL queries.
Remedy: Apply patch (SEC2018_20180410) NOTE: KACE SMA versions 9.0.270 and later include these security fixes.