
Preface
The deluge push the earth to next generation. The scientists found Noah’s Ark fingerprint on top of the hill in India. The tremendous trend of the cryptocurrency (Bitcoins) like deluge. It such a way change the financial industry framework.
The fundamental technology concept
What is the difference in between blockchain and hyperledger?
A consensus of the blockchain technology foundation have the following idea. The blockchain technology feature better implement in public ledger that is crypto currencies. Hyerledger should have benefits to business industries. Since the fundemental of the cryptocurrencies concept is a direct electronic payment.The specific technology objectives encryption and integrity of the record (it cannot counterfeit), once the block is use it cannot be use reuse anymore.
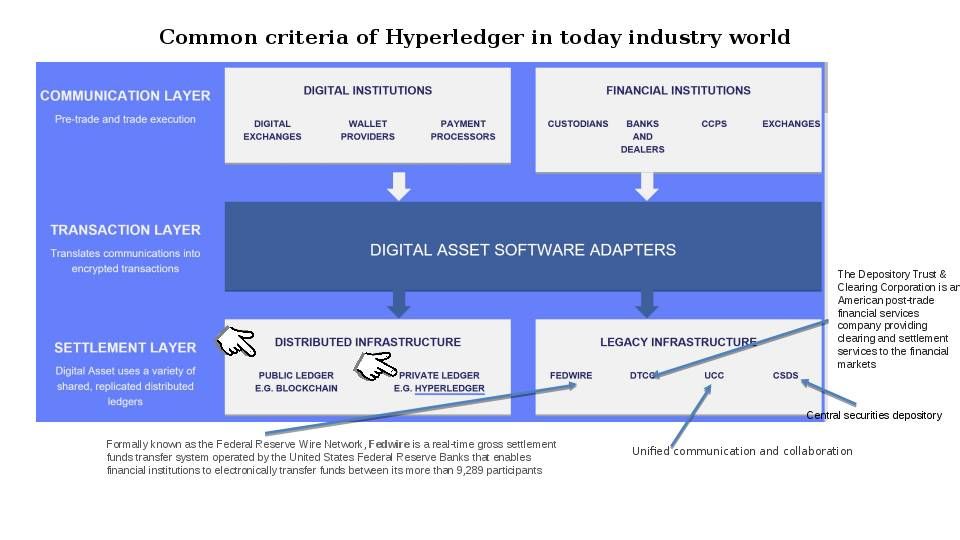
As times go by, the cyber attack incidents on IT technology world bring the enhancement idea to blockchain technology. In order to cope with on-going technology and business perspective. Blockchain technology transform the technology focus to enhance its framework structure. And therefore hyperledger was born.The most popular hyperledger framework models are the following models.
Refer to the Hyperledger Modular Umbrella approach. Each Hyperledger framework empower different advanced function in order to cope with business industry requirements.
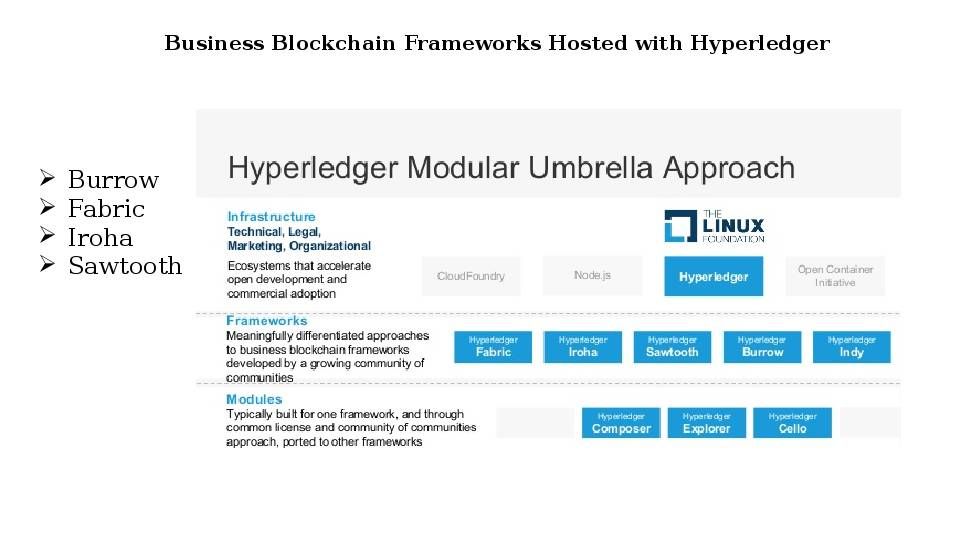
There are total 5 different framework of approach.
