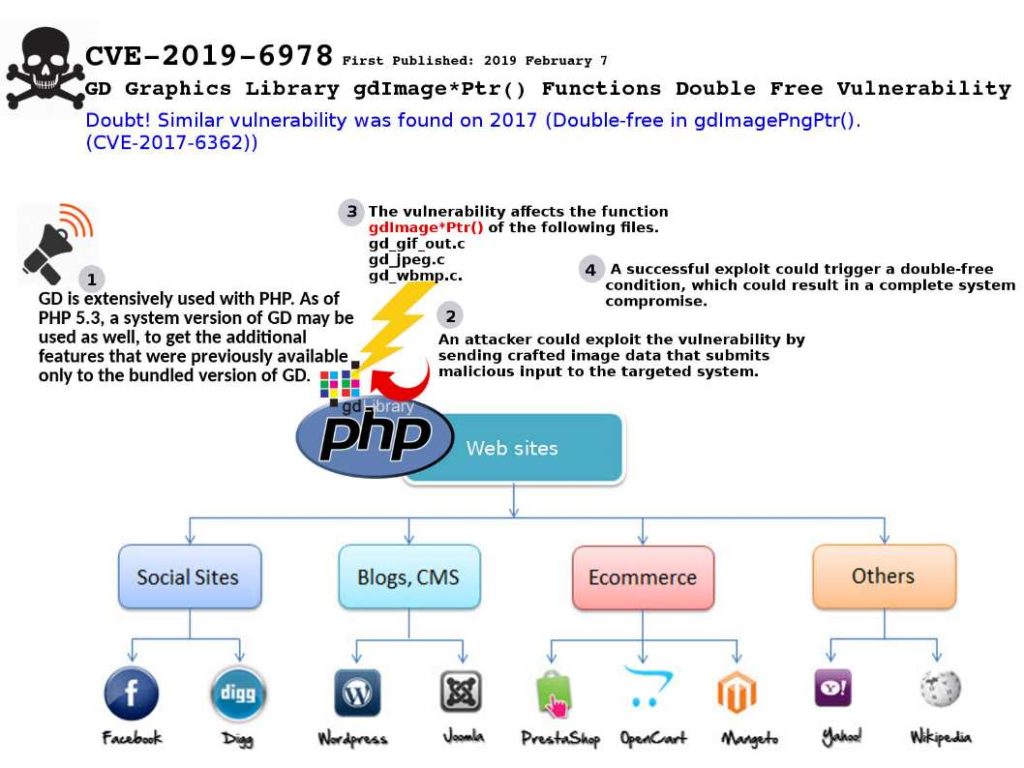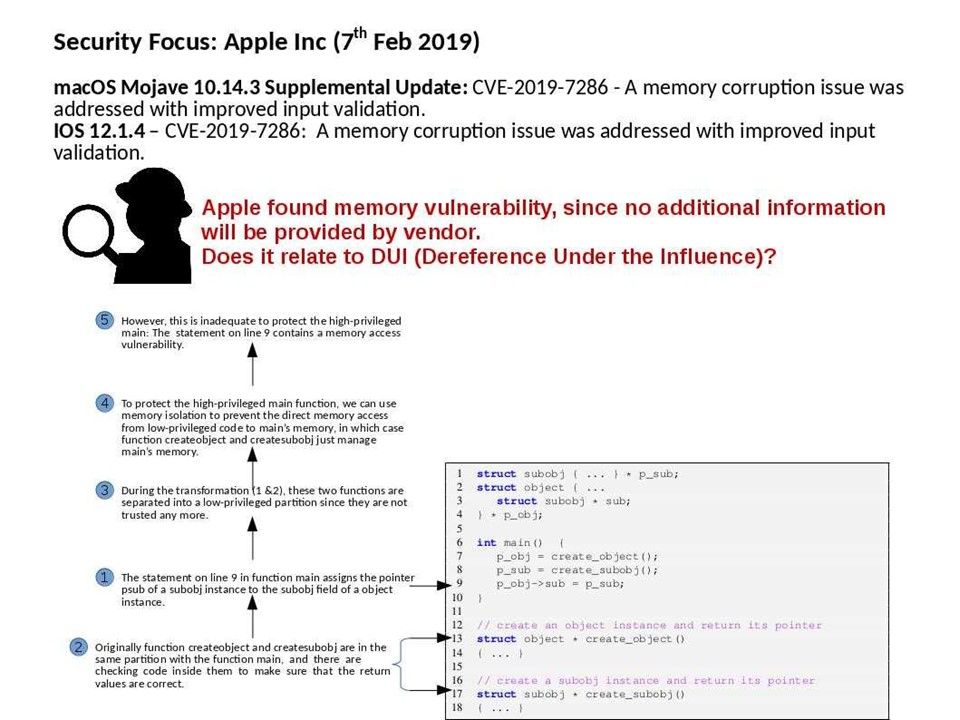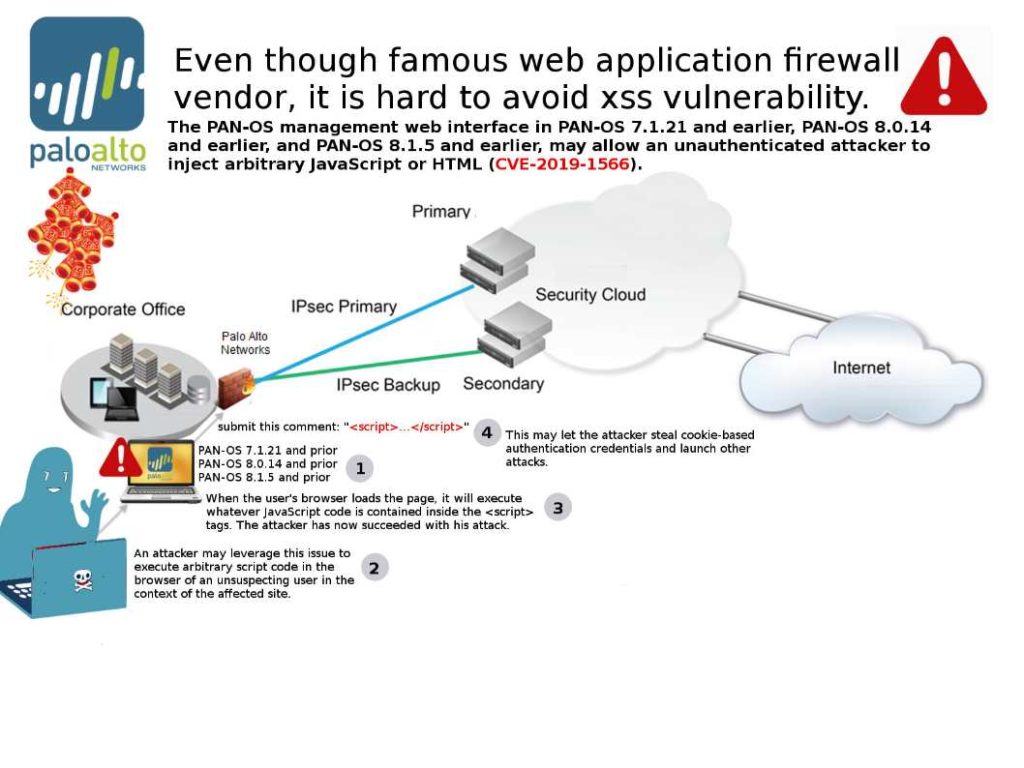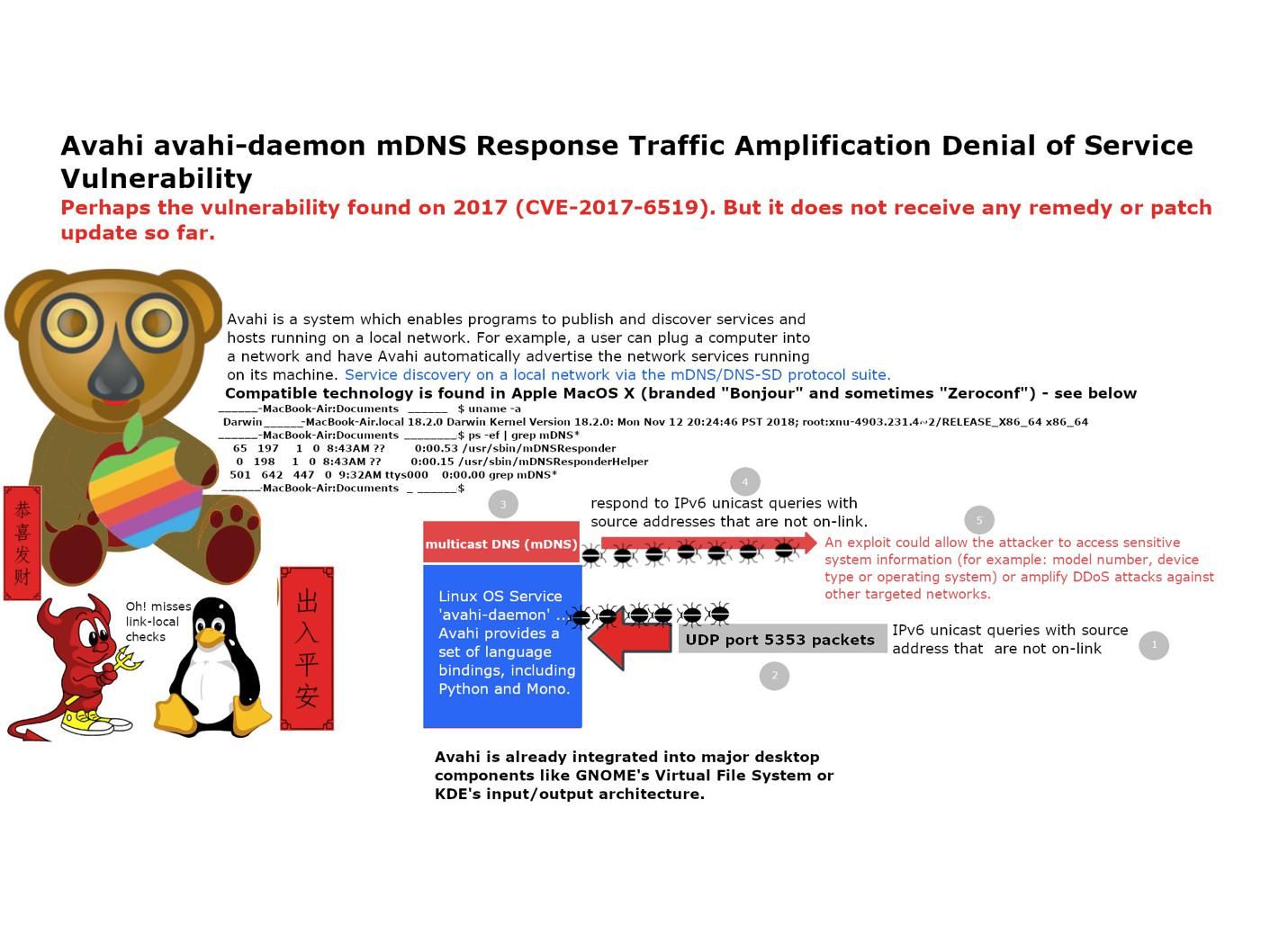