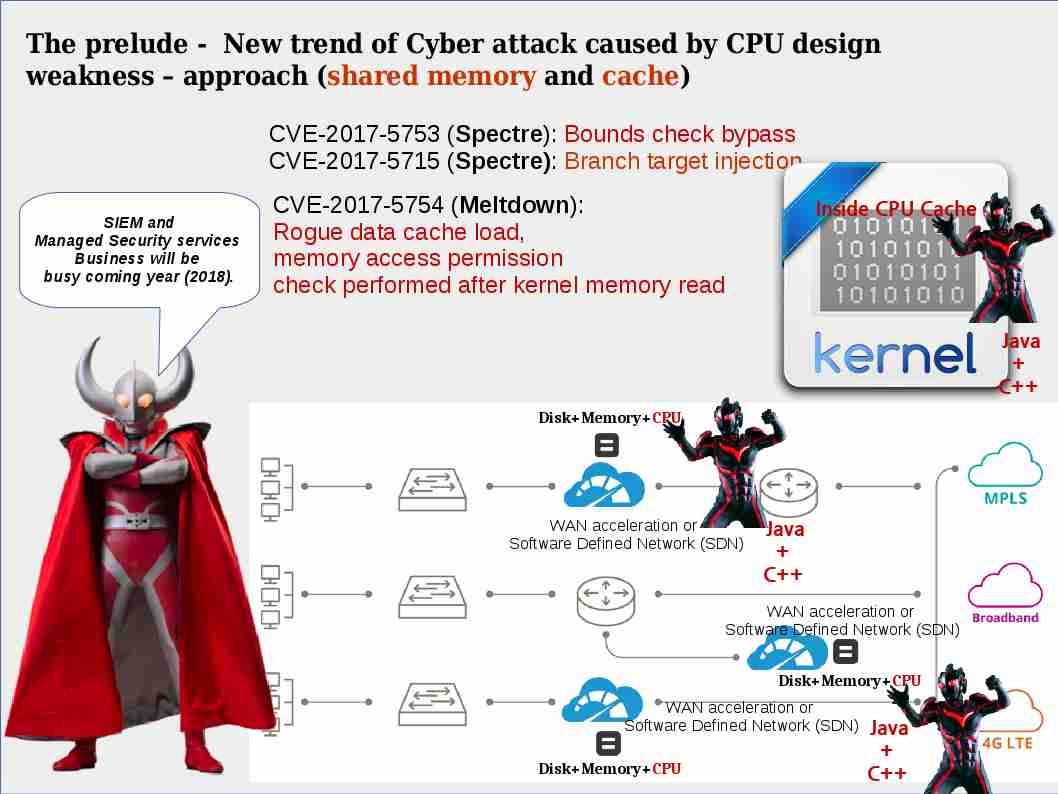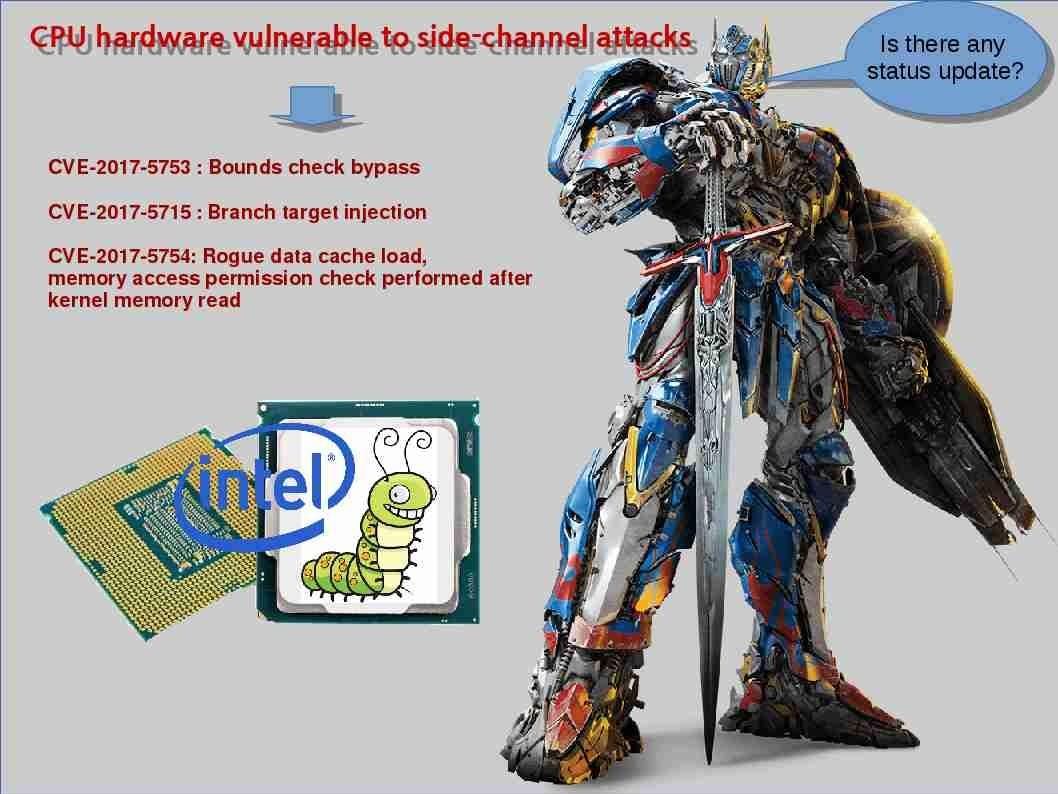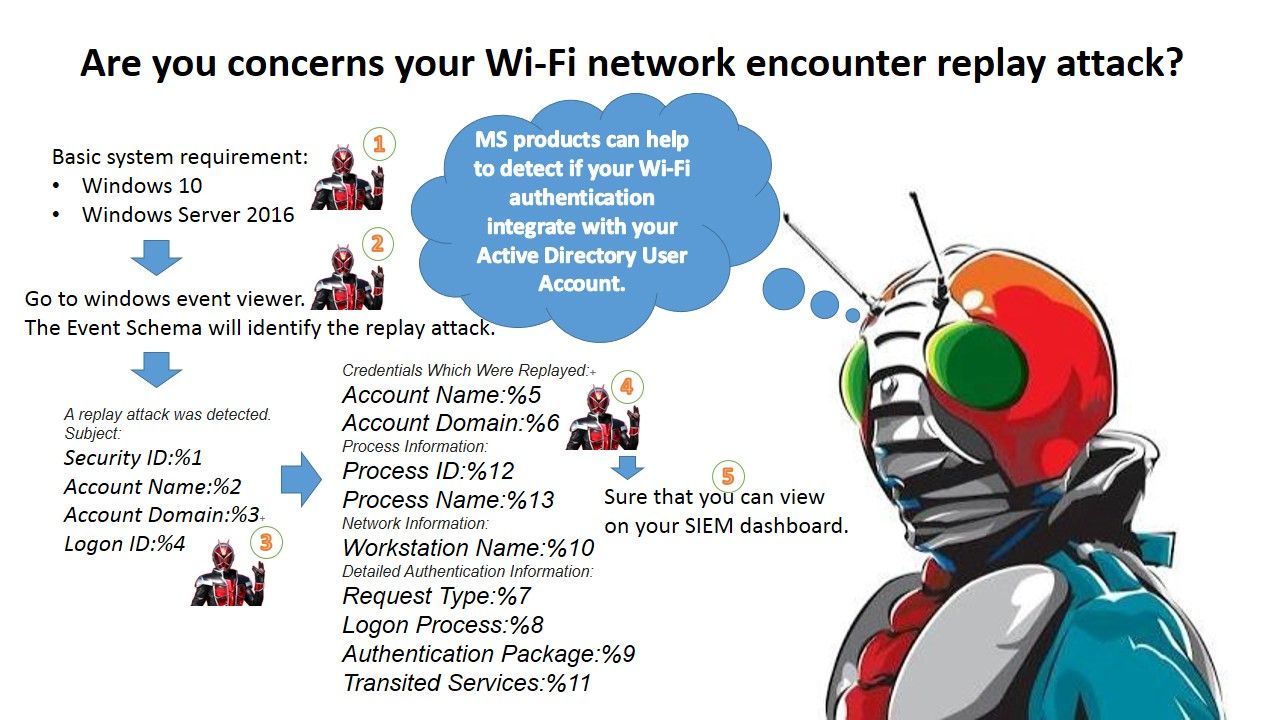
Perhaps Meltdown and Spectre CPU design weakness headache the IT guy this month. Sounds like the overall environment covered with mist! But the sunrise will be raised finally to get rid the dark. Can you remember that replay attack on WPA2 Wifi network last year? You did OS version upgrade and change the authentication method because of this incident. No matter hardware and software, the IT product life cycle is short today. In the meantime, Microsoft can help you to do the detection of this attack if your Wi-Fi network authentication integrate with Active Directory. You are able to verify the details on event viewer or make use of your SIEM Dashboard to review the details. For more details, please see below url provided by Microsoft for reference.
4649(S): A replay attack was detected:
https://docs.microsoft.com/en-us/windows/device-security/auditing/event-4649