Preface:
The desire of human being is infinite. It create motivation and innovation. However it embedded greedy and selfishness.
Smart city major domains
In high level point of view, it is easy to interpret smart city major domains. They are Analytics,Transportation,Health & Environment.
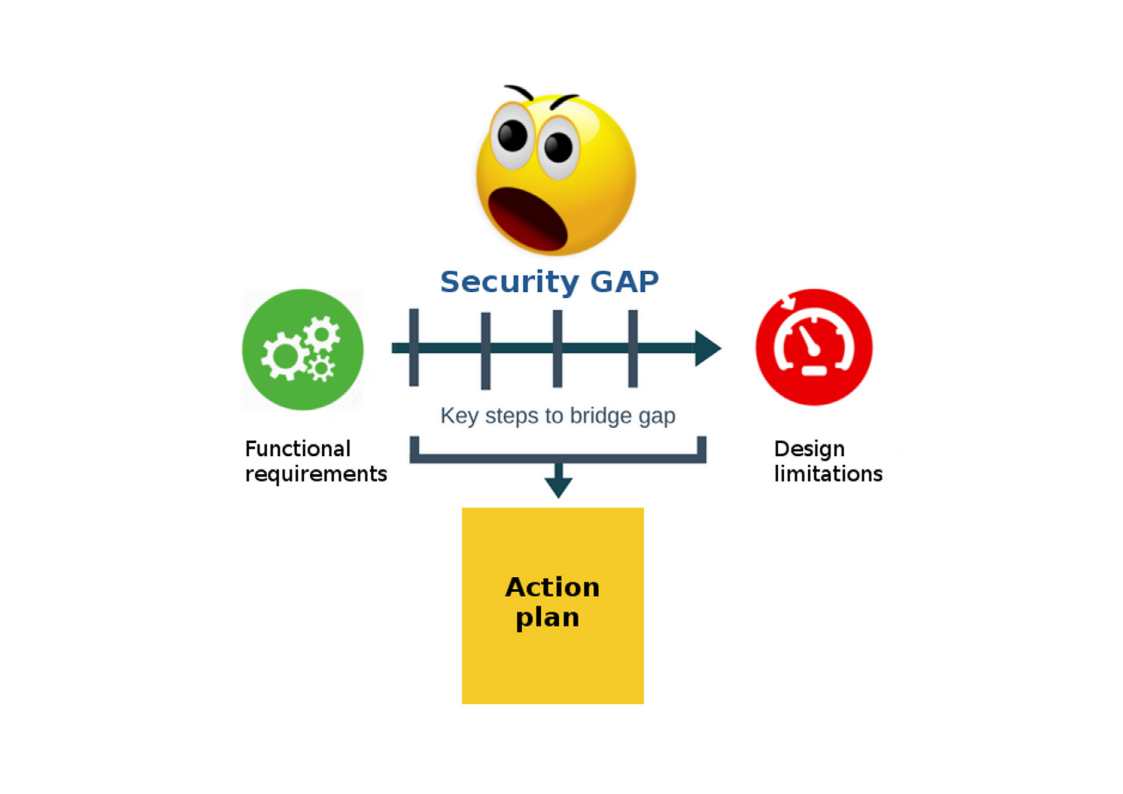
You might ask, where is cyber security? I assumed that cyber security equivalent as a hidden parameter. They will pop up during you conduct a gap analysis (see below diagram for reference).

Who causes security gap?
When functional requirements hits design limitation, you can set out strategic solution conduct the remedy, along with a time frame for meeting those objectives.
However the unknown parameters will impact business decisions because of their expectation and budget concerns. As a result, the technology and cyber security gap will carry forward with development cycle.
