Because many industries requires monitoring and control capabilities that SCADA offers. In most uses, SCADA is used to manage a physical process of Electric, Gas and water Utilities.We heard cyber security alert in SCADA facilities so far. As a citizen we cannot immagine how worst will be the incident happened. For instance once SCADA PLC compromised by hacker (malware).
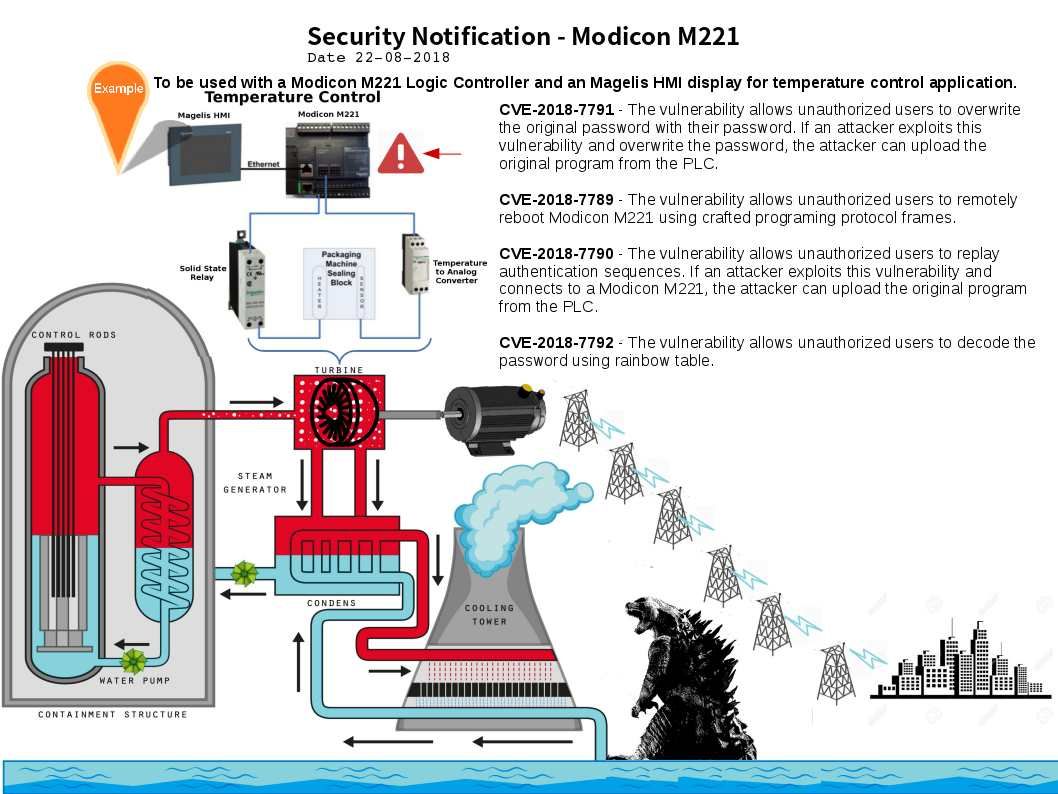
Coolant in a nuclear reactor is used to remove heat generated from it. It flushes out heat to electrical generators and environment. But how to monitor the temperature. Deploy Schneider M221 can conduct the Electric Temperature Control.
On end of Aug 2018, vendor found design weakness on Modicon M221. For more details, please refer below URL.
https://www.schneider-electric.com/en/download/document/SEVD-2018-235-01/