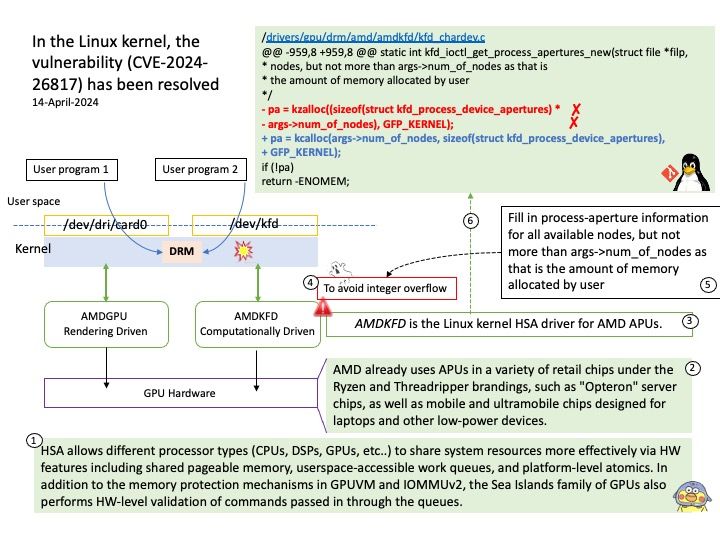
Preface: AMD already uses APUs in a variety of retail chips under the Ryzen and Threadripper brandings, such as “Opteron” server chips, as well as mobile and ultramobile chips designed for laptops and other low-power devices.
Background: As of 2022, AMD Kernel Fusion Driver (KFD) is now integrated in this one kernel module. AMD KFD development at AMD is part of ROCm, under the ROCk project.
ROCm is an Advanced Micro Devices (AMD) software stack for graphics processing unit (GPU) programming. ROCm spans several domains: general-purpose computing on graphics processing units (GPGPU), high performance computing (HPC), heterogeneous computing. It offers several programming models: HIP (GPU-kernel-based programming), OpenMP/Message Passing Interface (MPI) (directive-based programming), and OpenCL.
The calloc() function allocates memory and initializes all bits to zero.
kcalloc — allocate memory for an array. The memory is set to zero.
Vulnerability details: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2024-26817