Preface: CyberArk most likely to be known as a leader in PAM. BeyondTrust more popular among small and medium-sized enterprises.
Background: U-Series is a self-contained physical or virtual appliance that contains the operating system, the database, the BeyondTrust BeyondInsight platform, and the BeyondTrust Password Safe solution.
For a BeyondInsight deployment with a local SQL Server instance, the minimum requirement is 32GB. It is based on Microsoft Windows Server 2022 Standard operating system. The license included with the U-Series v20 and U-Series v20 SQL Free for Microsoft Windows Server 2022 covers up to 16 cores on the physical virtualization (host) server.
Vulnerability details:
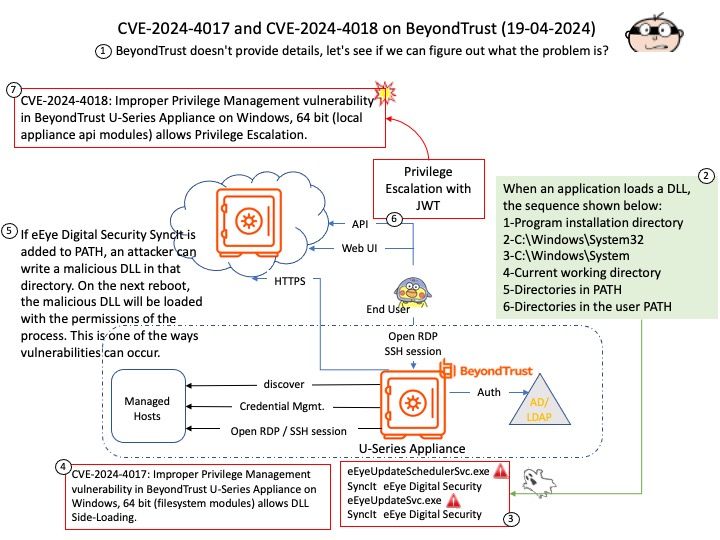
CVE-2024-4018: Improper Privilege Management vulnerability in BeyondTrust U-Series Appliance on Windows, 64 bit (local appliance api modules) allows Privilege Escalation.This issue affects U-Series Appliance: from 3.4 before 4.0.3. Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2024-4018
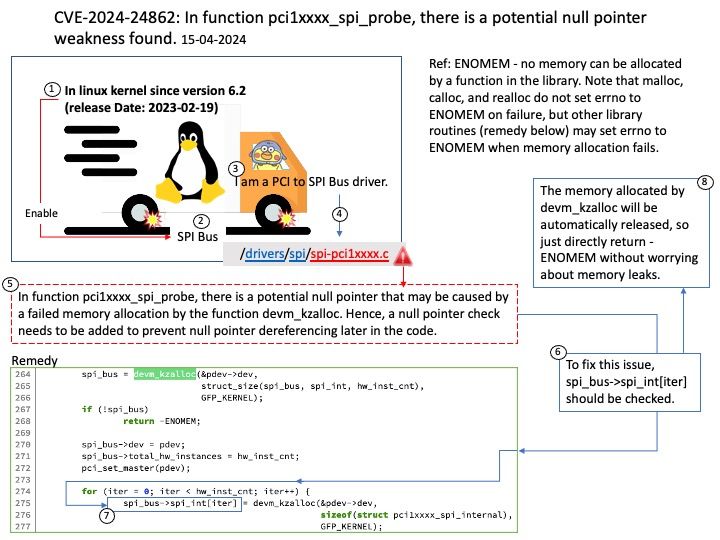
CVE-2024-4017: Improper Privilege Management vulnerability in BeyondTrust U-Series Appliance on Windows, 64 bit (filesystem modules) allows DLL Side-Loading.This issue affects U-Series Appliance: from 3.4 before 4.0.3. Please refer to the link for details –