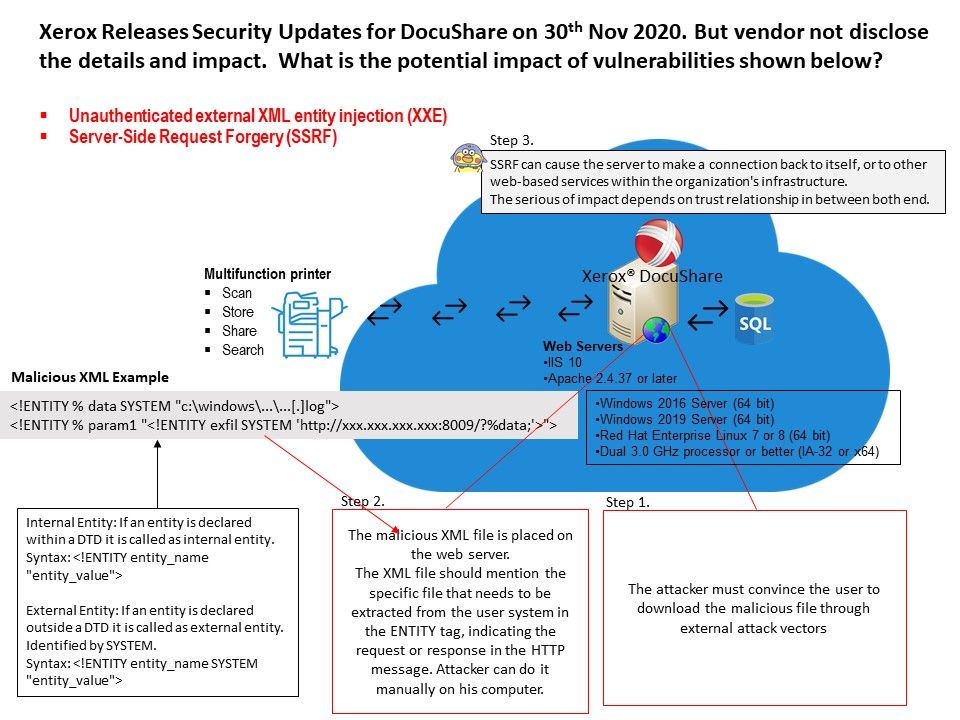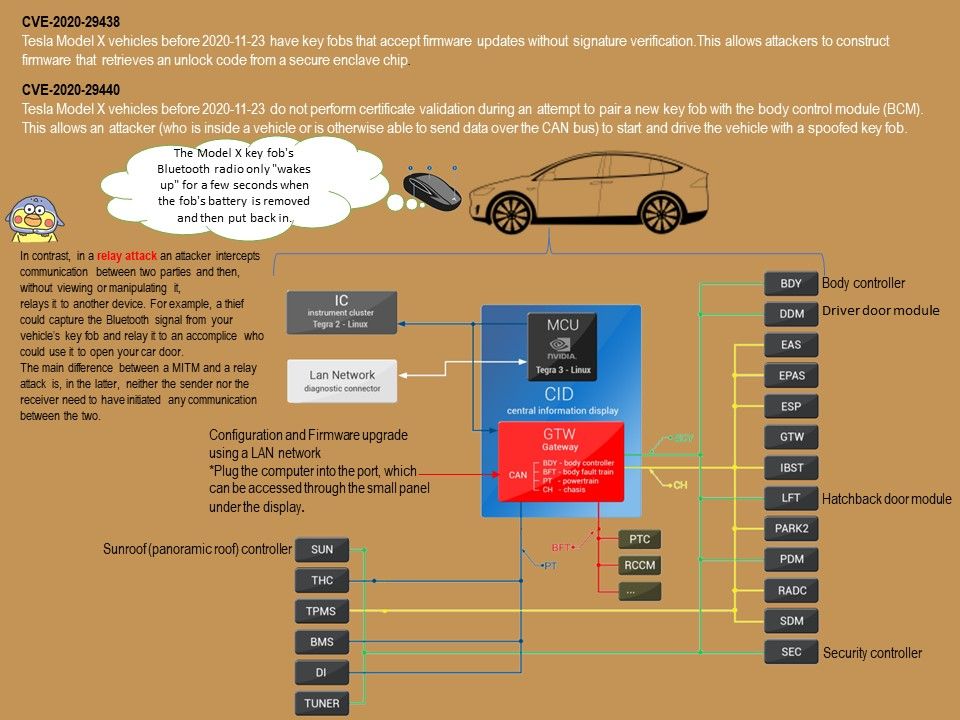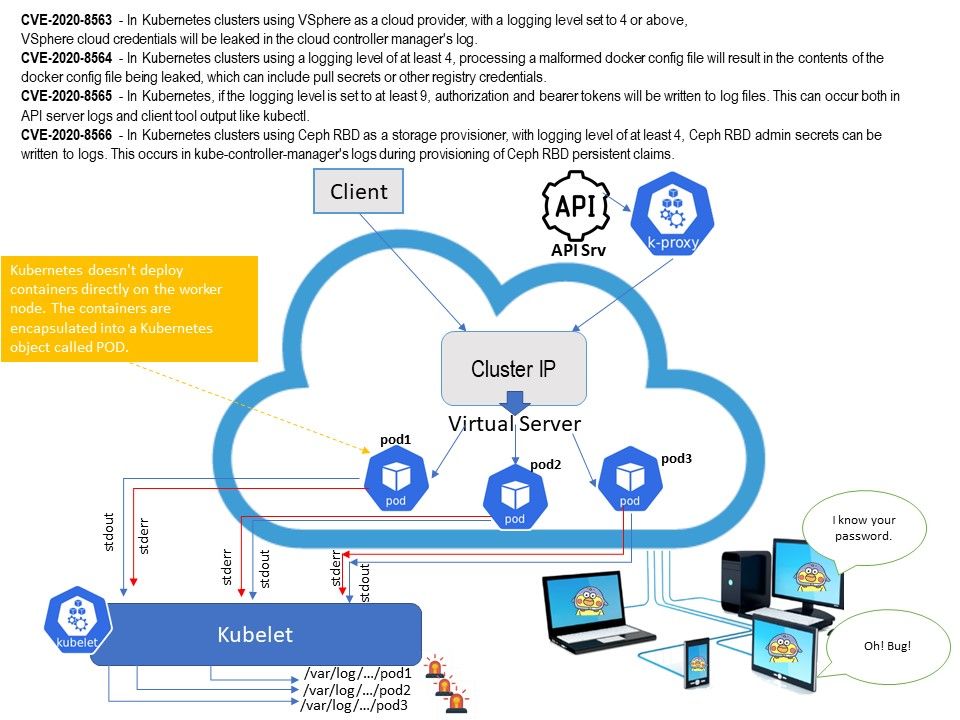
Preface: If you don’t see much useful in the logs, you could try turning on verbose logging on the Kubernetes component you suspect has a problem using –v or –vmodule, to at least level 4.
Technical background: The cluster-level logging in Kubernetes is that Kubernetes has no native cluster-level logging. There are a few proven methods that can be applied cluster-wide to provide the same effective result of all the logs being collected in a standardized way and sent to a central location. The common way are :Node Logging Agent,Monitoring Kubernetes Pods & Monitoring Applications Running in Kubernetes. Perhaps it is comprehensive. Meanwhile, it encountered sensitive information leakage. Cope