Preface
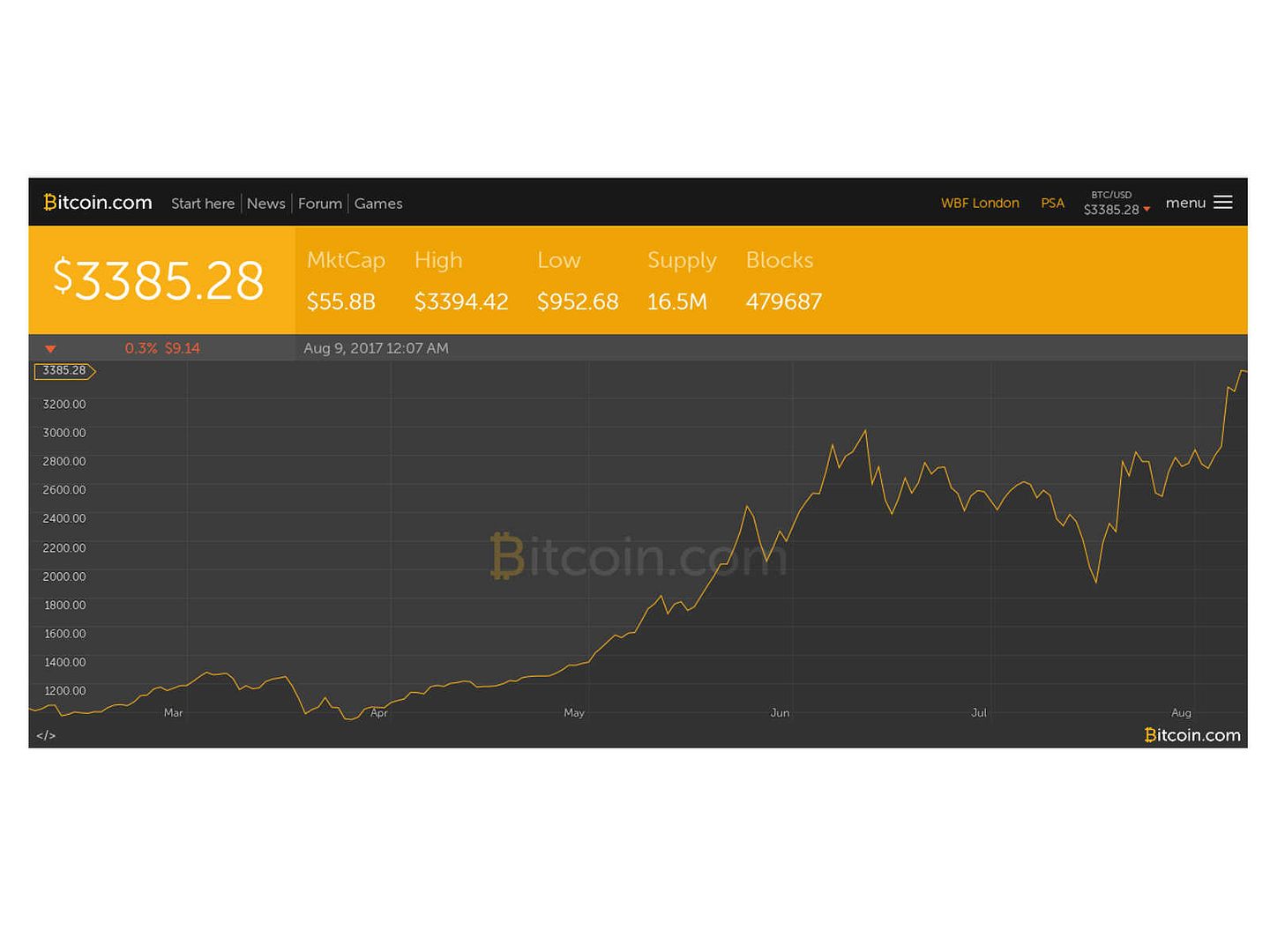
It looks a silent revolution, bitcoin technology spreading to the world. Even though government unsupported this financial tool and proprietary financial firm not accept this technology.
But he is valid in the finance and investment market. As a matter of fact, the activities running strong today (7th Aug 2017).
