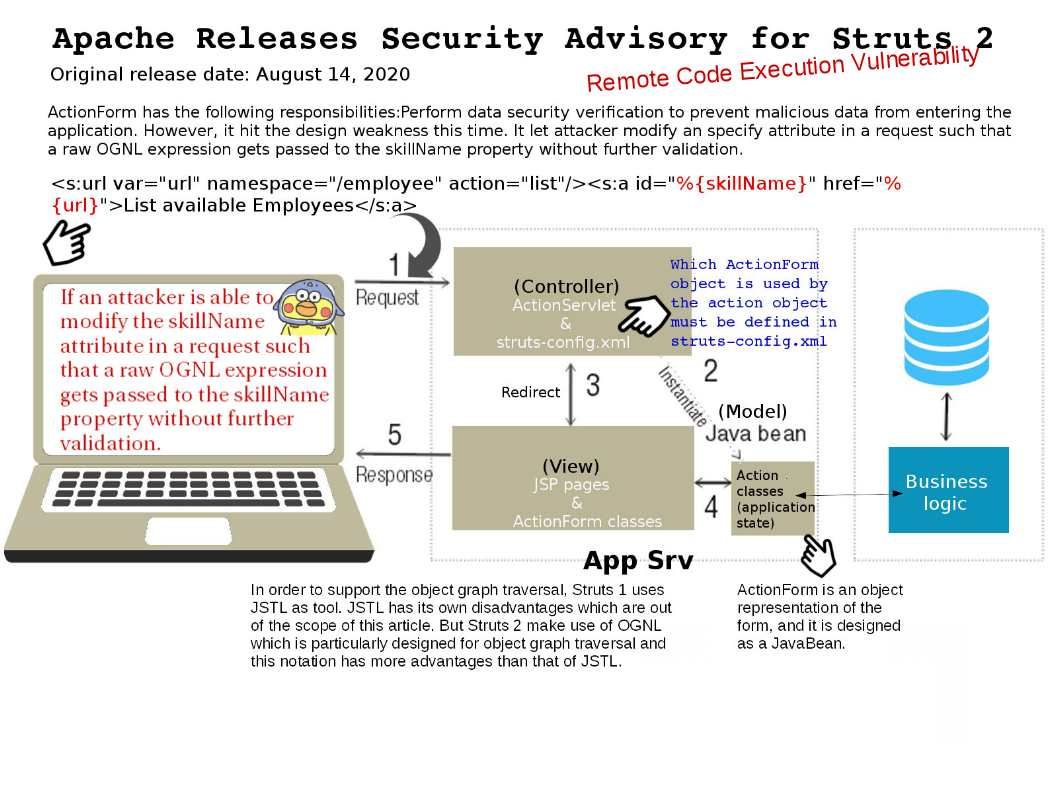
Preface: Struts2 OGNL is the expression language. OGNL is tightly coupled in Struts2 and used to store form parameters as java bean variables in ValueStack and to retrieve the values from ValueStack in result pages. ActionForm has the following responsibilities:Perform data security verification to prevent malicious data from entering the application.
Vulnerability details: However, it hit the design weakness this time. It let attacker modify an specify attribute (skillName) in a request such that a raw OGNL expression gets passed to the skillName property without further validation.
Remedy: upgrading to Struts 2.5.22
Official recommendation: Don’t use forced evaluation of an attribute other than value using %{…} or ${…} syntax unless really needed for a valid use-case.
Recommendation (2): It is recommend to install the application firewall to enhance the preventive control. It can reduce opportunity let hacker conduct the OGNL expression injection attacks.