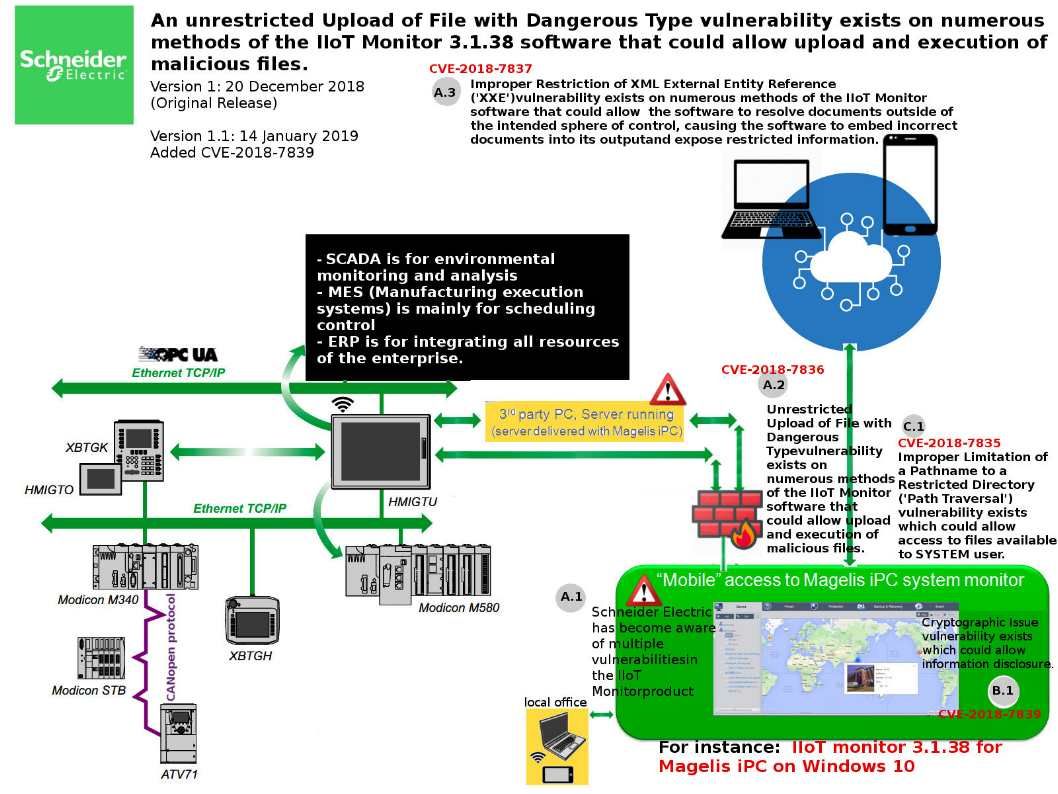
Preface: Cisco MSE is distributed as an Open Virtual Appliance (OVA) for installation on a virtual