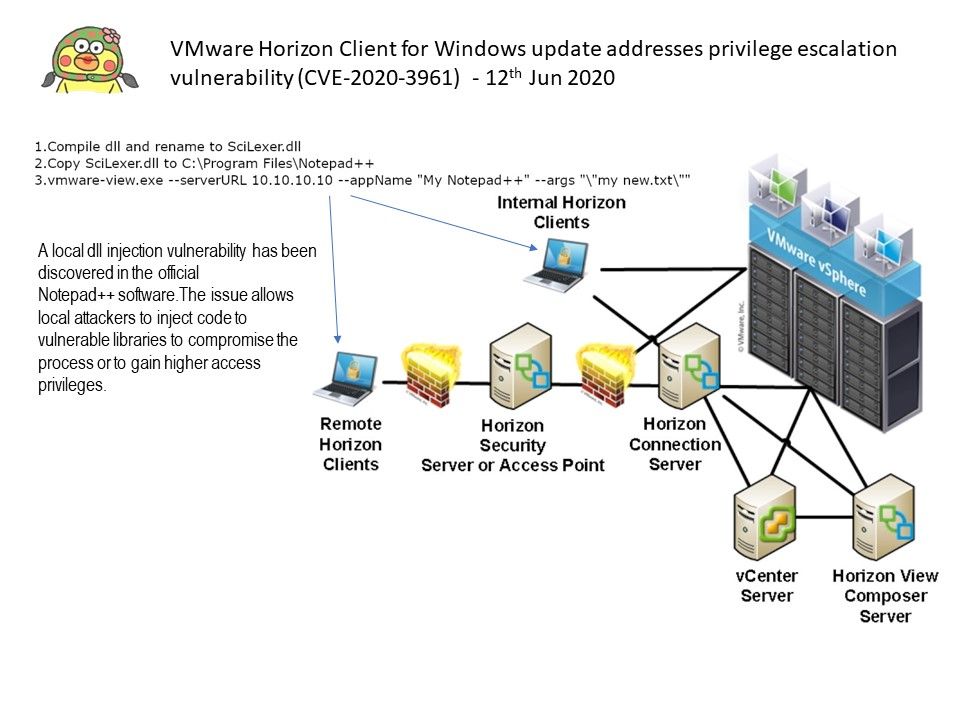
Preface: In order to avoid the impact of the vulnerability. VMware do not provide the details for CVE-2020-3961.
Synopsis: This vulnerability can be exploited locally. The attacker should have authentication credentials and successfully authenticate on the system.
Vulnerability details: VMware Horizon Client for Windows contains a privilege escalation vulnerability due to folder permission configuration and unsafe loading of libraries.
My observation: Perhaps the idea displayed on attached diagram may also have the way to do the same thing.
Reference: A local dll injection vulnerability has been discovered in the official Notepad++ software.The issue allows local attackers to inject code to vulnerable libraries to compromise the process or to gain higher access privileges.
Official announcement – please refer following link https://www.vmware.com/security/advisories/VMSA-2020-0013.html