Preface:
SCADA systems are the backbone of many modern industries, including: Energy, Food and beverage, Manufacturing, Oil and gas, Power, Recycling, Transportation, Water and waste water,….etc
SCADA evolution:
The first generation of SCADA system relies with mainframe computers. As time goes by, the evolutionary of SCADA build on top of open system foundation (Unix) in 80’s. Perhaps the Microsoft product dominate the computer world. And such away engaged the transformation in 90’s. The SCADA software that utilizes the power of SQL databases provides flexibility and advantages to traditional SCADA system.
One big benefit of using SQL databases with a SCADA system is that it makes it easier to integrate into existing MES and ERP systems, allowing data to flow seamlessly through an entire organization.
- (MES) – Manufacturing execution systems are computerized systems used in manufacturing, to track and document the transformation of raw materials to finished goods.
- (ERP) – Enterprise resource planning is the integrated management of core business processes, often in real-time and mediated by software and technology.
Evolving from classic program (non web access) to Web Platform
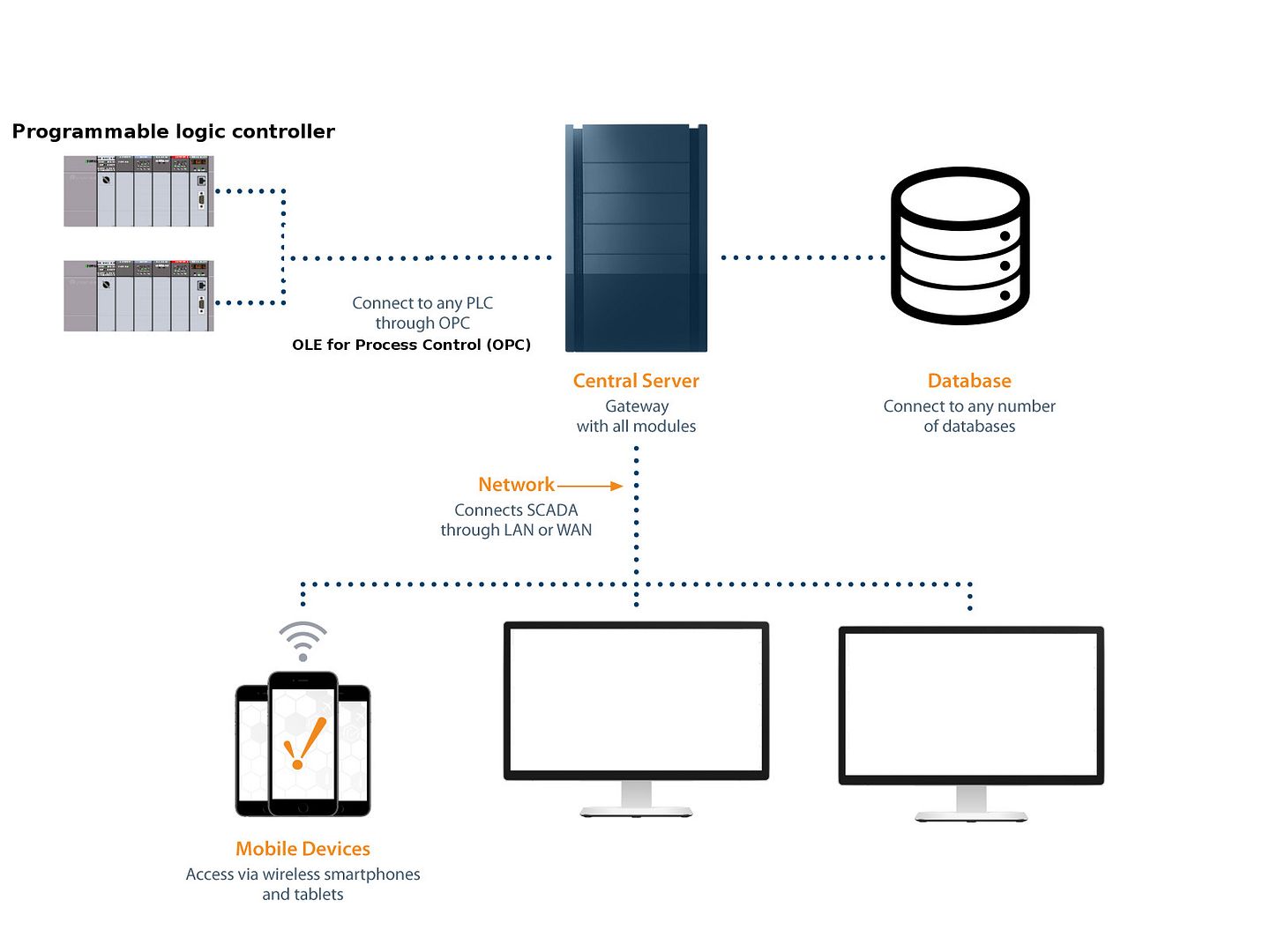
SCADA system on the Cloud (cope with modern technology trend with access anywhere function)
Before we start the discussion in security topic, we do a quick introduction of big-data frameworks. Since the Hadoop and Apache Spark pay the key role on this architecture especially big data function. For more details, please see below:
Big-data frameworks:
Hadoop is essentially a distributed data infrastructure: It distributes massive data collections across multiple nodes within a cluster of commodity servers.
