Preface:
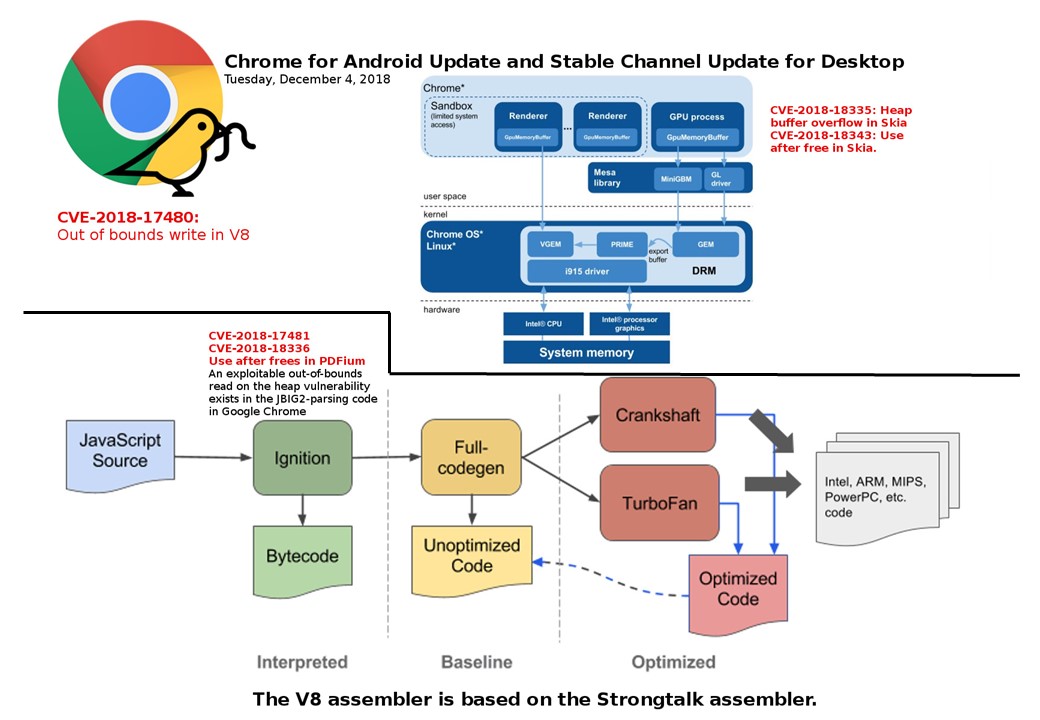
Remote code execute and Privileges escalation are the critical vulnerabilities topics which lure end user attentions. On patch Tuesday (remedy program) issued by Microsoft this week. Their product design limitation contains priviliges escalation vulnerability.
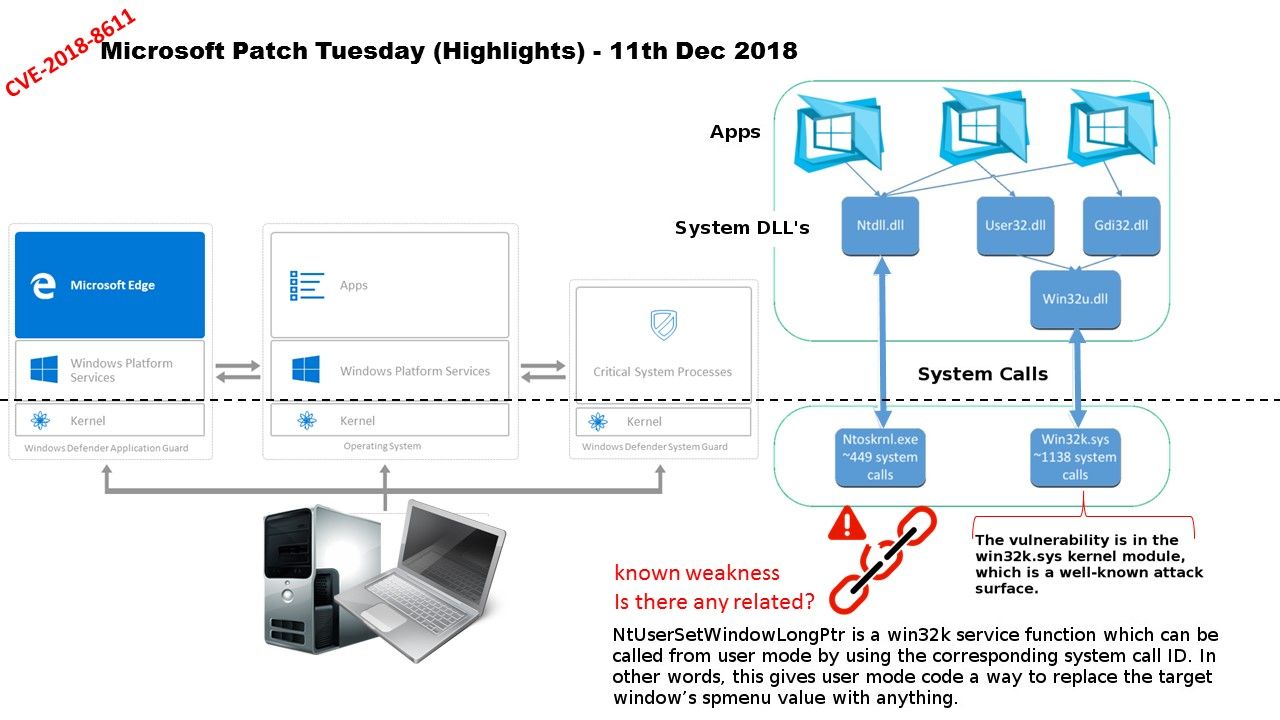
CVE-2018-8611 – Vulnerability details:
With reference of CVE-2018-8611 inform customer that exploit this vulnerability, an attacker would first have to log on to the system. An attacker could then run a specially crafted application to take control of an affected system.
Technical background:
So far, the the win32k.sys kernel module is a well-known attack surface. The function NtUserSetWindowLongPtr replaces the target window’s spmenu field with the function’s argument without any checks when using GWLP_ID and the target window’s style is WS_CHILD.
NtUserSetWindowLongPtr is a win32k service function which can be called from user mode (use the corresponding system call ID).
In the nutshell, this gives a way to attacker to replace the target window’s spmenu value to anything.
Microsoft remedy:
https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2018-8611