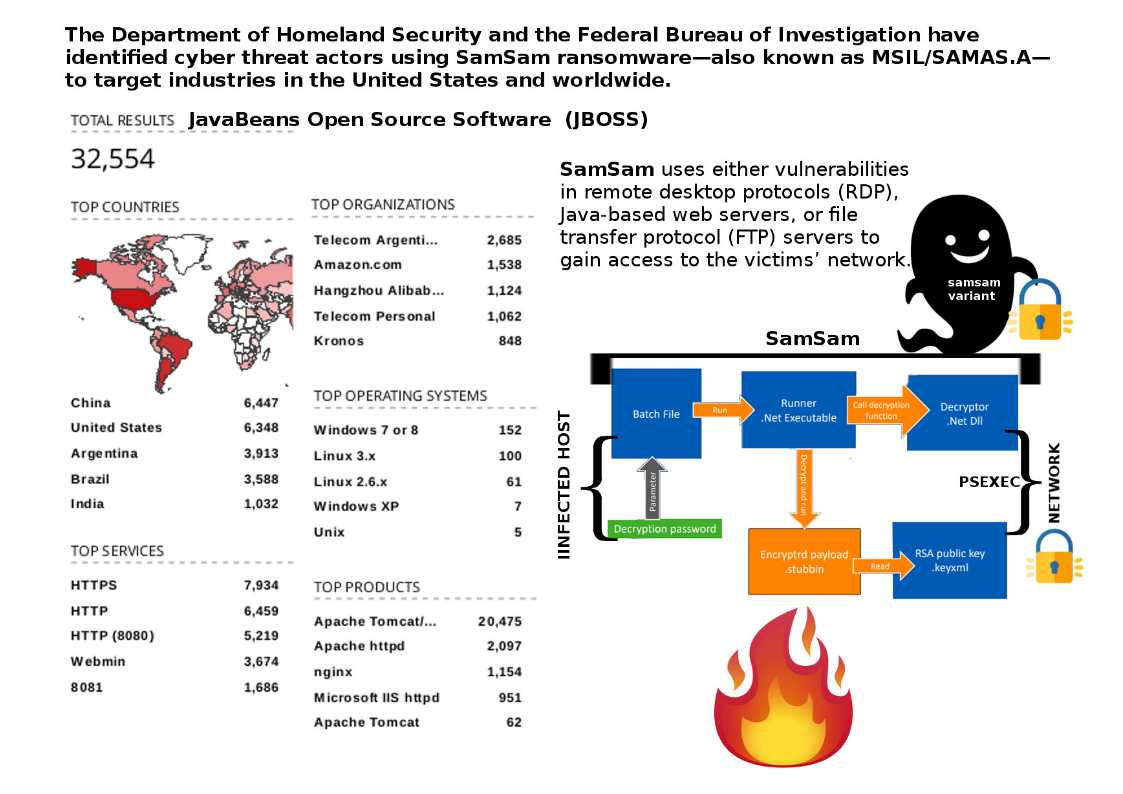
A study from Hewlett Packard in 2016 concluded that 70 percent of IoT devices contain serious vulnerabilities.
The IoT devices and smart city relationship
IoT involves adding internet connectivity to a system of interrelated computing devices, mechanical and digital machines, objects, animals and/or people. The Internet of Things (IoT) form a bridge in between human and machine. As of today, key terms so called ECO system explicitly describe above mechanism. The key technology behind the success of smart city initiatives is the IoT devices. Thereby IoT devices similar an organ inside the human body. The communication in between IoT devices and IoT ECO system like human blood vessel. So, if the smart city infrastructure characteristics like human. And therefore it is hard to avoid sick and illness.
IoT security
When a electronic device has ability for external communications. A specific TCP or UDP port will operate in listen state. The traditional best practice will deploying Firewall and antivirus software. Since IoT devices OS footprint is small. For example a webcam, even though the manufacturer want to install a defense mechanism. However the design limitation restrict or without space. It could not fulfill the requirement. So IoT devices are the top attack target by cyber criminals. As we know, a so called botnet army will be control by attacker command and control server remotely.
For my observation by far, the IoT security awareness was alerted by security researcher since 2010 (see below diagram for reference).