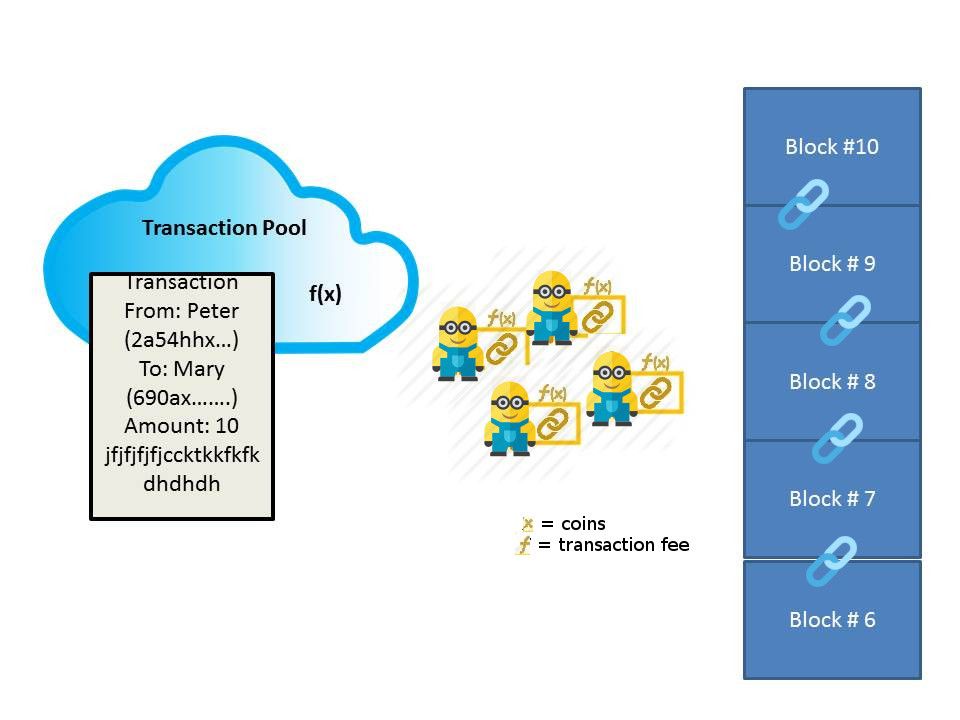
Our earlier study on block chain technology motion
Comparison table:
| Hyperledge | Ethereum | Bitcoin | |
| Association | Linux Foundation | Ethereum Developers | Bitcoin Developers |
| Currency | N/A | Ether | BTC |
| Mining Reward | N/A | Yes | Yes |
| Network | Design goal – Private | Design goal – Public | Public only |
| Privacy | Private | Open | Open |
| Smart Contracts | Multiple-programming language | C++,Rust and Go | i. Bitcoin Core, is written primarily in C++ ii. Lightweight clients like MultiBit and Bitcoin Wallet written in Java |
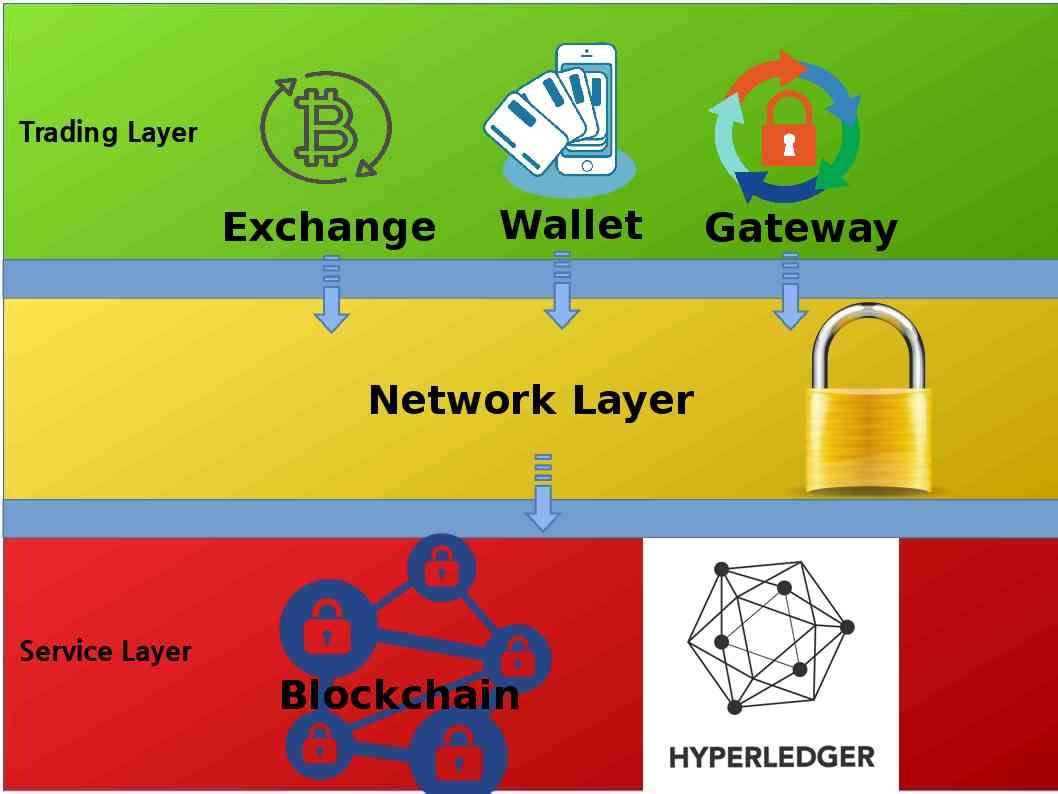
Rouge-et-noir , they are all going to achieve this objective (blockchain or Hyperledger)
The maturity business model of bitcoin today
The fundamental design concept of bitcoin improvement program are based on vote or user input. And therefore Bitcoin is not controlled by any single entity or company. Whereby an improvement program framework has been introduced. It is so called BIP (Bitcoin Improvement Proposal).
