Preface: Business computing architecture now go to virtualization world, perhaps it is hard to imagine in five year ago!
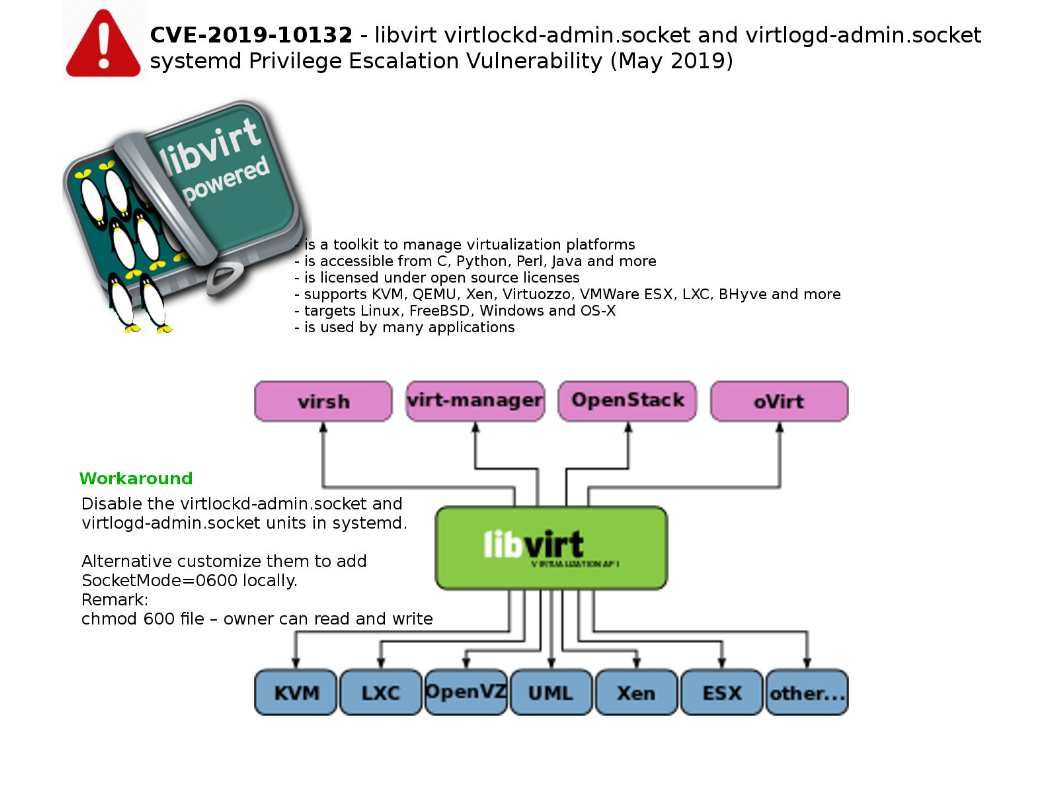
Technical background: The libvirt library is used to interface with different virtualization technologies. It is accessible from C, Python, Perl, Java and more. Meanwhilethe libvirt project supports KVM, QEMU, Xen, Virtuozzo, VMWare ESX, LXC & BHyve. Libvirt’s built-in API is widely used in the virtual machine monitor orchestration layer in cloud solution development.
Vulnerability details: A vulnerability in libvirt could allow an authenticated, remote attacker to escalate privileges on a targeted system. The vulnerability exists because the virtlockd-admin.socket and virtlogd-admin.socket unit files do not set the SocketMode configuration parameter in the affected software.
Workaround: Disable the virtlockd-admin.socket and virtlogd-admin.socket units in systemd. Alternative customize them to add SocketMode=0600 locally.
Remedy: libvirt has released software updates at the following link – https://github.com/libvirt/libvirt/releases