appliance and as an ISO image for installation on a physical appliance. Cisco MSE acts as a platform (physical or virtual Cisco Mobility Services Engine [MSE] appliance) to deploy and run the Cisco services.
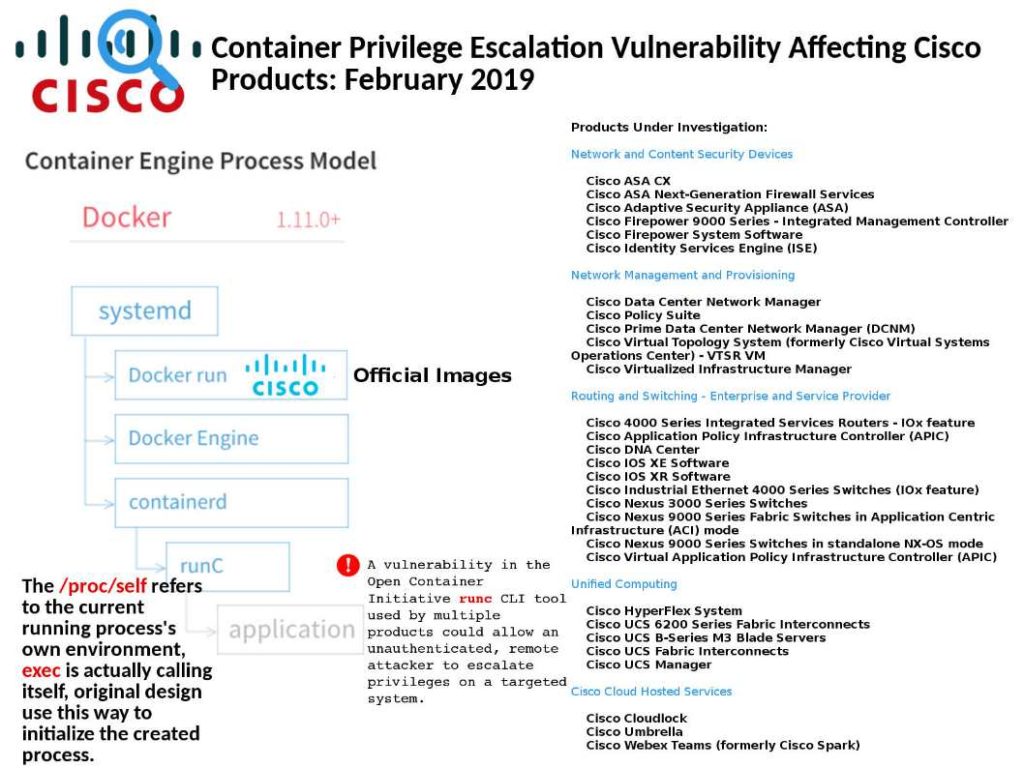
Open Container Initiative overview:
