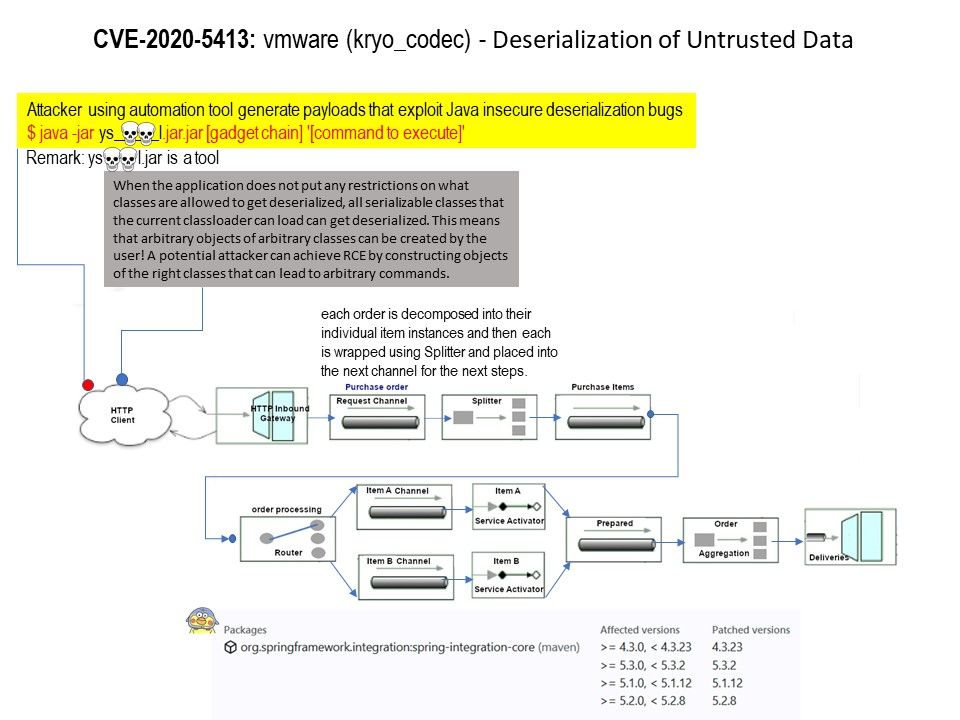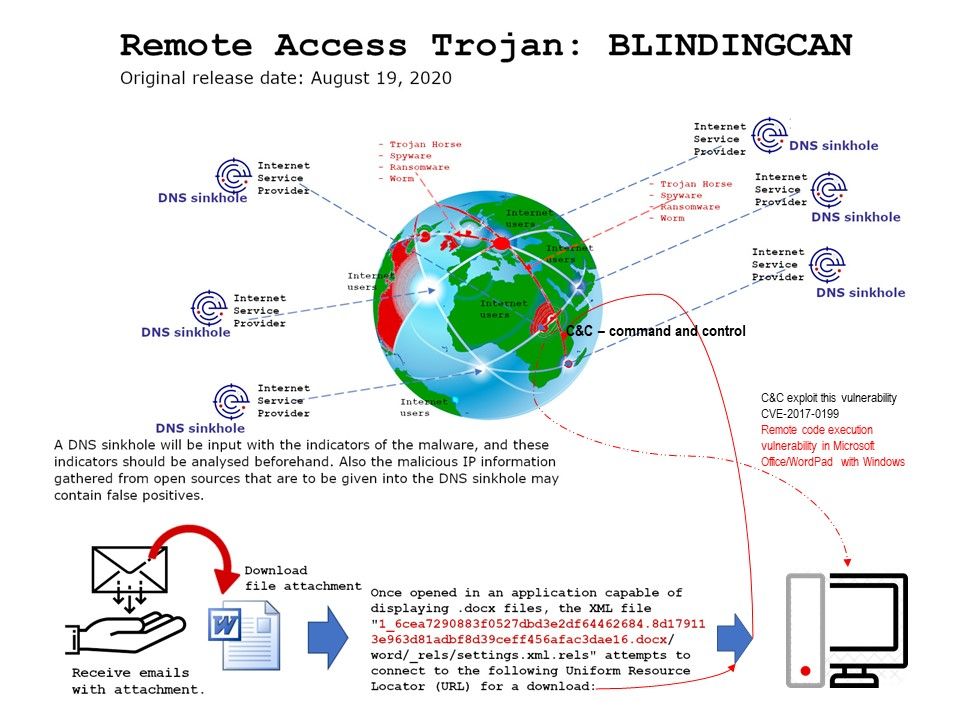
Preface: The Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have identified a malware variant—referred to as BLINDINGCAN—used by North Korean actors.