with technology world, Kubernetes cluster will do a lot of system integration or thin provisioning. For example: use Ceph product services. So when design weakness occurs, sensitive information will be found here.
Ref: A RADOS Block Device (RBD) is software that facilitates the storage of block-based data in the open source Ceph distributed storage system.
Vulnerability details:
CVE-2020-8563 – https://nvd.nist.gov/vuln/detail/CVE-2020-8563
CVE-2020-8564 – https://nvd.nist.gov/vuln/detail/CVE-2020-8564
CVE-2020-8565 – https://nvd.nist.gov/vuln/detail/CVE-2020-8565
CVE-2020-8566 – https://nvd.nist.gov/vuln/detail/CVE-2020-8566
Comment: The management of log files is merged into ISMS. Therefore, the impact depends on this area.
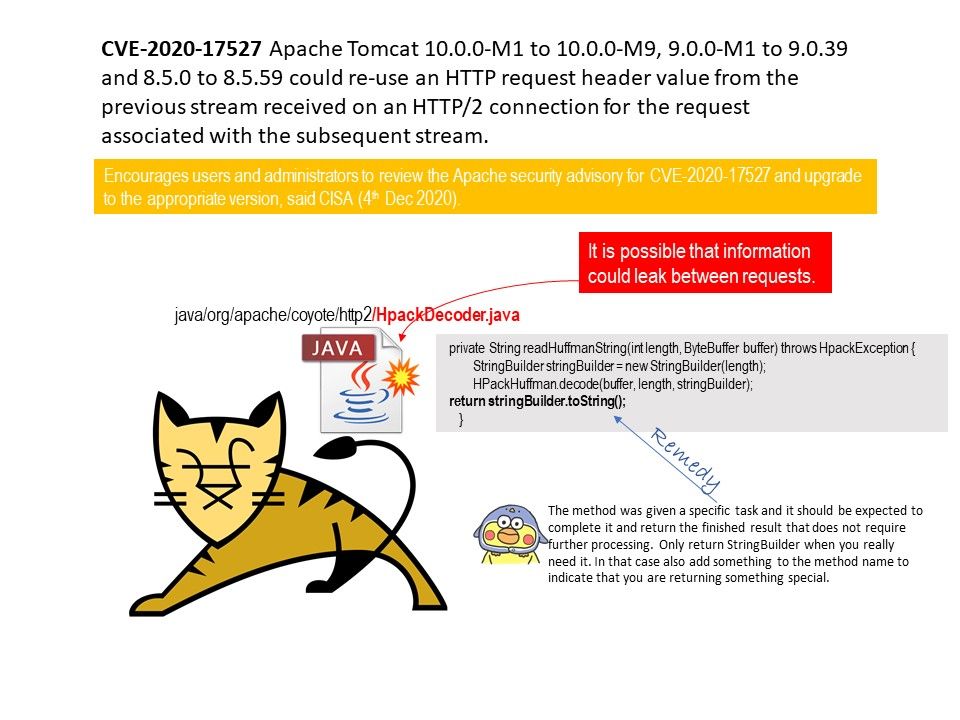
.jpg?width=1920&height=1080&fit=bounds)