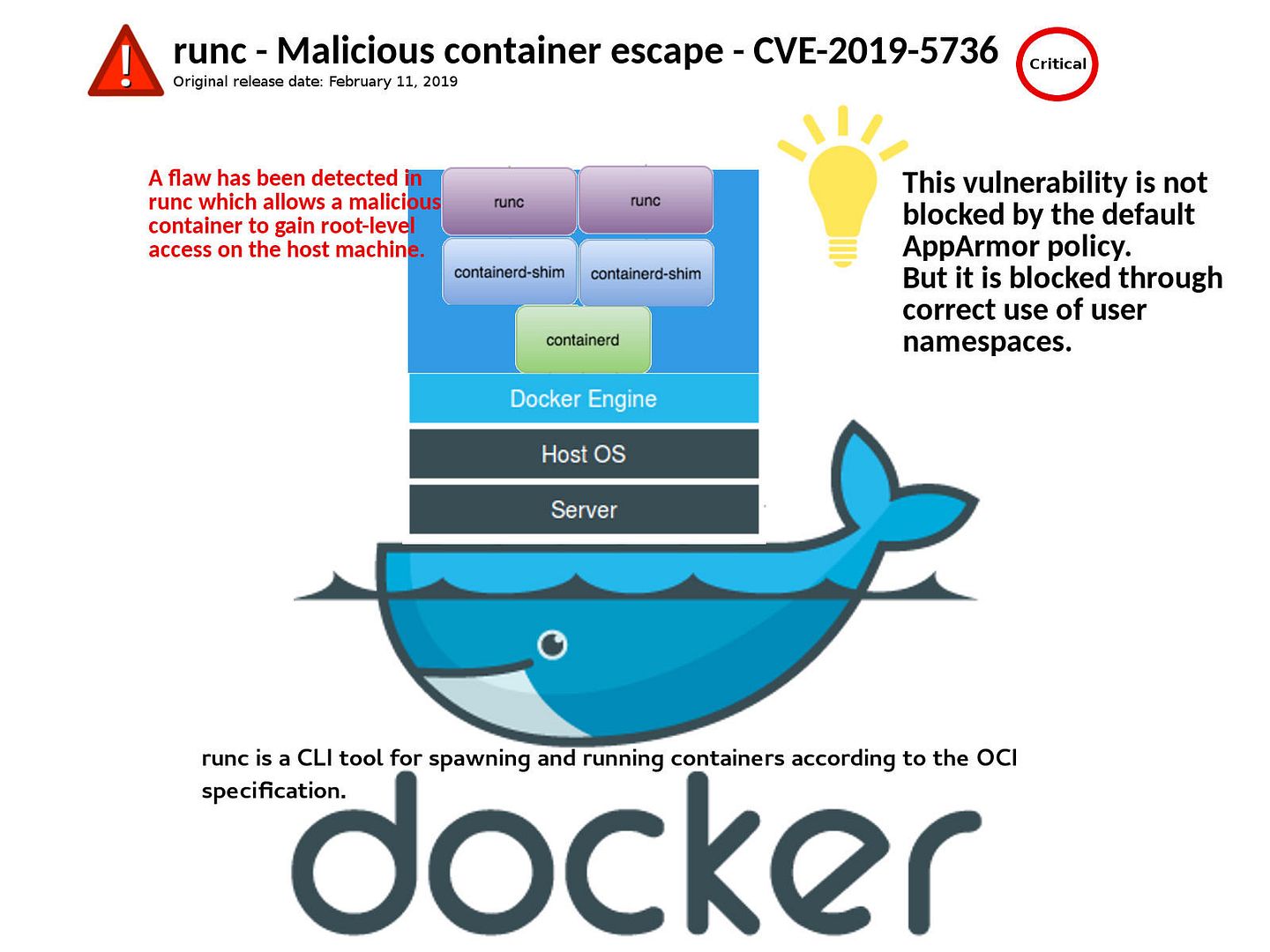
OCI currently contains two specifications: the Runtime Specification (runtime-spec) and the Image Specification (image-spec).