Techincal details: Perhaps the official report already provide the details. In short, the key point is that APT group exploit the Microsoft Word vulnerability (CVE-2017-0199). As such, APT attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. The report described that malware will download [.]dll file from C&C server. The aim is to replace the local workstation iconcache[.]dll. Replace the iconcache[.]dll require privileges access right. So the specifics attack is targeting the machine which do not have patch installed. If it is successful. The unpack iconcache[.]dll will be transformed a variant of Hidden Cobra RAT.
Official announcement: https://us-cert.cisa.gov/ncas/analysis-reports/ar20-232a
Recommendation: Check your MS office Patch – https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2017-0199
Reference: Perhaps you have doubt that why do the cyber security organization aware the cyber attack in earlier phase. Does it a conspricy? They do a sniffing of your traffic? Or doing surveillance?
No. they have several ways to protect the internet world. For example, relies on DNS Sink Hole activity record in service provider side, cyber crime activities reporting by computer users. Or, through alerts issued by law enforcement agencies, alerting of special types of cyber attacks from hostile entities.
.jpg?width=1920&height=1080&fit=bounds)
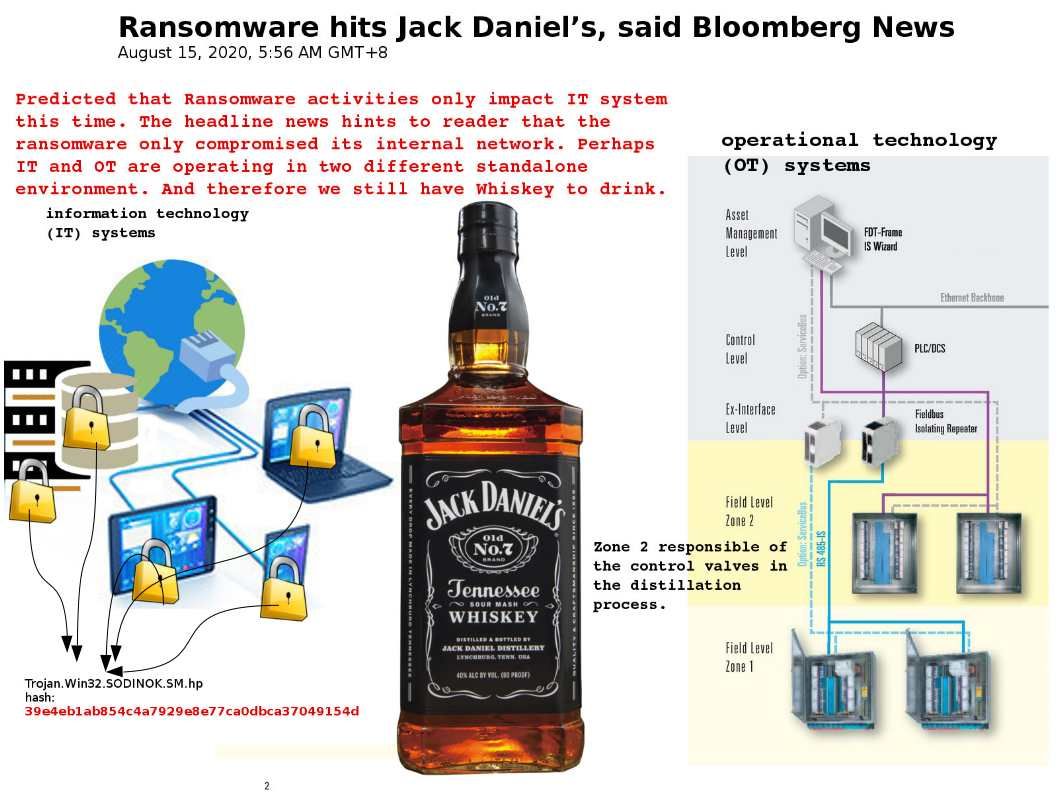
.jpg?width=1920&height=1080&fit=bounds)
.jpg?width=1920&height=1080&fit=bounds)