Preface: The main advantage of object storage is that you can group devices into large storage pools, and distribute those pools across multiple locations.
Background: Object storage is a technology that manages data as objects. All data is stored in one large repository which may be distributed across multiple physical storage devices, instead of being divided into files or folders. An “object” includes the data itself, some metadata, and a unique identifier. This data can be immediately accessed through APIs or http/https. In this way, the object storage safeguards the data. This data can also be replicated to multiple datacenters if needed.
MinIO offers high-performance, S3 compatible object storage. Native to Kubernetes, MinIO is the only object storage suite available on every public cloud, every Kubernetes distribution, the private cloud and the
edge. MinIO is software-defined and is 100% open source under GNU AGPL v3.
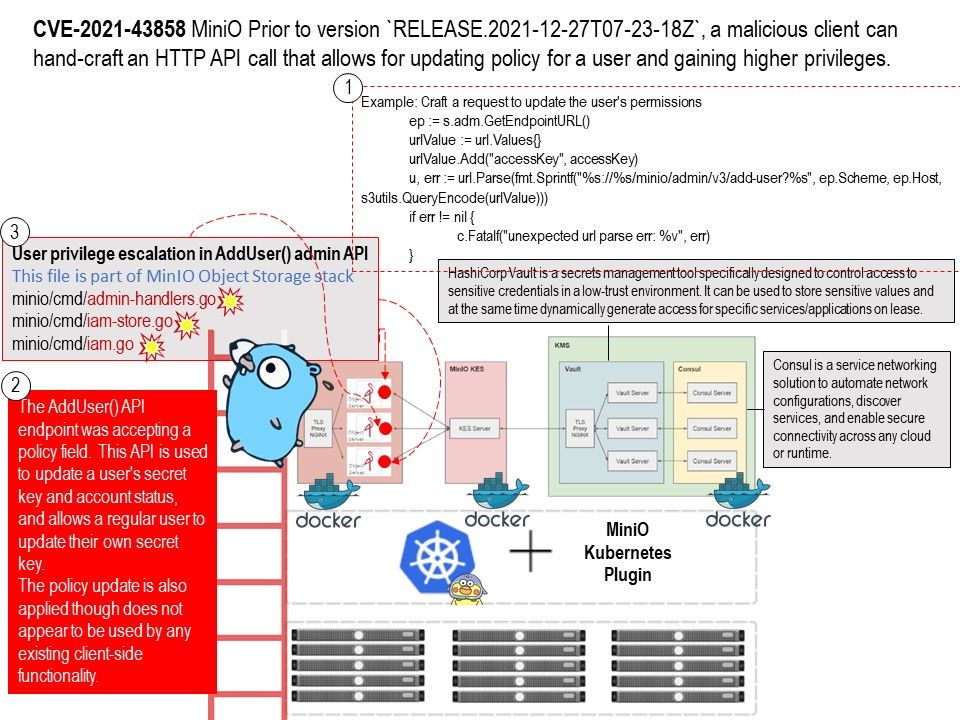
Vulnerability details: The user create API endpoint was accepting a policy field. This API is used to update a user’s secret key and account status, and allows a regular user to update their own secret key. The policy update is also applied though does not appear to be used by any existing client side functionality.
Workaround: Changing passwords can be disabled as a workaround for this issue by adding an explicit “Deny” rule to disable the API
for users.
Remedy: Users are advised to upgrade to RELEASE.2021-12-27T07-23-18Z – https://github.com/minio/minio/releases/tag/RELEASE.2021-12-27T07-23-18Z