Features:
- Indexes and keeps track of that data
- Enabling big-data processing and analytics
Apache Spark is an open-source cluster-computing framework.
- Spark can interface with other file system including Hadoop Distributed File System (HDFS).
Remark: From technical point of view, Spark is a data-processing tool that operates on those distributed data collections; it doesn’t do distributed storage.
Go to discussion
As of today, more and more business migrated their system application to Cloud platform including SCADA industry. Since SCADA system belongs to energy, food and beverage, manufacturing, oil and gas, Power, Recycling, Transportation, water and waste water. And therefore cyber security news and articles lack of their news. Perhaps we can hear the news is that after nuclear power station encounter hacker or malware attack.
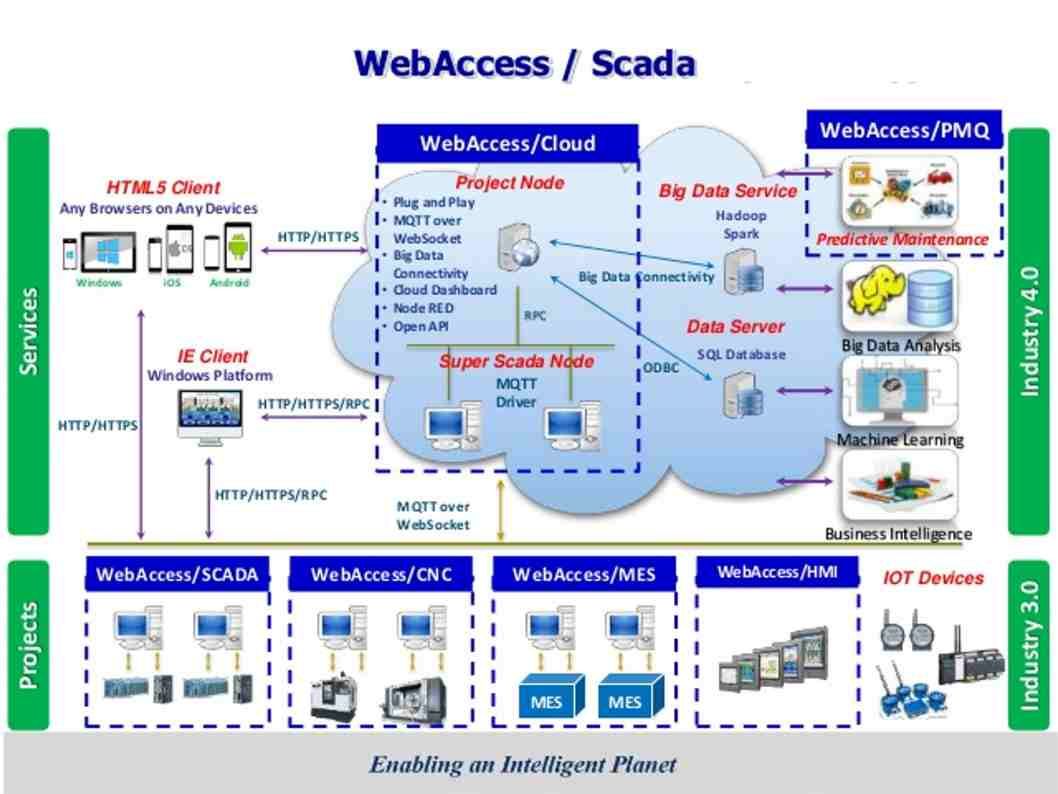
Actually SCADA now expand their user function to mobile device. Even though a mobile phone can do a remote monitoring of the system. With WebAccess, users can build an information management platform and improve the effectiveness of vertical markets (see below picture for reference) development and management.

Let’s think it over, the WebAccess SCADA system involved in energy, aerospace and public facilities control. However those product sound like your IT devices. The SCADA hits vulnerabilities and recorded in CVE database not the 1st time. We know that hundreds of United flights were delayed after the airline experienced a server malfunction on Jul 2015. Lets reader judge by yourself, let review their vulnerabilities found so far. Does it relate to SCADA vulnerability occurs which causes denied of services. Or it is really server malfunction?