Burrow Framework
Provides a modular blockchain client with permissioned smart contract interpreter partially developed to the ethereum virtual machine (EVM) specification.
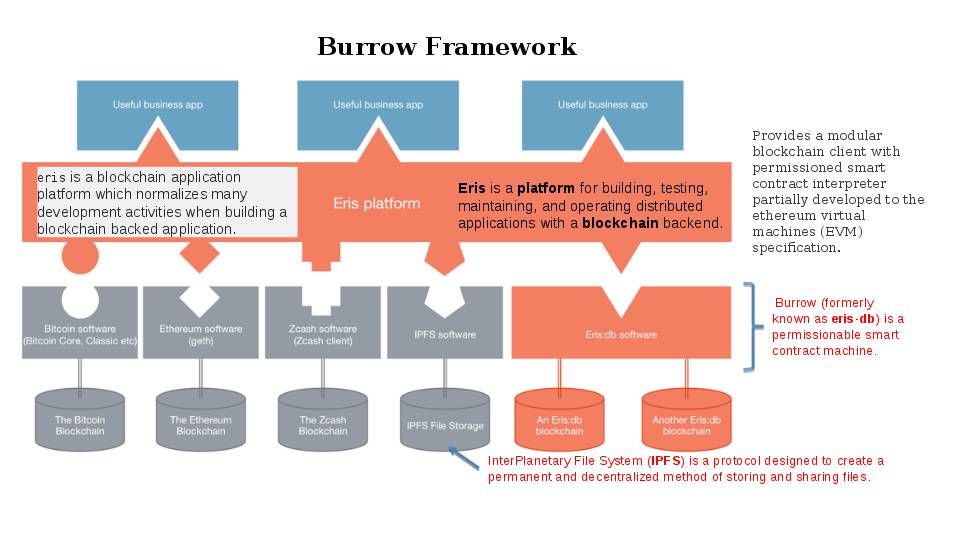
From security point of view: Eris makes use of Docker containers for its services and much of the Eris and Tendermint tooling is written in Go.You’ll need to have at least as many EC2 instances available as you want nodes. Again, you’ll need at least four nodes for the network to operate. If you don’t want to use AWS to host your nodes, you’ll need to have access to hosts that have Go version 1.4.x and Docker version 1.8.x installed. The programming language is Go. This development language not popular but it is secure. But it is hard to find programmer familiar with GO programming background.
Observation: (CVE-2016-3958/CVE-2016-3959) Untrusted search path vulnerability in Go before 1.5.4 and 1.6.x before 1.6.1 on Windows allows local users to gain privileges via a Trojan horse DLL in the current working directory, related to use of the LoadLibrary function (CVE-2016-3958).
Iroha
An blockchain framework designed for simple and easy incorporation into infrastructure projects requiring distributed ledger technology.
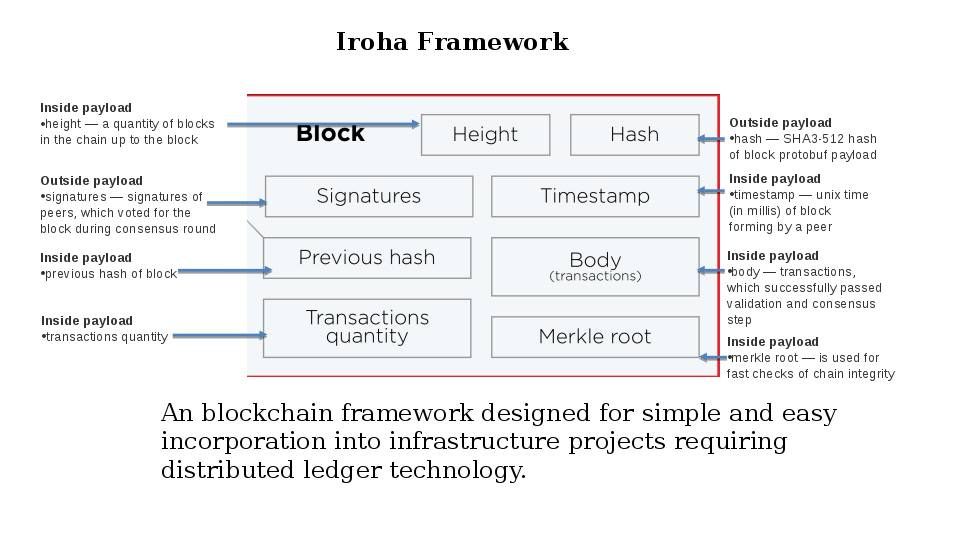
From security point of view: Since Iroha framework contains the following features:
- Creation and management of custom complex assets, such as currencies or indivisible rights, serial numbers, patents, etc.