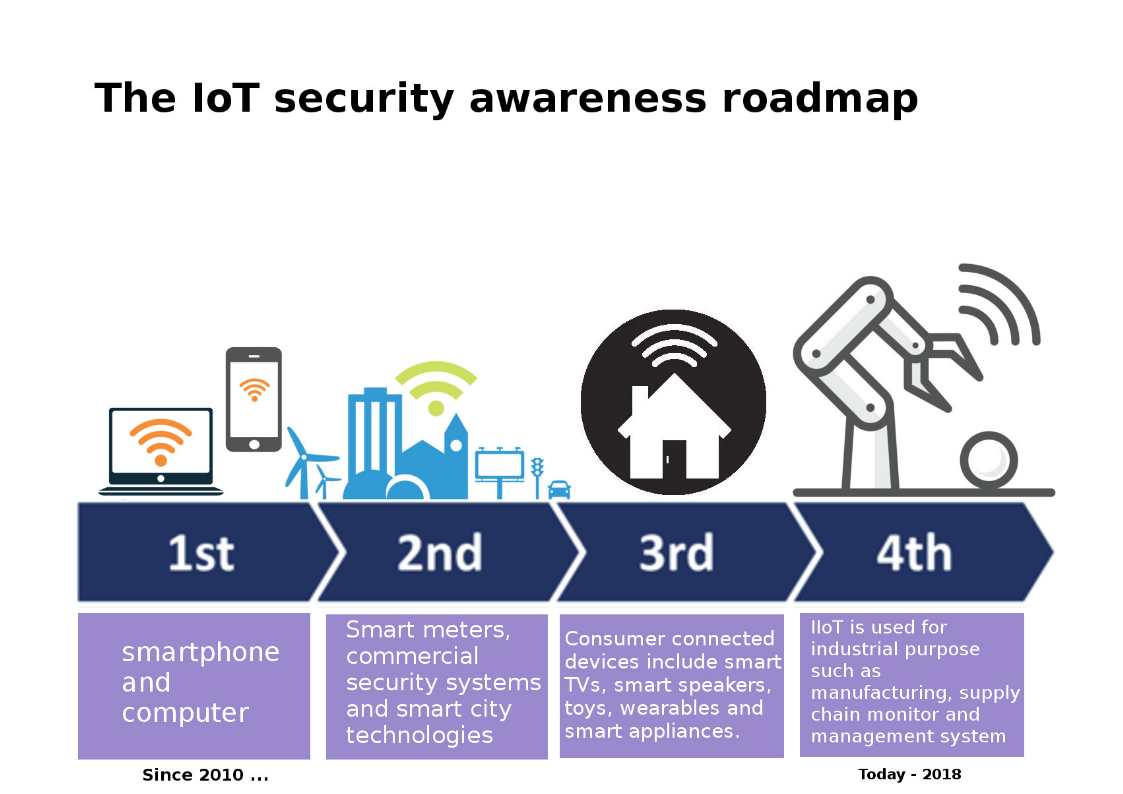
Perhaps the product development and business trend run in fast way. The smart city and artificial intelligence boots up the growth. As of today, IoT devices implementation covered all around the world. Moreover IoT device owner learn from practice in result reduced the cyber attack hit rate. For instance do the patch management. But due to on demand business economic model (multi vendor, without common standard). It has difficult to sharpen the preventive and detective control in IoT world.
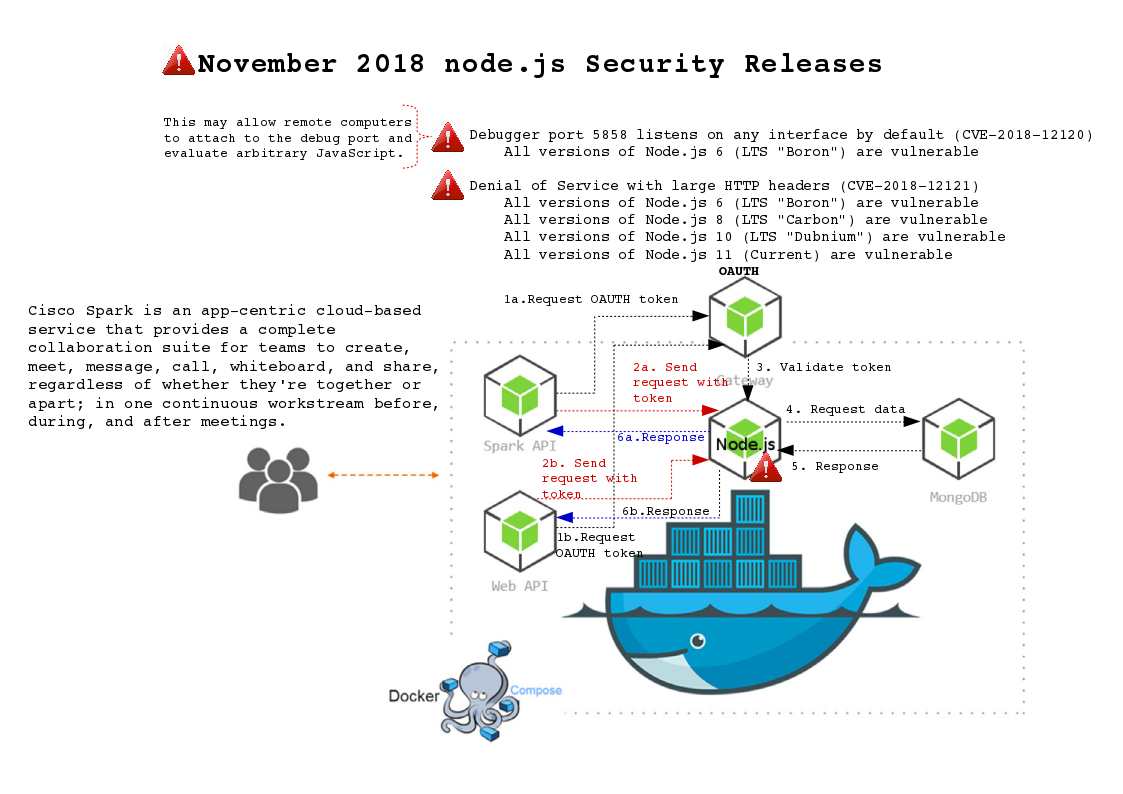
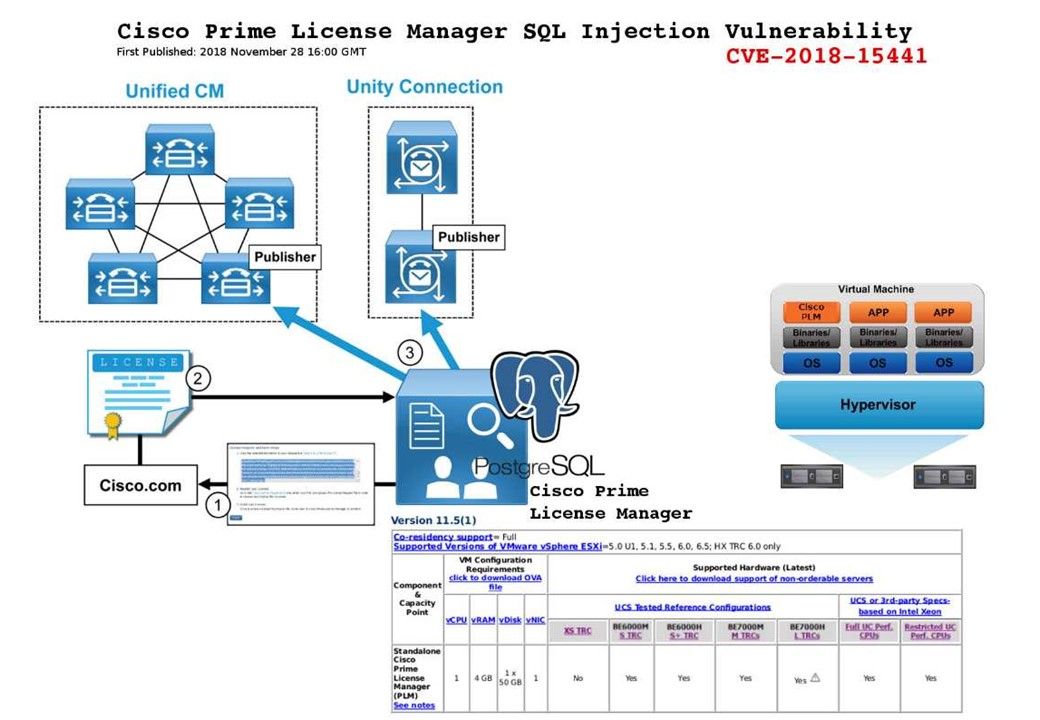
IoT now transform to 4th generation (IIoT). The Industrial Internet of Things (IIoT) or Industry 4.0 refers to interconnected sensors, instruments, and other devices networked together with computers’ industrial applications. The IIoT manufacturer especially SCADA system keen to partnership with famous antivirus vendor. For instance Siemens electronic in high priority installed Trend Micro antivirus products. However the fundamental design of SCADA systems did not focus cyber security . In light of that, on Aug 2018, the Internet Society’s Internet Engineering Task Force is working on IoT standards in areas including authentication and authorization, cryptography for IoT use cases and device life cycle management. Do you think the plethora of IoT security standards could make it difficult for a global IoT standard to emerge?
Internet of Things Embedded Operating Systems is Bad News for the Safety
IoT devices tend to use a type called RTOS, which officially is short for Real-Time Operating System. Unofficially it stands for Not-a-Full-Featured Operating System.
Below diagram bring an idea to you for reference. The Smart TVs, new generation of washing machines, Smart doorbells, Artifical intelligence lawn sprinkler systems, CCTV cameras, smart meter, motion, humidity and temprature sensor and webcam has embedded OS installed. Above IoT devices are capable for WiFi or TCP/IP connection protocol function. TCP protocol integrate to electonic devices was the best of times. But it was the worst of times since it will encountered vulnerability and Zero day attack. But it was the age of wisdom!

