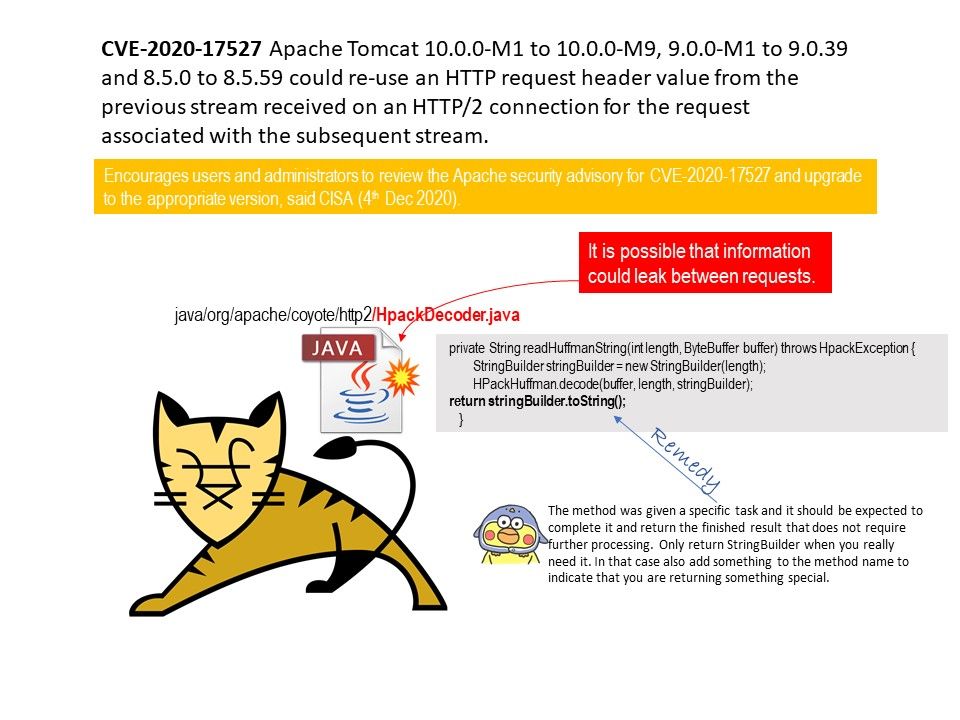
Preface: We encourages users and administrators to review the Apache security advisory for CVE-2020-17527 and upgrade to the appropriate version, said CISA (4th Dec 2020).
Vulnerability details: With known HTTP/2 Protocol practice, HTTP headers are compressed using a combination of compression schemes (static Huffman coding and context adaptive coding). Flow control and dependency mechanisms that allow HTTP/2 clients and servers to signal how to transmit object. However, a design weakness was found in Apache Tomcat. The fault is that it allow to re-use an HTTP request header value from the previous stream received on an HTTP/2 connection for the request associated with the subsequent stream.
This design limitation will causes error and closure of the HTTP/2 connection. Whereby, it is possible that information could leak between requests.
Remedy: The method was given a specific task and it should be expected to complete it and return the finished result that does not require further processing. Only return StringBuilder when you really need it. In that case also add something to the method name to indicate that you are returning something special. For more detail, please refer to diagram.
Mitigation:
Upgrade to Apache Tomcat 10.0.0-M10 or later
Upgrade to Apache Tomcat 9.0.40 or later
Upgrade to Apache Tomcat 8.5.60 or later