- Management of user accounts
- Taxonomy of accounts based on domains — or sub-ledgers in the system
- The system of rights and verification of user permissions for the execution of transactions and queries in the system
- Validation of business rules for transactions and queries in the system
Comparing the actual functions (see below diagram). My comment is that the integrity check looks run in precise way on each transaction. Iroha try to improve the anti-tamper solution of the data. The fundamental design concept of Iroha focuses on Blockchain-based Data Management.
Observation: Since Iroha focuses on blockchain based data management. How about the end point protection? It looks the design did not provide a clear visibility on the end point.
Remark: The Iroha project is a bit of an outlier within Hyperledger. It originated with some developers in Japan who had built their own blockchain technology for a couple of mobile use cases. It’s implemented in C++ which can be more high performance for small data.
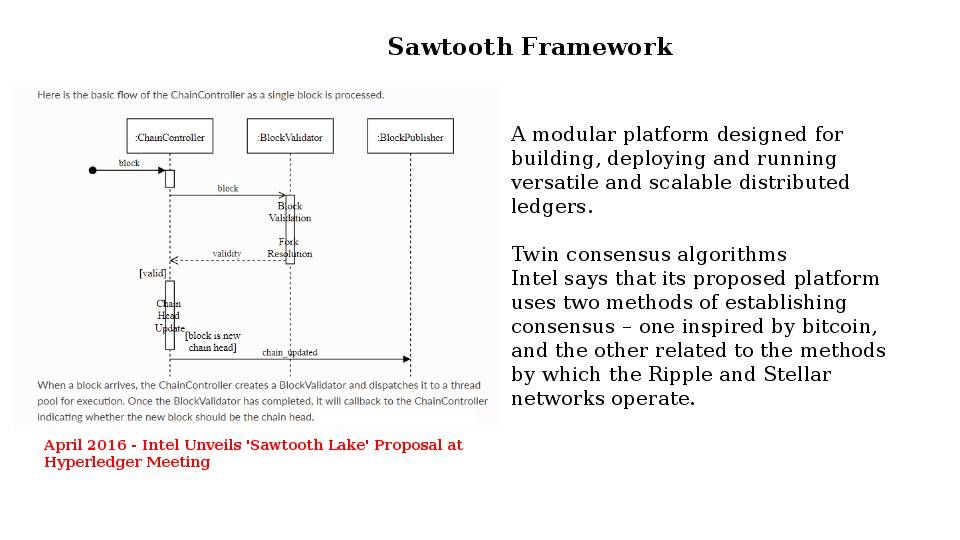
A modular platform designed for building, deploying and running versatile and scalable distributed ledgers. Heard that the Sawtooth consensus software targets large distributed validator populations with minimal resource consumption. “It may give us the ability to build very broad and flat networks of hundreds to thousands of nodes,” said Behlendorf. “It’s harder to do with traditional consensus mechanisms without having the CPU burden of cryptocurrencies.”
From security point of view: No conclusion at this moment.
Fabric Framework
An implementation of block chain technology intended as a foundation for developing blockchain application or solutions. Fabric is Hyperledger’s most active project to date. Hyperledger Fabric intends to offer a number of SDKs for a wide variety of programming languages. The first two delivered are the Node.js and Java SDKs.
