Preface: Training is the most important step in machine learning. In training, you pass the prepared data to your machine learning model to find patterns and make predictions. It results in the model learning from the data so that it can accomplish the task set.
Background: What is Apache Zeppelin? Apache Zeppelin is an open-source, web-based notebook that enables data visualization, data exploration, and collaborative data analytics. Apache Zeppelin interpreter supports several language backends, including Apache Spark, Python, R, JDBC, Apache Flink, Markdown, and Shell.
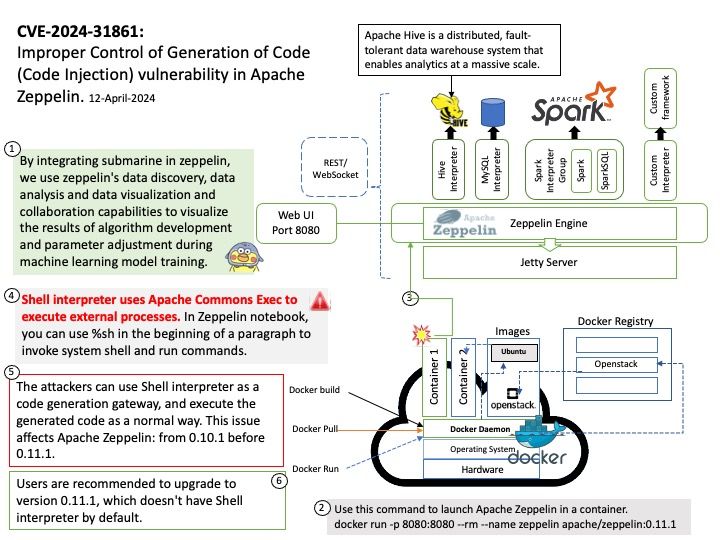
By integrating submarine in zeppelin, we use zeppelin’s data discovery, data analysis and data visualization and collaboration capabilities to visualize the results of algorithm development and parameter adjustment during machine learning model training.
Vulnerability details: Improper Control of Generation of Code (‘Code Injection’) vulnerability in Apache Zeppelin. The attackers can use Shell interpreter as a code generation gateway, and execute the generated code as a normal way. This issue affects Apache Zeppelin: from 0.10.1 before 0.11.1. Users are recommended to upgrade to version 0.11.1, which doesn’t have Shell interpreter by default.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2024-31861