Remark 1: A Bitcoin Improvement Proposal (BIP) is a design document for introducing features or information to Bitcoin. The BIP should provide a concise technical specification of the feature and a rationale for the feature. This is the standard way of communicating ideas since Bitcoin has no formal structure. The first BIP (BIP 0001) was submitted by Amir Taaki on 2011-08-19 and described what a BIP is?
Proposal 91
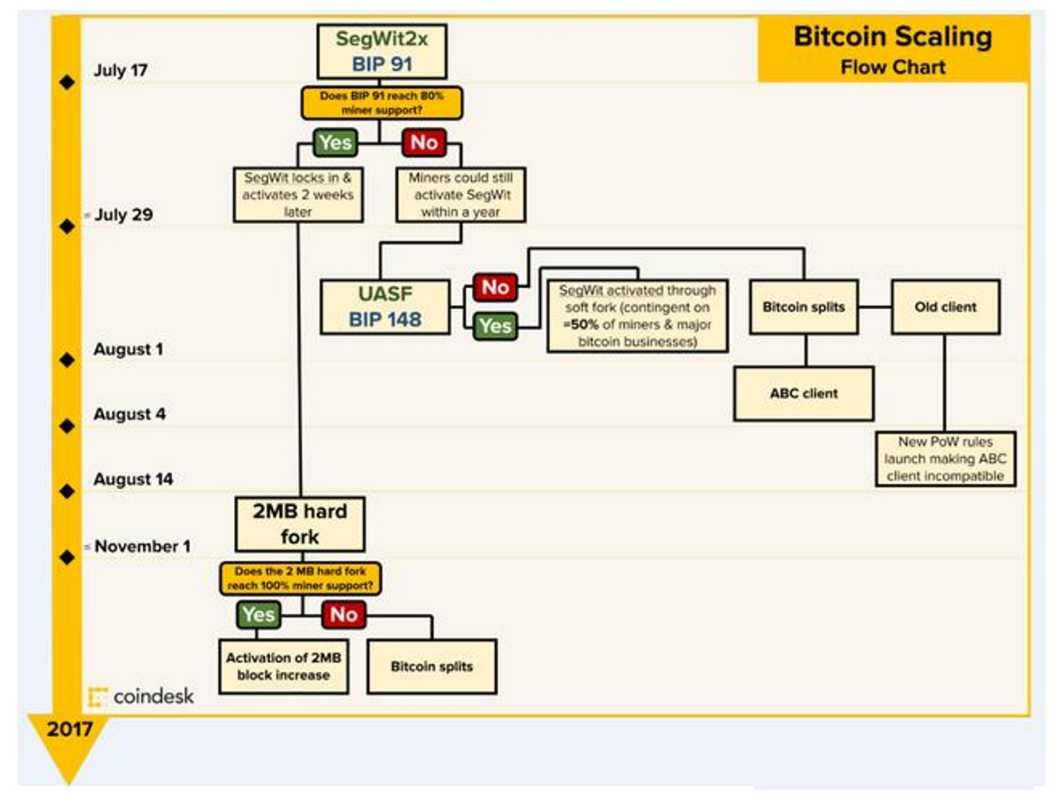
Upcoming Bitcoin activation of Bitcoin Improvement Proposal 91 (BIP 91). Bitcoin Improvement Proposal 91 (BIP 91, also known as Miner Activated Soft Fork) recently locked in over 90 percent of all mining hash power, signaling majority support for this proposal. BIP 91’s lock in effectively makes BIP 148 (User Activated Soft Fork scheduled for August 1) obsolete and discard the chances of the Bitcoin network forking through UASF (User Activated Soft Fork). What is the reason to nullifies UASF?
Bitcoin Possible Crisis, User Activated Soft Fork(UASF BIP-148)-Vulnerability encountered CVE-2017-9230
For more details about the vulnerability, please refer below url for reference
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9230
Bitcoins tell the world, sunrise is on the way.