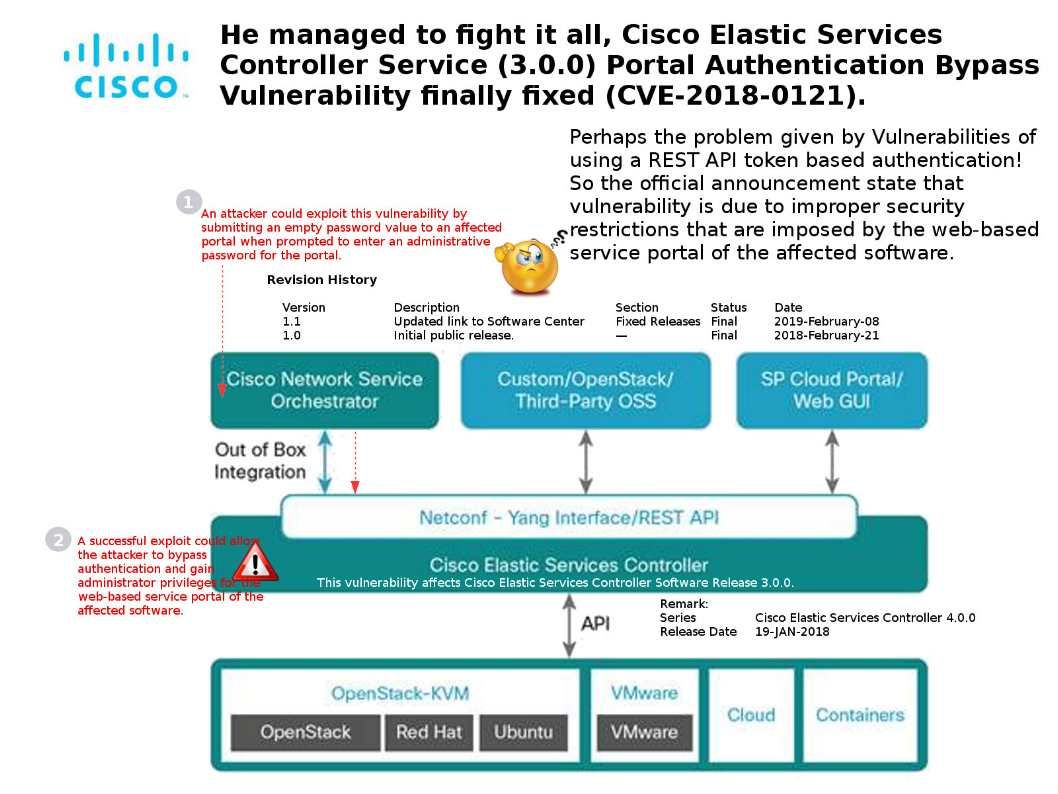
Cisco worries that OCI flaw will be affecting his Products:
The /proc/self refers to the current running process’s own environment, exec is actually calling itself. When flaw allow someone improperly handles file descriptors related to /proc/self/exe. In the sense that attacker similar escalate privileges on a targeted system.
For more details, refer below Official announcement: https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190215-runc