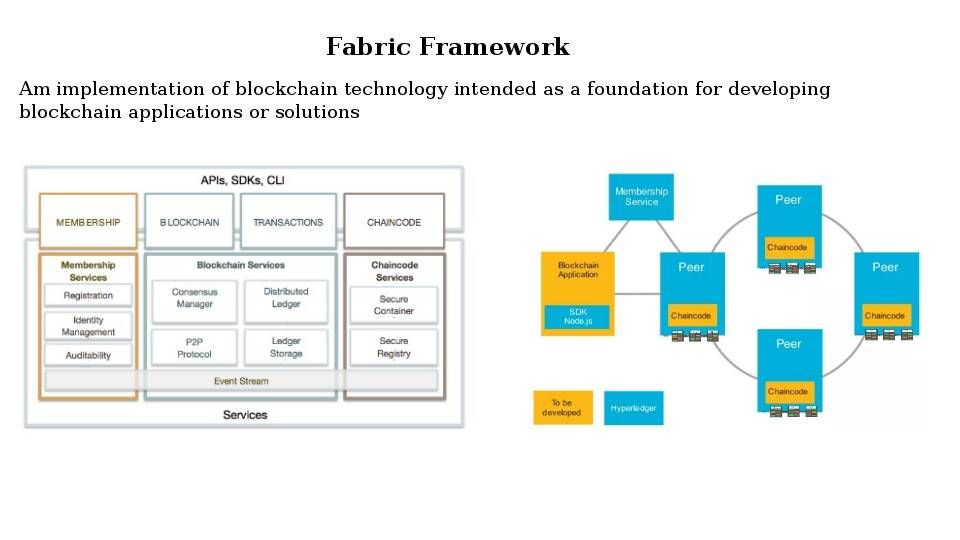
From security point of view: Since the first two delivered are the Node.js and Java SDKs. In order to avoid the denial of service or avoid unauthenticated attacker with network access via Kerberos to compromise Java SE, Java SE Embedded. It is better to make use of GO for application development in future.
Below details are the recently vulnerabilities occurred on above 2 programming languages for reference.
http://www.cvedetails.com/cve/CVE-2017-10388/
https://nodejs.org/en/blog/vulnerability/oct-2017-dos/
Indy
Sovrin is a specific deployment of the Hyperledger Indy codebase. Sovrin developed the Indy code base as part of its mission to build a global public utility for self-sovereign identity. Sovrin Foundation contributed the code to Hyperledger under the Hyperledger Indy brand to expand the developer community and allow greater participation. But Sovrin and Indy are distinct. Sovrin is a specific, operating instance of the Hyperledger Indy code that contains identities that are interoperable at the global scale.
Remark: The best way to start develop Sovrin would be with the Indy SDK. (Indy is the technology under Sovrin, and its SDK provides a C-callable library.

From security point of view: Vulnerability (Slow nodes can be stalled after a view change)
Description – The election process needs to communicate what is the transaction and state root hash apart from the last ordered Pre-Prepare sequence number
Detail explanation: What if A is malicious, and C and D during a catch up get inconsistent catchup messages from A and B? Perhaps the PRIMARY declaration message needs a root hash, and f+1 consistent responses for both Last Ordered Batch number AND Txn Root Hash
Remedy: The election process needs to communicate what is the transaction and state root hash apart from the last ordered Pre-Prepare sequence number.
Summary:
IT security from 90’s encountered virus infection till today malware infection causes data breach. The appearance of blockchain (hyperledger technology) goal to mitigation the data leakage issue. The design objective of the data encryption is going to protect your data. As of today, an advanced technology enhanced server side and data storage. Block chain technology breakthrough traditional key algorithm encryption. The hash encryption technique and blockchain (accumulate) (N+1) data encryption scheme awaken the world. However the product design limitation let hacker exploit the vulnerabilities and such away expand the risk to application layer including programming language. On the other hand a hidden factor in client side (end point) looks without significant improvement. Apart from that the smartphone geometric level of growth . So, I forseen that information technology world requires a new revolution to end point platform. See whether there is a new concept of client platform technology announces tomorrow?