The Bitcoin Improvement Proposal (BIP) expect to meet the goal on 1st August 2017. The goal is launch of a new coin and Bitcoin Cash (BCC). These coin should include strong replay protection. All you need to do to be able to access your BCC is control your bitcoin (BTC) private keys on this day.
BIP 91 objective – BIP 91 requires 80% of the coin miners to support. Besides, it require to locking SegWit2x’s (SegWit) update on 1st August 2017.
Remark 2: SegWit was proposed by Bitcoin Core volunteers to increase network capacity and solve transaction scalability through soft folk on 2015.
Remark 3: SegWit2x (BTC1): Supported by miners and start-up companies, the proposal aims to develop SegWit through a soft fork.
Breakthrough – below voting status shown that BIT 91 receive miner fully support
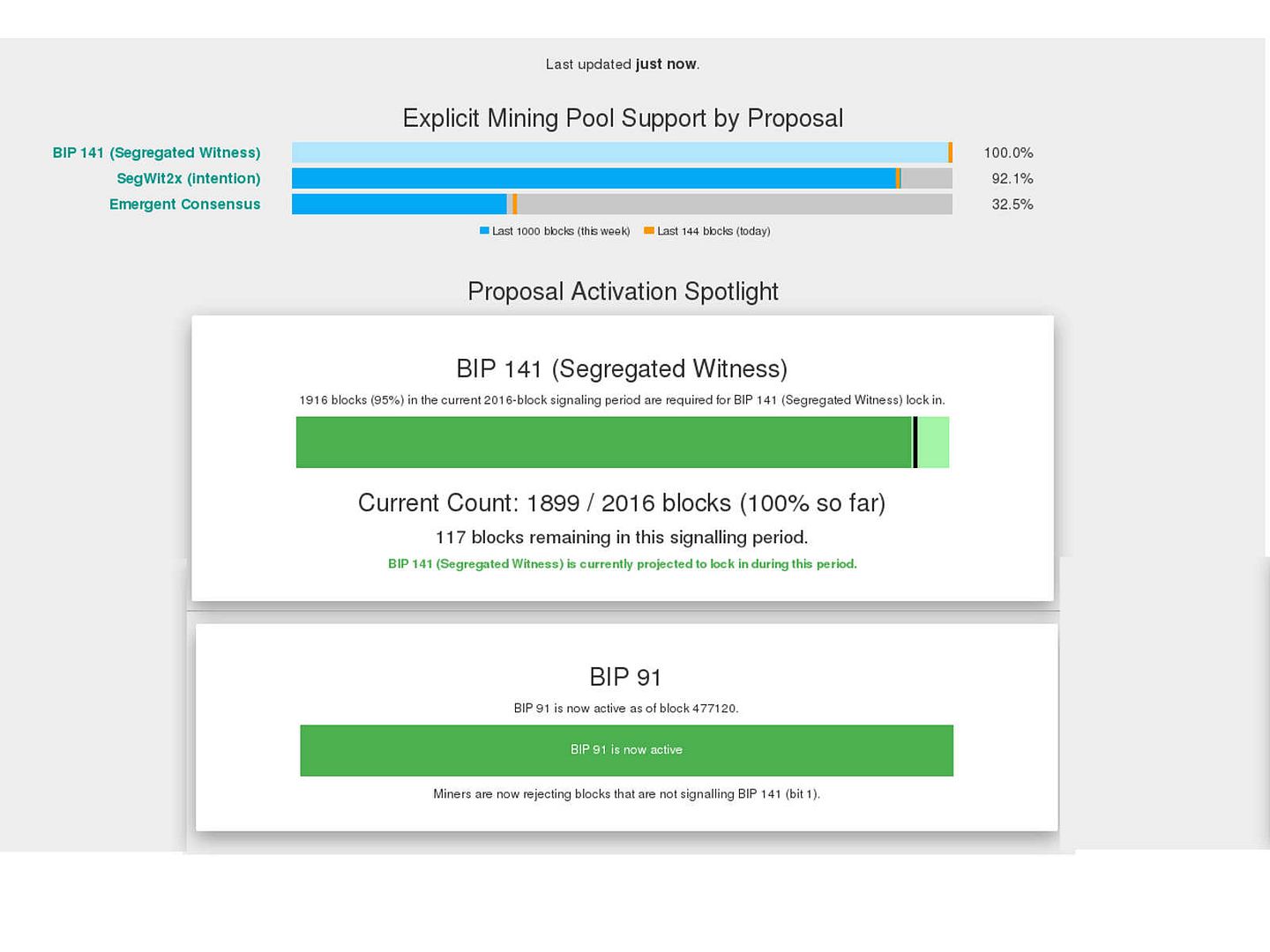
Summary:
As of today, bitcoin looks running strong in the market. We keep our eye open see whether any unforeseen matter happen in coming month.
……..in deo speramus