FreeRTOS – A real-time operating system microkernel has been developed by chip companies for over 15 years. As of today, IoT industry especially webcam, Smart home devices are deploy this operating system. But serious security flaws in FreeRTOS. The most recent known vulnerabilities are shown as below:
Remote code execution vulnerabilities: CVE-2018-16522, CVE-2018-16525, CVE-2018-16526, CVE-2018-16528.
Denial of service: CVE-2018-16523
Design flaw allow information disclosure: CVE-2018-16524, CVE-2018-16527, CVE-2018-16599, CVE-2018-16600, CVE-2018-16601, CVE-2018-16602, and CVE-2018-16603
Smart city open data platform
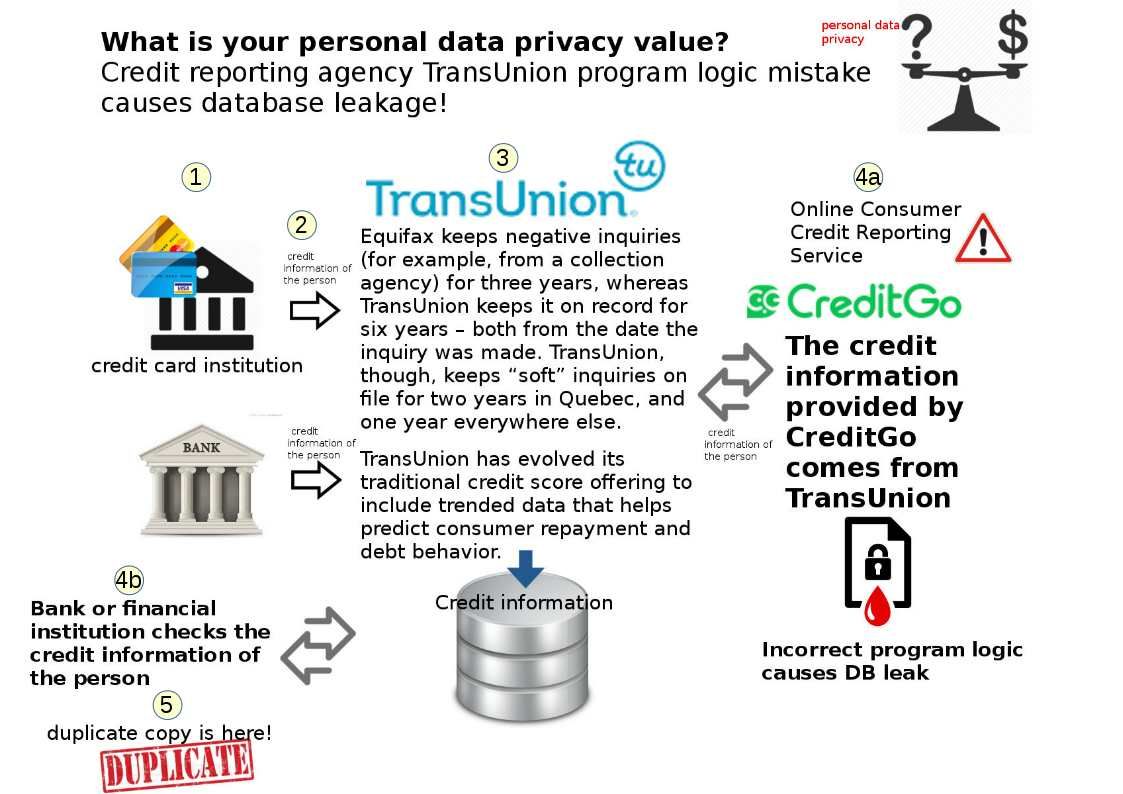
Basically Open data is just that – open. The baseline definition is anyone can access, share and use it free of charge to better connect and interact with their cities. Applications include real-time bus timetables, weather report and public safety information sharing initiatives. Basically Open data is just that – open. The baseline defintion is anyone can access, share and use it free of charge to better connect and interact with their cities. Applications include real-time bus timetables, weather report and public safty information sharing initiatives. But the open data platform not limit above data criteria. So it make people including myself has personal data privacy concerns.
It was the worst of times since it make people concerning personal data privacy . But it was the age of wisdom!
In New York City, open data is law, rather than just a policy. In order to driven the development of smart city. The Domain knowledge expert has the following recommendations.
https://www.scmp.com/comment/insight-opinion/article/2127946/new-york-shows-open-data-key-smart-traffic-solutions
Summary:
Who hinder smart city development? We can say it is the technology limitation and personal data privacy concerns. Whether it was the worst of times on these matters . But it was the age of wisdom!
Reference:
What is a smart city from an security point of view?