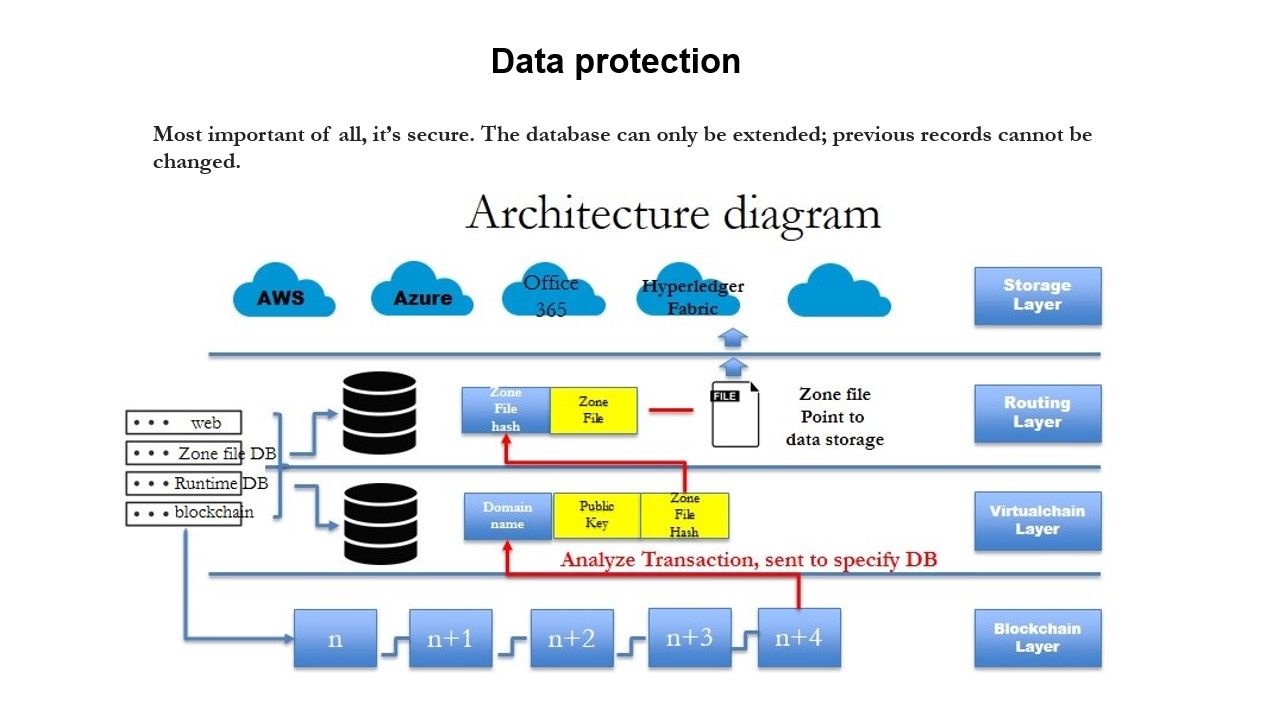
Note: AWS, Azure and Office 365 are ready for Blockchain (hyperledger) services (see above diagram). Be a innovative IT management. Don’t wait. Now please try to jump to Blockchain (hyperledger) services. You will love it!
Status update 19th Feb 2018 – The deluge push the earth to next generation.Bitcoin and hyperledger technologies such a way transform their new generation to the financial business world. Dubai a former big brother leading the natural resources supply to the world especially petroleum. Now they are keen to leads bitcoin and hypledger technologies. I wishes of their success. See whether what is the new technique can be renovate the blockchain and hyperledger world.
We stumbled over here different web address and thought I might as well check things out. I like what I see so now i am following you. Look forward to looking into your web page again.|
I like this site because so much useful stuff on here : D.
Please let me know if you’re looking for a article author for your weblog. You have some really great posts and I believe I would be a good asset. If you ever want to take some of the load off, I’d absolutely love to write some content for your blog in exchange for a link back to mine. Please send me an email if interested. Thanks!
Nothing relaxes him like reading does.
I believe everything said was very logical. However, what about this? suppose you added a little information? I ain’t saying your content isn’t good, however what if you added something that makes people want more? I mean is kinda boring. You ought to look at Yahoo’s home page and note how they create post titles to grab people to open the links. You might add a related video or a related pic or two to grab readers interested about everything’ve got to say. Just my opinion, it might make your posts a little livelier.
I added a new list. As you’ll see it’s bigger than most of them. I hope you all have had a great week!
Howdy! This is my first comment here so I just wanted to give a quick shout out and tell you I really enjoy reading your articles. Can you recommend any other blogs/websites/forums that deal with the same topics? Thank you!|
After checking out a number of the articles on your web site, I honestly appreciate your technique of writing a blog. I added it to my bookmark site list and will be checking back in the near future. Please visit my website too and let me know your opinion.|
You could certainly see your expertise in the work you write. The world hopes for more passionate writers like you who are not afraid to mention how they believe. All the time follow your heart.|
WOW just what I was searching for. Came here by searching for keyword|
I must thank you for the efforts you’ve put in writing this blog. I am hoping to see the same high-grade content by you in the future as well. In fact, your creative writing abilities has motivated me to get my own, personal site now ;)|
great submit, very informative. I’m wondering why the other specialists of this sector do not understand this. You must proceed your writing. I am sure, you’ve a huge readers’ base already!|