Quote: Hundreds of United flights were delayed after the airline experienced a server malfunction on Jul 2015.
Quote: A United spokeswoman said that the glitch was caused by an internal technology issue and not an outside threat or hacker.
Advantech, a leader within the IPC global market. Advantech offers a comprehensive IPC product range that delivers reliability and stability for extreme environments, providing its customers with a one-stop shopping experience implementing Industry 4.0 and fulfilling their Industrial IoT needs. Let’s take a closer look on Advantech scada webaccess products vulnerabilities so far.
The vulnerabilities found on 2014 include an OS command injection, CVE-2014-8387, in the Advantech EKI-6340 series, a stack-based buffer overflow, CVE-2014-8388, in Advantech WebAccess, and a buffer overflow, CVE-2014-8386, in Advantech AdamView, CVE-2014-0770 – Advantech WebAccess SCADA webvact.ocx UserName Buffer Overflow. It looks that the design weakness keeps appear till today! For more details, please refer below details for references.
https://nvd.nist.gov/vuln/detail/CVE-2015-3947
https://nvd.nist.gov/vuln/detail/CVE-2018-5445
https://nvd.nist.gov/vuln/detail/CVE-2018-5443
Our observation in regards to above known vulnerabilities.
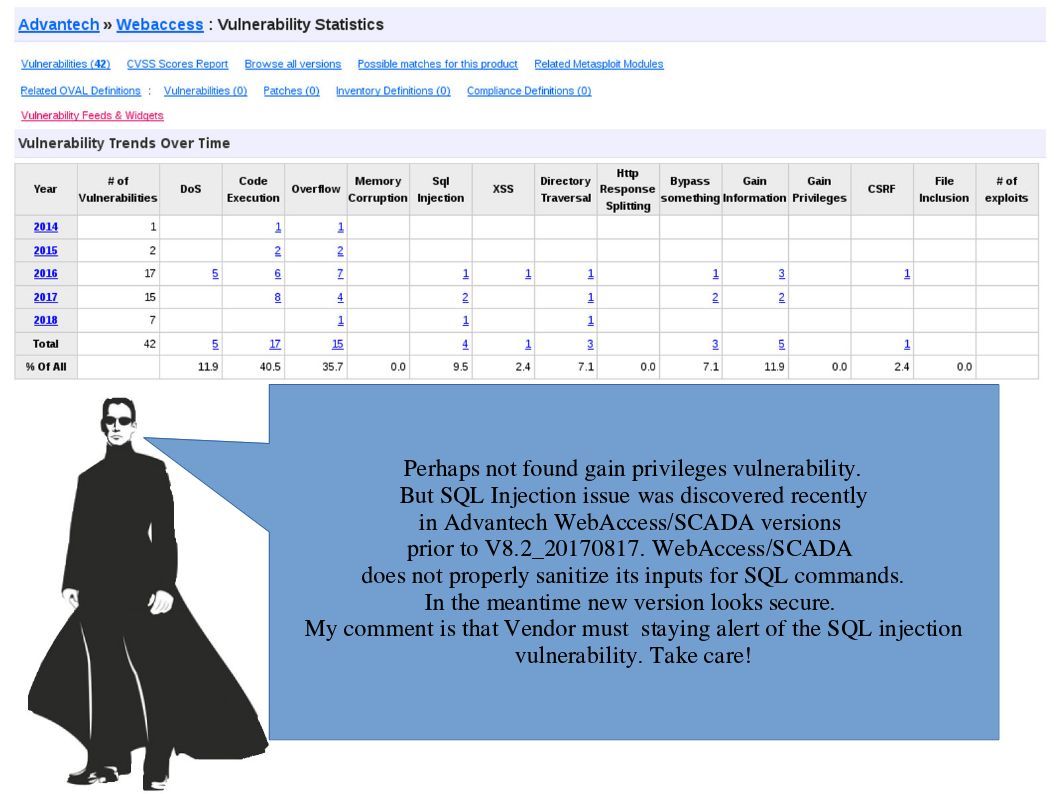
Regarding to WebAccess support specifications. It support the following open real-time data connectivity : OPC, Modbus, BACnet, DDE Server and the following open offline data connectivity: SQL Server, Oracle, MySQL, and Microsoft Access Database. If the repository is the MS SQL server. The IT administrator must staying alert of the SQL injection vulnerability. Since the OS user privilege escalation via Windows Access Token abuse is possible also via SQL injection.
End discussion. Thank you.
Reference:
Information appending on 3rd Feb 2018 – additional technical information supplement. My study on SCADA system risk factors to nuclear facilities (see below):
Potential black force – digitize Godzilla